Financial Services face threats such as ransomware, data breaches and vulnerabilities from remote workforces. Solutions include access management, endpoint security, SD-WAN, FWaaS and compliance tools. |

Cyberattacks are on the rise, and the costs and impacts of ransomware, data breaches, and other cyberattack campaigns continue to grow. The combination of growing cybersecurity risk and expanding regulatory requirements makes it vital for financial services organisations to implement security strategies that effectively protect their systems and the data entrusted to them against modern cyber threats.
Table of Contents
However, with the wide variety of tools and services available, it can be difficult to determine which can provide real value to the organisation. When evaluating potential cybersecurity solutions, it is important to consider how they address the risks and security threats that financial services face today and in the future.
What are the top Cybersecurity Challenges of Financial Services Organisations?
Due to the volume, value, and sensitivity of the data in their possession, financial services organisations are a primary target of cyberattacks. Financial institutions face various security challenges, including the following:
Ransomware
Ransomware has become a top-of-mind security concern for any organisation. Ransomware attacks are surging in recent years, and the costs of a ransomware attack are growing. For financial services, the average cost of remediating a ransomware attack is $2.1 million.
While any organisation can be the victim of a ransomware attack, financial services are a leading target. According to a study by Nordlocker, finance ranked in the top three for ransomware attacks in 2021 behind construction and manufacturing.
Data Breaches
Data breaches are another leading and costly threat to financial services. According to the 2021 Cost of a Data Breach Report, a data breach in the financial sector costs an average of $5.72 million, ranking second behind the healthcare industry. As a highly-regulated industry, the financial sector has a high cost and impact of breaches. Financial organisations are entrusted with large amounts of sensitive data that must be protected in accordance with the requirements of a complex patchwork of regulations.
Digital Transformation
Many financial services companies have strategies in place for digital transformation and the adoption of next-generation technologies. For example, many organisations have or plan to transition IT resources to cloud infrastructure. With these changes to corporate IT environments come cybersecurity challenges and risks. Cloud deployments operate under the shared responsibility model, and taking full advantage of the benefits of the cloud by moving to serverless and containerised applications requires new approaches to security. Making the move to the cloud while maintaining data security and regulatory compliance can be a challenge, as demonstrated by the massive number of cloud data breaches that occur each year.
Remote Work
The COVID-19 pandemic had a significant impact on how many businesses conduct business. In the wake of the pandemic, many companies are looking to extend their telework programs, sometimes indefinitely. Remote work creates significant challenges for financial services organisations, especially in the areas of data security and regulatory compliance. As employees access sensitive customer data from home or anywhere, it can be more difficult to prove that they are doing so in a way that complies with applicable regulations. Not only do financial services providers need to ensure that data is properly protected but also that it complies with restrictions on data transfers outside jurisdictional boundaries defined by regulations such as the General Data Protection Regulation (GDPR).
Supply Chain and Third-Party Risk Management
Recent events such as the SolarWinds, Kaseya, and Microsoft Exchange hacks have demonstrated the limitations and complexity of a corporate cybersecurity program. While a business may have strong cybersecurity protection for its own environment, it may be vulnerable to attack via its third-party suppliers, vendors, and other partners. The trend toward open banking makes the financial services industry even more vulnerable to these types of attacks. As financial services organisations extend access to sensitive customer data to third-party service providers, they need the ability to ensure that this data remains secure against unauthorised access and is managed in accordance with applicable regulations.
How Modern Security Solutions Address Financial Services Security Challenges
Financial services face a wide range of cybersecurity risks and challenges. However, solutions exist that provide organisations with key capabilities vital to reducing their cybersecurity risk.
Access Management
Access management is crucial to financial services’ data security and regulatory compliance strategies. Many of the major cyber threats to financial services (such as ransomware and data breaches) exploit compromised credentials and privileged access to achieve their objectives. Additionally, managing access to sensitive customer data is the primary focus of most regulations that impact the financial industry. Financial services organisations can manage access to their data and systems in various ways.
Some of the primary components of an access management strategy include:
- Cloud Application Security Broker (CASB): CASB solutions monitor and manage access to an organisation’s cloud-based applications. As financial services pursue digital transformation and shift core applications to the cloud, CASB solutions are vital to preventing unauthorised access to sensitive customer data.
- Multi-Factor Authentication (MFA): MFA requires a user to use a combination of factors (such as a password and a physical token) to authenticate to an account. MFA is commonly mandated for access to customer financial data by regulations such as the Payment Card Industry Data Security Standard (PCI DSS).
- Privileged Access Management (PAM): 74% of data breaches involve third parties with unnecessary privileged access to a company’s systems and data. As financial services expand third-party relationships due to open banking and digital transformation initiatives, PAM solutions are vital to monitoring and managing accounts with elevated access to sensitive systems and data.
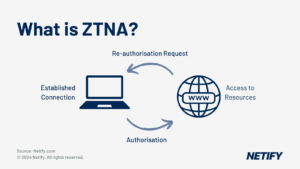
- Zero-Trust Network Access (ZTNA): Telework makes secure remote access solutions necessary as employees remotely access corporate data and systems. ZTNA solutions can enable financial institutions to manage data security risks and regulatory compliance requirements by providing access to data on a case-by-case basis determined by role-based access controls.
Endpoint and User Security
With the rise of remote work, endpoint security is more important than ever for financial institutions. As employees work from home, devices outside the traditional network perimeter have access to sensitive corporate and customer data and enterprise resources. If these devices become infected with malware, an attacker can exploit their remote access to attack the business directly.
Financial services need solutions that enable them to prevent, detect, and respond to potential infections on their employees’ devices. Some applicable cybersecurity solutions include:
- Extended Detection and Response (XDR): As malware and other cyberattacks grow more sophisticated, traditional standalone endpoint security solutions are growing less and less effective. XDR solutions are designed to take a more holistic approach to threat detection and remediation, collecting data from multiple sources (endpoints, email, network traffic, etc.) and analysing it to identify these more subtle attacks.
- Secure Web Gateway (SWG): Many security threats that employees face come over the Internet. Users may accidentally browse to malicious or infected websites or be directed there by phishing emails. SWGs sit between a user and the Internet and proxy all connections, enabling the organisation to block visits to inappropriate or dangerous sites and to monitor for malicious content.
Securing the Distributed Enterprise
As financial institutions embrace remote work and digital transformation initiatives, their IT infrastructure becomes more distributed. This is most obvious in cloud adoption, with 91% of financial services organisations currently using cloud computing or planning to do so within the fiscal year.
The shift from on-prem to the cloud creates security challenges for an organisation as traditional perimeter-based defences are no longer effective. Routing all traffic through the headquarters network for security inspection creates network latency and degrades performance, but allowing traffic to continue to its destination uninspected creates risk and risks regulatory non-compliance
As financial services embrace a more distributed IT infrastructure, they can enhance network performance and security by transitioning to modern security solutions, such as:
- Software-Defined WAN (SD-WAN): SD-WAN is a network optimisation tool designed to identify the best route between SD-WAN points of presence (PoPs) over various network media. This can ensure that latency-sensitive applications have the network performance that they require, and security solutions deployed alongside or integrated with SD-WAN solutions can secure all traffic flowing over the enterprise WAN.
- Firewall as a Service (FWaaS): Like other cloud-hosted, service-based solutions, FWaaS provides financial services with increased flexibility and scalability. FWaaS can be deployed alongside an organisation’s cloud-based applications to protect them and can also be used to provide high-performance and scalable protection to on-prem IT resources.
Threat Detection and Response
Rapid detection and response is vital to minimising the cost and impact associated with a security incident. The longer that an attacker has access to systems, the more opportunity to steal or encrypt valuable data, compromise user credentials, or deploy persistence mechanisms to deepen their hold on the system. Financial services need robust threat detection and response to minimise the cost of cybersecurity incidents and meet regulatory deadlines for breach reporting. To do so, companies require visibility into active threats and security personnel capable of addressing them. The following security solutions can help companies to meet these requirements.
- Security Information and Event Management (SIEM): The average enterprise has 75 security solutions, all of which generate logs and alerts about potential security incidents, overwhelming security analysts with too much data. A SIEM solution aggregates and analyses these logs, using context and multiple data sources to eliminate false positives and draw analysts’ attention to the most significant threats.
- Managed Detection and Response (MDR): A global cybersecurity skills gap makes it difficult for organisations to find the security talent that they need, leaving 61% of security teams understaffed. MDR can help an organisation to fill these gaps by augmenting or replacing in-house security teams with third-party providers with security and compliance expertise.
Designing Security for Compliance
Every organisation has regulatory compliance responsibilities; however, the financial sector is one of the most highly regulated industries. The sensitivity of the data entrusted to financial institutions and the potential for fraud result in additional scrutiny for companies working in the industry.
Different organisations may be subject to various regulations, each with its own requirements and mandatory security controls. Some of the most common regulations that financial services companies will have to consider when designing a security strategy include:
- General Data Protection Regulation (GDPR): The EU’s GDPR is one of the furthest-reaching regulations in existence. Any company processing the data of EU citizens is subject to the GDPR.
- Sarbanes-Oxley (SOX): SOX is a US regulation designed to protect shareholders in public companies. It focuses on corporate transparency to protect against financial fraud.
- Payment Card Industry Data Security Standard (PCI DSS): PCI DSS was developed by the major payment card brands to protect cardholder data. All merchants processing payment card transactions are subject to PCI DSS.
- Bank Secrecy Act (BSA): The BSA is a US regulation also known as the Currency and Foreign Transactions Reporting Act. Its focus is on preventing money laundering and financing terrorism.
- Gramm–Leach–Bliley Act (GLBA): GLBA is a US federal regulation designed to protect customers of financial institutions. Financial services organisations must protect customer data and disclose data sharing with third parties.
- Financial Industry Regulatory Authority (FINRA): FINRA requires US brokers to be registered and licensed. It includes requirements for protecting customer data from exposure and cyber threats. This is not a complete list of financial industry regulations and standards, and the regulatory landscape is changing rapidly. Financial institutions should research applicable regulations and incorporate their requirements into a corporate cybersecurity strategy.
10 Questions to Ask Your SD-WAN and Cybersecurity Vendors and Service Providers
Many cybersecurity solutions and providers are out there, and it can be difficult to determine which are the best for your organisation. Some questions that you can ask to help identify if a potential vendor or service provider is a good fit include:
- Can you provide third-party evaluations and customer testimonials?
- How does your solution integrate with my existing security architecture?
- Does your tool comply with applicable regulatory requirements?
- How does your tool reduce exposure?
- How do your tool’s capabilities map to MITRE ATT&CK, NIST, or other open standards?
- What reporting capabilities does your solution have?
- Where is data stored and how is it protected?
- How often do you distribute updates?
- How quickly are security patches created and distributed?
- What is your process for reporting a security issue?
- Can you provide a third-party security audit report for your products, development environment, etc.?