What is SASE Cybersecurity for the Healthcare Sector?
In the healthcare industry, doctors, nurses, support workers and administration teams all rely on the quality of the network to carry out daily duties and deliver care to patients. SASE (Secure Access Service Edge) solutions offer greater quality network performance and security, ensuring optimal patient care, as well as a better user experience for professionals. SASE improves healthcare networks through its integration of advanced tools such as ZTNA, SWG, CASB and SD-WAN, enabling sensitive patient data to be secured, compliant with strict healthcare regulations and improved network performance. And SASE's growing importance is only emphasised by the growing demand for new healthcare technologies. Healthcare advancements, such as the widespread adoption of telemedicine, IoMT devices, smart equipment and remote services, are all enabled by SASE, with healthcare providers able to deliver these improved technologies in a secure, reliable manner. |
Within the healthcare industry, the demand to enable remote care and mobile workforces is continuously growing, with network administrators not only tasked to provide this availability but also to implement security measures alongside it.
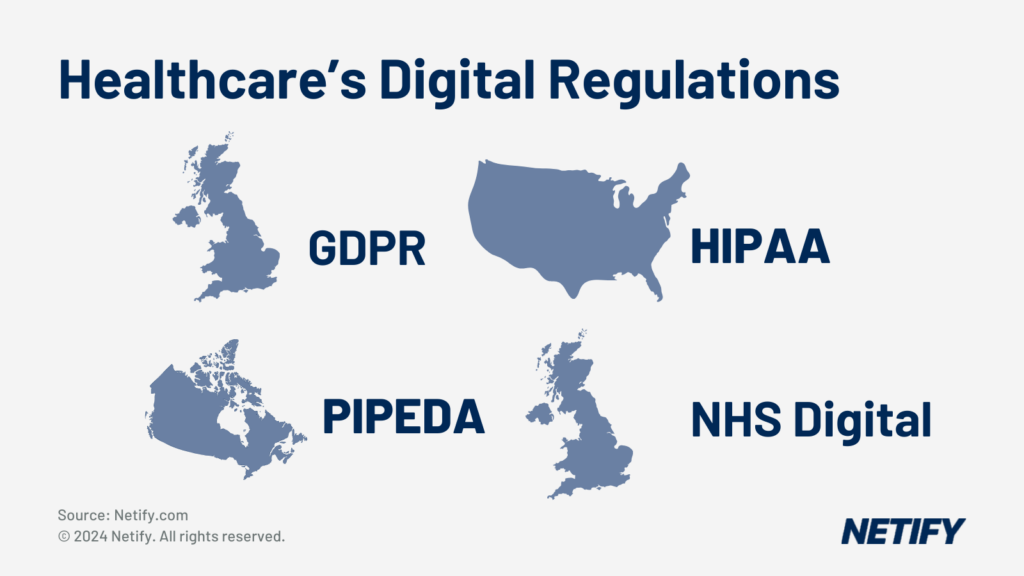
Regulations (such as HIPAA, GDPR, NHS guidelines and PIPEDA) all dictate that healthcare providers must keep sensitive patient information confidential, which can be difficult when care is dispersed across a range of healthcare environments.
Further to this, as healthcare data has become particularly valuable to malicious actors, the requirement to prevent network breaches, care disruptions and health data exfiltration must also be prioritised.
For many network administrators in the healthcare industry, catering the network to fulfill all of these requirements simultaneously can be daunting, however Secure Access Service Edge (SASE) offers the solution. SASE is a cloud-native network architecture that integrates both security and networking improvements into a single unified solution.
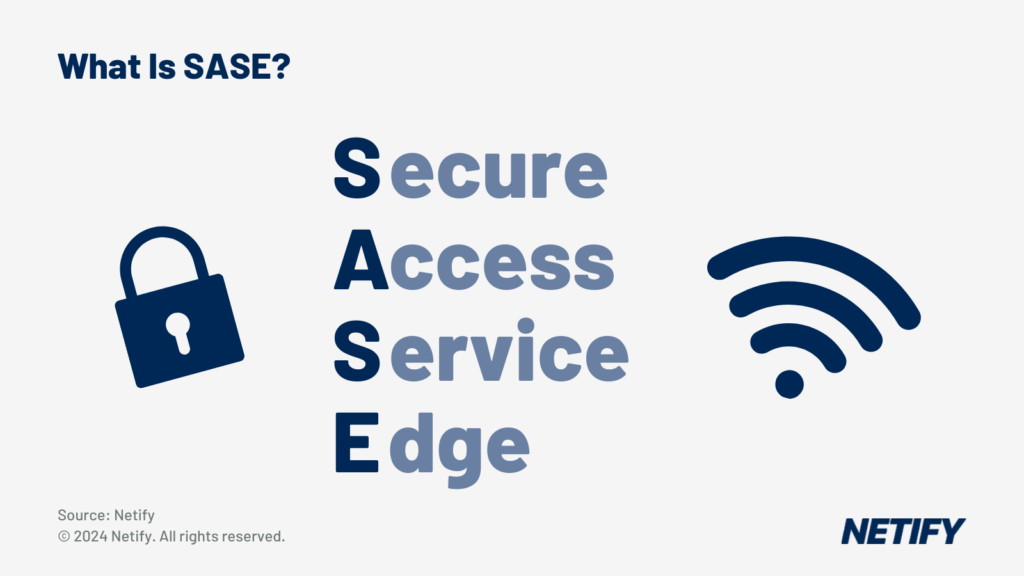
When considering SASE solutions that are specifically designed for healthcare environments, providers can benefit from improved protection for patient data, assurances of compliance with regulations and support for essential services such as telemedicine, Internet of Medical Things (IoMT) connected medical devices and remote healthcare services.
Due to the unique challenges that the healthcare industry experiences with safeguarding sensitive data, maintaining operational efficiency and integrating new medical innovations, SASE is arguably essential in such a highly regulated environment. SASE directly addresses these issues by delivering an all-encompassing solution tailored to the sector's needs.
Related Terms
Successful SD-WAN Deployments in Healthcare
How to choose SD-WAN for Healthcare
SD-WAN & CyberSecurity Providers & Vendors for Healthcare
SD-WAN & CyberSecurity in Healthcare
Top Healthcare Managed Service Providers
10 Questions to Ask When Choosing CyberSecurity for Healthcare
Got a question about SASE CyberSecurity for Healthcare? Contact our experts for advice via email: hyelland@netify.com |
Core Components of SASE for Healthcare
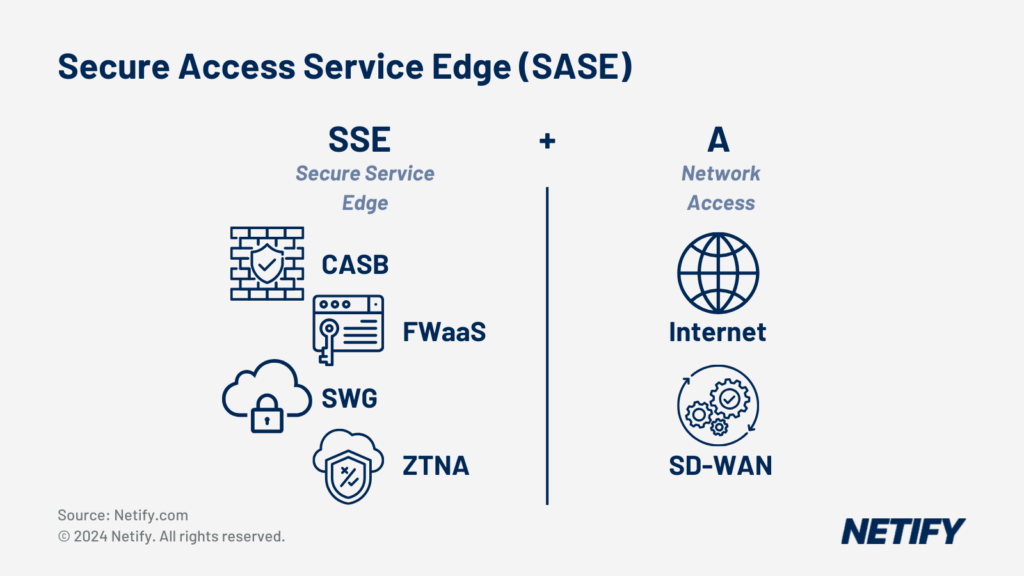
Zero Trust Network Access (ZTNA):
Zero Trust Network Access (ZTNA) is an architecture primarily designed to ensure that professionals have to continuously verify their identity in order to gain access to network resources.
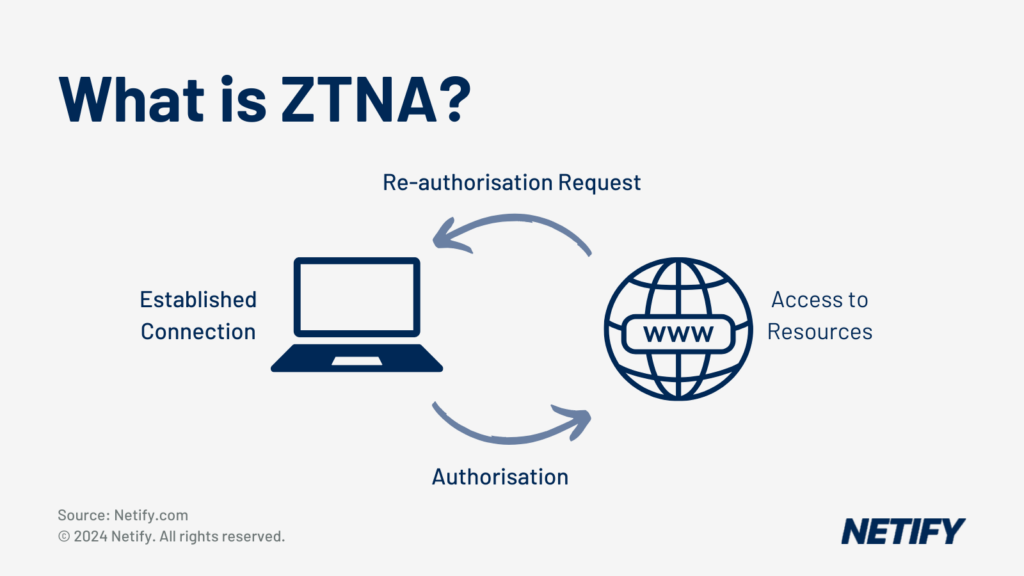
When paired with a role-based access solution, healthcare provider using ZTNA not only provides different levels of access for clinicians, administrators and third-party vendors, but can also minimise unauthorised access through multi-factor authentication techniques and monitoring.
In practice, when considering a remote workforce accessing patient records in the cloud, the remote professional will need to verify themselves via multi-factor authentication, their device will need to comply with all security policies and all traffic must be encrypted. If there are any issues during this process, such as failed login attempts, the ZTNA system can detect the suspicious activity, alert network administrators and block access to the system.
When such issues are identified, ZTNA logs access attempts and user activities in order to provide network administrators with a clear audit trail for regulatory compliance purposes in the event of an investigation.
Cloud Access Security Broker (CASB):
At heart of many care operations, the cloud has become essential to the healthcare industry. From Electronic Health Records (EHR) systems to Medical Imaging Storage and Clinical Decision Support Systems. (CDSS), there's no doubt that healthcare professionals rely on the cloud daily.
Supporting systems, such as Remote Patient Monitoring and Health Information Exchanges are important for the sharing of health data and analysis of patients with chronic conditions, but all would not be possible at such a scale without utilising the cloud.
Cloud Access Security Broker (CASB) is designed to improve the security of data being transferred across these cloud-based applications and platforms, which is a requirement if healthcare providers are to comply with industry regulations.
CASB achieves this by enforcing encryption measures (such as AES-256) and applying the same security measures that apply within internal networks, to cloud platforms too.
By introducing these measures, CASB mitigates potential risks such as unauthorised patient data storage on non-compliant platforms or sensitive care data (including those from IoMT devices) being transmitted in plain-text. Further to this, CASB provides healthcare networks with greater visibility into cloud application usage and enables network administrators to quickly identify potentially malicious activity or risky behaviour patterns.
Secure Web Gateway (SWG):
Secure Web Gateway (SWG), as the name suggests, adds security when healthcare professionals access web-based platforms. Similar to how CASB secures cloud applications, SWG can be used to protect typical web platforms, which include patient portals, medical billing systems, pharmacy management systems and Laboratory Information Systems (LIS).
To achieve protection of such web applications, SWG filters malicious content by inspecting web traffic for malware, ransomware and other threats, enforces security policies and monitors for unauthorised sharing of Protected Health Information (PHI).
This means that healthcare providers can leverage web applications for improved patient care by utilising secure browsing within both clinical and remote environments.
Firewall-as-a-Service (FWaaS):
However, whilst CASB enables cloud and SWG enables web platforms, healthcare providers will be just as concerned for widespread security, especially for internal networks, such as within hospital settings. For protecting the broader network across all edges (and the internal network itself) a firewall is essential and can be key to ensuring patient care systems that rely on networked data (e.g: patient monitoring systems, imaging systems, ventilators, anaesthesia machines and even laboratory equipment) do not experience interruptions.
To combat the threat of these systems going offline, SASE leverages Firewall-as-a-Service (FWaaS) capabilities, which deliver cloud-based firewall protection across the full range of healthcare facilities and eliminates the need to install individual firewall components on each premises.
FWaaS protects patient monitoring, administration systems and laboratory databases, simplifying management by integrating with existing security policies and platforms to enable a single, all-encompassing security solution.
Software-Defined Wide Area Network (SD-WAN):
Finally, SASE introduces greater network access through Software-Defined Wide Area Network (SD-WAN) solutions. SD-WAN provides application-level controls, which can be utilised to prioritise the more high-impact healthcare technologies. Electronic Health Records, typically one of the most frequently accessed systems and PACS (medical imaging), which can send higher traffic volumes than other applications, therefore massively benefitting from the performance improvements that SD-WAN brings about.
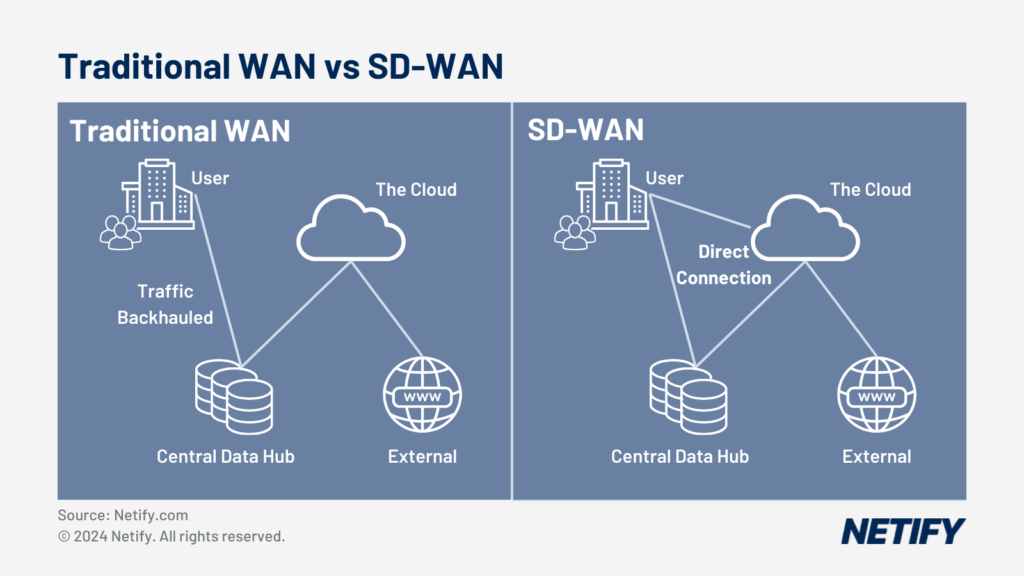
SD-WAN achieves this by implementing dynamic traffic routing and Quality of Service (QoS) to load-balance traffic based on priority. Further to this, SD-WAN can also switch across multiple network underlays to ensure that technologies such as remote telehealth are always running across the optimal path, providing real-time data access.
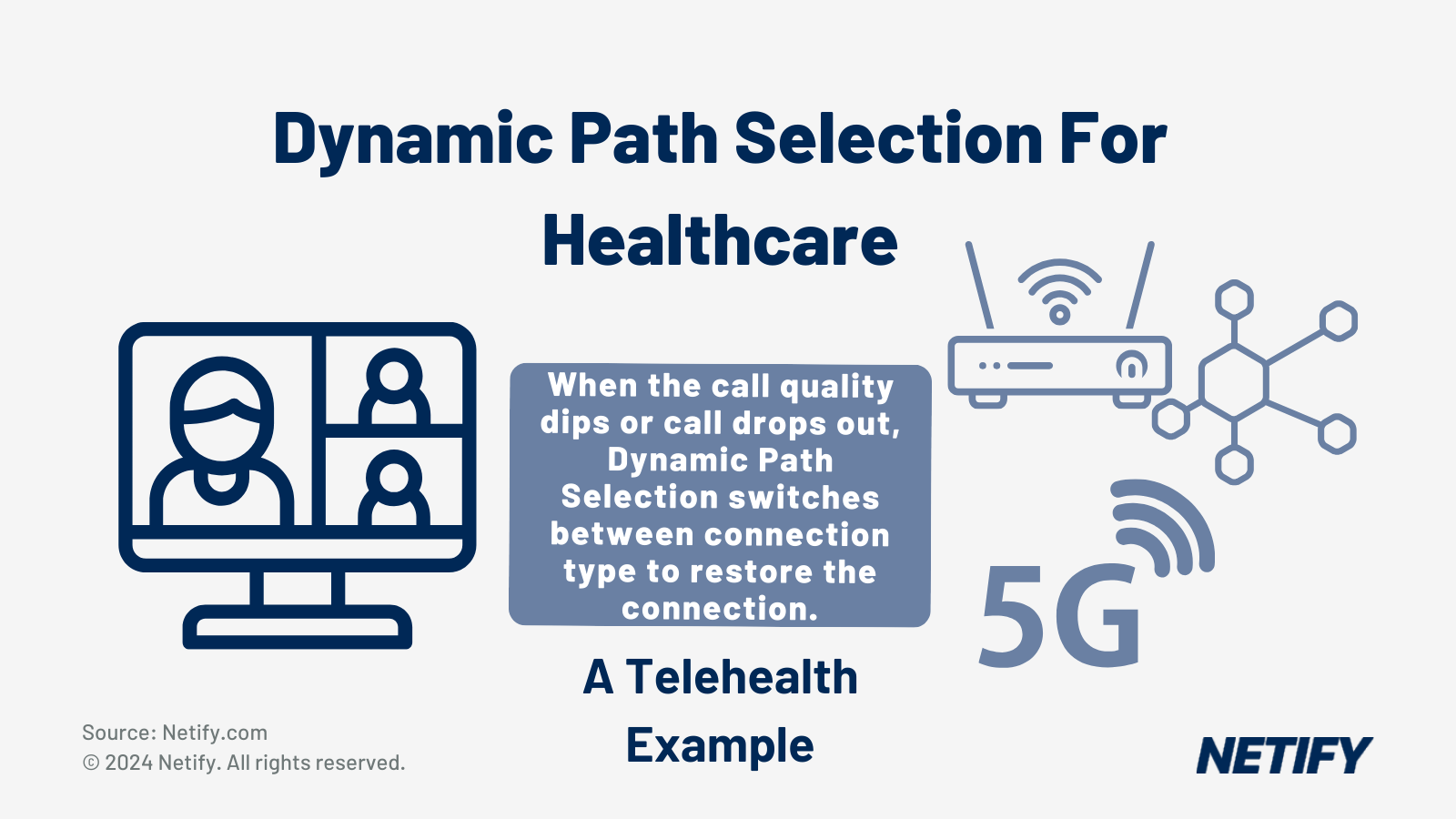
However, whilst prioritising specific traffic types is an important feature, arguably the most important network functionality is the ability to maintain continuous uptime for care systems. The use of multiple network underlays is essential to SD-WAN offering improved uptime for telehealth, IoMT, patient monitoring, EHR access alongside other care systems.
By leveraging this capability, redundant network underlays can be used in the event of a link outage. Whilst an important feature for most businesses, this features significance is emphasised within the healthcare sector, with potentially severe consequences faced by (typically traditional WAN) networks unable to meet service demand or the effects of downtime.
Why SASE is Critical for Healthcare IT Decision-Makers
Regulatory Compliance:
We would argue that the biggest headache that network administrators in the healthcare industry face is trying to comply with regulations, especially when multiple geographical locations are involved.
SASE solutions leverage their core components (ZTNA, SWG, CASB and FWaaS) to tackle this headache in a converged manner. Integrating SASE helps protect sensitive patient data as well as care systems, all of which are covered are focal points of the various industry regulations from around the world:
Different Aspects of Healthcare's Digital Protection Regulations From UK and North America
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Aspect | UK (GDPR, NHS Digital) | North America (HIPAA, PIPEDA) |
|---|---|---|---|---|---|---|---|
| 1 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Legislation Type | Comprehensive data protection (GDPR) with healthcare-specific guidelines (NHS Digital) | Healthcare-specific regulation (HIPAA) in the USA, and general data protection regulation (PIPEDA) in Canada, with adaptations for the healthcare sector |
| 2 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Scope | All personal data, including healthcare data handled by both public and private sectors | In the USA, applies to healthcare providers, insurers, and their business associates. In Canada, applies to all personal data, including healthcare data handled by commercial organisations |
| 3 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Data Sharing within Networks | Strict rules about sharing with third parties without explicit consent, NHS Digital oversees secure data sharing within NHS networks | Allows sharing of patient data for treatment, payment, and operations without explicit consent but requires safeguards in the USA. In Canada, allows sharing with adequate consent, organisations must establish policies for data exchange security |
| 4 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Data Encryption Requirements | Encryption is recommended under GDPR as a security measure, NHS Digital has strict guidelines for encryption to protect patient data during transfer | HIPAA mandates encryption of electronic Protected Health Information (ePHI) during storage and transmission, particularly in networks. In Canada, PIPEDA recommends encryption as a best practice for secure data exchange, focusing on minimising unauthorised |
| 5 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Data Breach Notification | Mandatory notification to the ICO within 72 hours for breaches, including those impacting healthcare networking | Mandatory notification to HHS and affected individuals without unreasonable delay, generally within 60 days, in the USA. In Canada, mandatory notification to the OPC and affected individuals is required when a breach poses a significant risk of harm |
| 6 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Patient Consent | Explicit consent is required for the processing of patient data, NHS Digital provides a framework for managing patient consent for data sharing | Implied consent is sufficient for treatment, payment, and operations in the USA, while written consent is needed for non-standard use. In Canada, implied consent is used for essential healthcare services, while explicit consent is needed for secondary use |
| 7 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Data Portability | Patients have the right to request copies of their data in a portable format, including healthcare records (applies under GDPR) | HIPAA guarantees patient access to health records, allowing digital copies if feasible, but no specific portability format is mandated. In Canada, PIPEDA requires organisations to provide access to personal data in an accessible format upon request |
| 8 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Third-Party Vendors | GDPR holds both data controllers (e.g. hospitals) and processors (e.g. vendors) accountable, Data Processing Agreements are required | Both HIPAA in the USA and PIPEDA in Canada require organisations to ensure third-party vendors meet privacy obligations. HIPAA mandates Business Associate Agreements (BAAs) for all third parties handling ePHI, whereas PIPEDA recommends contracts to ensure |
| 9 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Data Localisation | Data can be processed within the EU/EEA or other countries with adequate protection, special considerations apply to NHS patient data for security and privacy | No localisation requirements in the USA, patient data can be stored offshore provided HIPAA requirements are met. In Canada, there are no specific localisation requirements, but organisations must protect transferred data, including cross-border data shar |
| 10 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Interoperability & Standards | NHS Digital supports interoperability and data standards such as FHIR (Fast Healthcare Interoperability Resources) to facilitate secure networking between systems | Encourages interoperability through ONC standards and FHIR adoption in the USA, focusing on secure communication channels within healthcare networks. Canada also supports interoperability, often guided by provincial regulations, and generally follows FHIR |
And for network administrators that are still unsure whether SASE can meet their regulatory requirements, SASE also embeds Data Loss Prevention (DLP) tools. DLP within SASE can ensure data integrity and improves patient trust by adding breach mitigation tactics, such as preventing unauthorised patient data exfiltration.
Data Protection and Privacy:
Data Protection and Privacy rules require sensitive patient information to be protected both when stored and when transmitted. This is made especially important when considering healthcare organisations that frequently transmitting data between hospitals, laboratories and any remote workforces.
By enforcing end-to-end encryption regardless of the network edge, SASE ensures that patient data is protected from unauthorised access internally or when using either the web or cloud applications.

In the event of data misuse, SASE can also quickly pick up on malicious activity through behavioural analysis techniques. Behaviour analysis identifies and mitigates against unusual practices, such as unauthorised access to patient records or attempted data exfiltration. Once identified, SASE solutions either alert network administrators or, as supported by some providers, automatically remediates the issue. By forming either a full or partial resolution to data privacy issues, healthcare providers are assisted with regulatory compliance.
Remote Access for Healthcare Professionals:
For healthcare providers wanting to add remote access to their care-arsenal, we would strongly recommend healthcare network administrators consider SASE for secure, role-based access to systems. This role-based access is not only applicable to on-site network access but also remote staff, eliminating the vulnerabilities often associated with traditional VPNs.
Remote access with SASE is ideal for supporting telemedicine due to the combination of security and access capabilities, which enables healthcare providers to deliver high-quality, encrypted video consultations, ensuring both data security and continuity of care.
Support for Modern Healthcare Innovations:
SASE is, arguably, the most scalable solution for healthcare organisations to integrate security for more modern care technologies. SASE can be leveraged to adapt to the scale of an expanding Internet of Medical Things (IoMT) equipment range, new hospital branches and care facilities, as well as merging networks from new acquisitions. Integrating new clinics, telehealth services and remote staff into the network becomes more straightforward with SASE, making network administration more simplified, allowing administrators to focus on delivering new health technologies, rather than network integrations.
Key Benefits of SASE for Healthcare
Enhanced Security Posture:
SASE connects hospitals, clinics, pharmacies, and research facilities globally through a cloud-based network and points of presence (PoPs). By moving away from traditional branch connectivity, SASE enables healthcare providers to transmit data securely between geographically dispersed teams.
The consolidation of network and security tools into a single framework, allows network administrators to efficiently secure complex infrastructures, including multi-location hospitals or telehealth platforms. One of the SASE capabilities yet to be discussed in this article, advanced threat detection improves the overall security posture of healthcare network by preventing attacks targeting healthcare systems. With typical attacks including ransomware on Electronic Health Record (EHR) databases and phishing attempts on administrative staff, implementing SASE’s security can be pivotal for healthcare networks to ensure systems aren’t compromised.
Improved Network Performance:
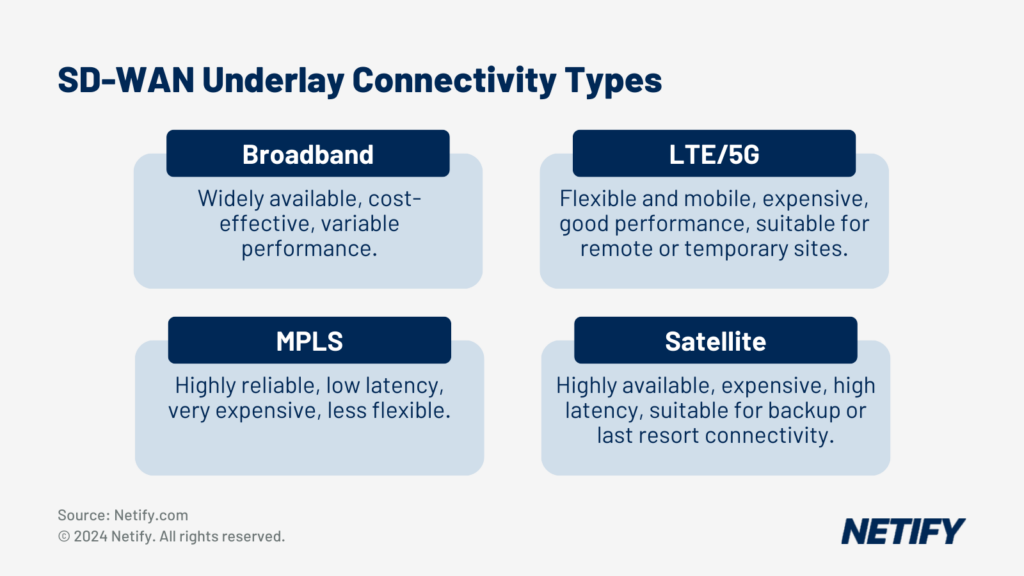
The SD-WAN element of SASE is ideal for improving network performance. With SASE, healthcare organisations can prioritise applications, ensuring real-time availability for systems such as medical imaging and EHRs. Prioritisation, through methods such as Quality of Service, dynamic path selection and link aggregation, combines to minimise latency experienced by care systems. This significantly improves the care experience for both healthcare professionals and patients.
Operational Efficiency and Cost Savings:
With the addition of SD-WAN into SASE architectures, healthcare providers can replace legacy hardware (such as MPLS) in a move towards using more cloud-delivered solutions.
By utilising the cloud, healthcare providers can scale systems as and when there are influxes in demand, reducing the risk of paying out for resources that aren’t being used.
SASE therefore reduces CAPEX (capital expenditure), whilst network administrators can benefit from cloud management. Management can be conducted via a single centralised platform, with security policies, traffic prioritisation/Quality of Service (QoS) configurations and report generation all in one place.
Centralising management means that network administrators only have to set network-wide policies once (rather than the traditional method of implementing them at every network edge) and therefore reduces administrator workload. This means that network administrators can focus their attention on integrating new medical technologies. Further to this, healthcare providers should consider the cost efficiency this brings, not only from scalable cloud resources, but by not needing to allocate network administrators to repetitively change policies across edges.
Use Cases for SASE in Healthcare
Telemedicine Security:
Telemedicine has become an important innovation for the healthcare industry Enabling remote consultations and sharing of medical data across large geographical locations has become essential for the industry; however, adding security is a must, given the sensitive nature of the technology.
SASE encrypts patient data during video consultations, ensuring services remain uninterrupted and protected against threats such as DDoS attacks, which is essential for maintaining trust and regulatory compliance in telehealth services.
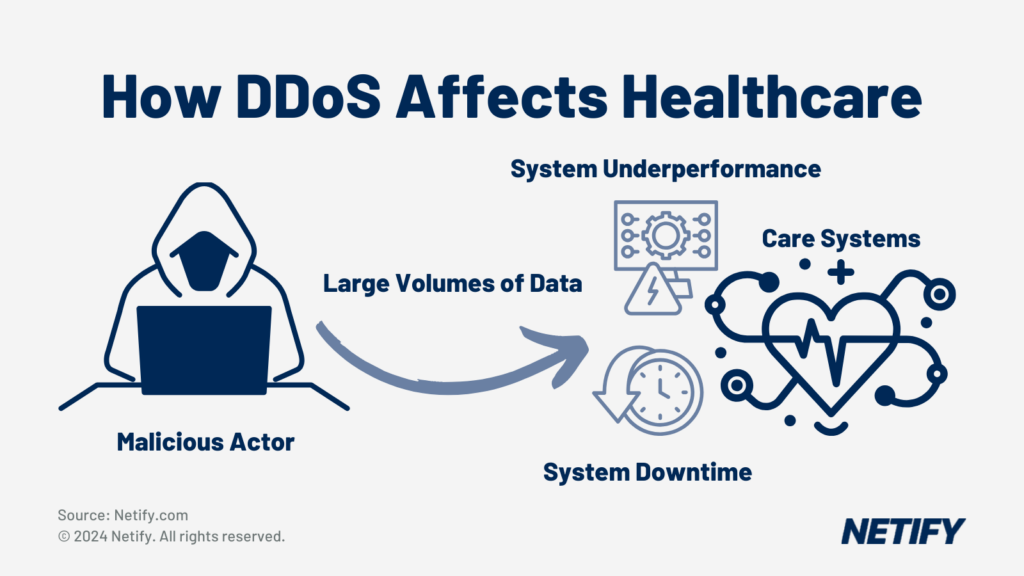
IoT Device Protection:
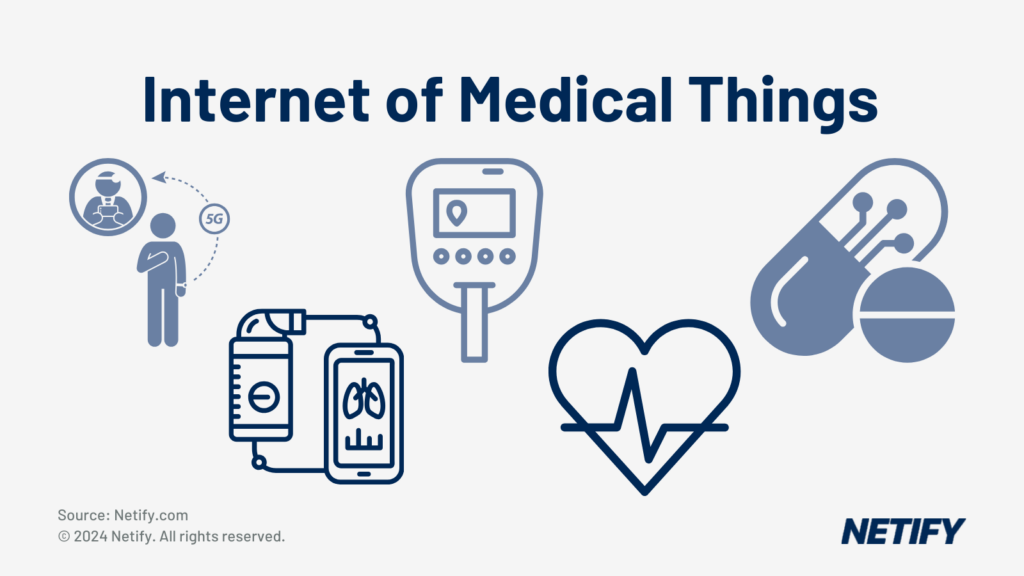
IoT (Internet of Things) devices, often coming in the form of sensors and smart devices have changed computing by using vast amounts of data in order to convert analysis of the real-world into digitised formats.
And this is showcased in the healthcare industry where Internet of Medical Things (IoMT) are increasingly being introduced. IoMT devices include:
- Remote patient monitoring devices,
- Glucose monitors,
- Heart rate monitors,
- Smart inhalers,
- Connected contact lenses,
- Wireless blood pressure monitors,
- Implantable cardioverter-defibrillators (ICDs),
- Smart pills,
- Personal Emergency Response Systems (PERS)
- Smart Hospital Equipment
Due to this widespread reliance on IoMT that will surely only continue to grow, implementing security measures for IoMT devices should be a major consideration for healthcare providers. SASE solutions support IoMT with its segmentation and ZTNA capabilities.
By isolating IoMT devices into their own segment, healthcare organisations can prevent lateral movement from and to other networked systems, protecting and containing IoMT devices.
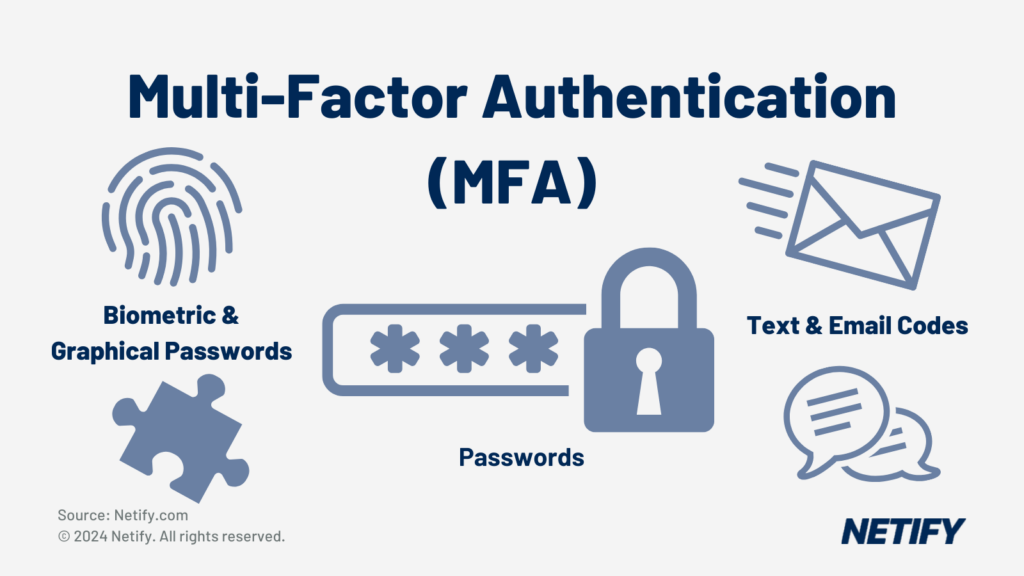
ZTNA with multi-factor authentication (MFA) methods are ideal for restricting access to the data produced from IoMT devices, whilst device management techniques to maintain software and firmware of IoMT devices are essential best practices.
Distributed Hospital Networks:
For healthcare organisations with multiple facilities, SASE simplifies connectivity of dispersed systems. By providing each network edge with consistent connectivity and security, network administrators can ensure that professionals have seamless access to shared resources, e.g: EHRs, regardless of the edge. This capability facilitates real-time collaboration, enhancing diagnostic accuracy and care delivery.
Clinical Trials and Research:
To gain insights into new healthcare opportunities, the use of clinical trials is incredibly important. However, the data that clinical trials often involve is also highly sensitive and needs to be securely shared across multiple research centres (in order to remain compliant with regulations). SASE protects this data and ensures compliance with data protection regulations across a range of jurisdictions, enabling secure collaboration in research.
Third-Party Vendor Access:
Finally, Healthcare organisations can often rely on external vendors, which can introduce supply chain risks to sensitive data.
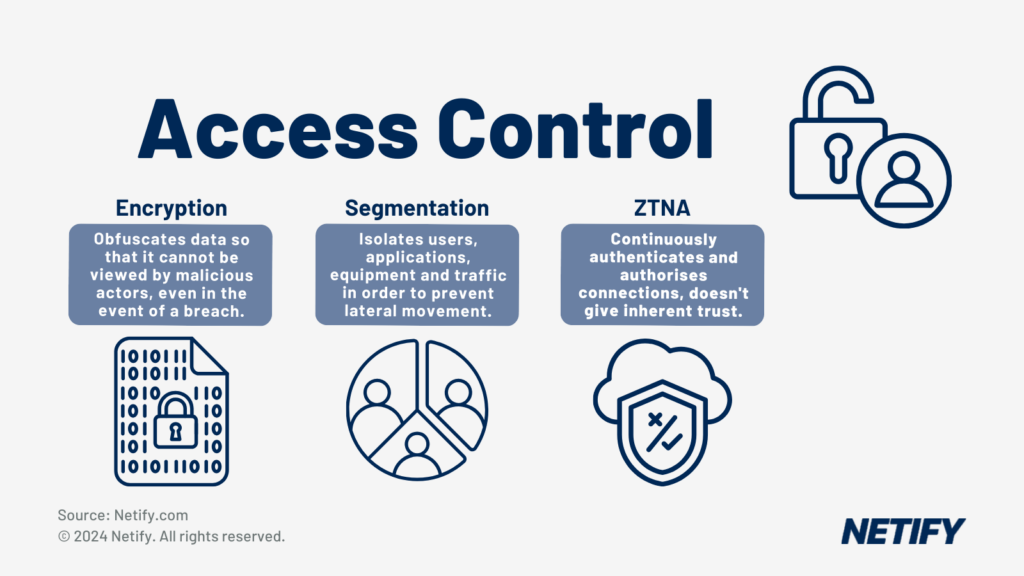
SASE enforces granular access controls for professionals and third-parties, ensuring they only have access to authorised systems. Continuous monitoring builds on this to help mitigate risks associated with third-party involvement and puts remediation strategies into place should a breach or data exfiltration be identified.
Challenges in Adopting SASE for Healthcare
Integration with Legacy Systems:
Given that the healthcare industry has become reliant on proprietary and often legacy technologies in order to deliver care, simply getting rid of these systems is out of the question. Unfortunately, many of these systems have intricacies that need to be catered to by the network that houses them. This means that there may be difficulties when attempting to integrate these legacy systems within a SASE framework and network administrators should take the time to carefully identify the most appropriate vendor and then integrate these systems slowly to ensure there are no rollout issues. Whilst this can be challenging for the healthcare industry, the long-term benefit of integrating SASE with these systems far outweighs integration efforts.
Regulatory Complexity:
Given the strict regulations that healthcare providers have to adhere to, it’s also advisable that IT decision makers within the healthcare sector consider implementing compliance management tools. These tools monitor internal network and cloud environments to ensure that legal standards such as HIPAA, PIPEDA and GDPR (dependent on your region) are being adhered to. These tools can automate compliance checks, vastly reducing the workload for network administrators, as well as generating reports which can be especially useful in the event of an audit.
When put into practice, a compliance management tool works alongside a SASE solution in order to flag instances of unencrypted patient data that is being transmitted between services, allowing for immediate remediation and healthcare providers to comply with regulations.
Vendor Selection:
We would argue that the single most difficult issue when implementing SASE for a healthcare setting is selecting the right vendor. Due to vendor offerings vastly differing from solution to solution. The Healthcare industry must prioritise vendors with a proven track record in the sector, particularly those familiar with medical device security and healthcare-specific regulatory compliance. Further to this, by considering legacy and proprietary system requirements, healthcare providers should identify which vendors solutions can support these systems.