What is Healthcare Network Security?
| Network Security in Healthcare is required to ensure compliance with legislation and guidelines (GDPR and NHS Digital in the UK, HIPAA for US and PIPEDA for Canada) whilst also protecting sensitive patient care data from criminal activities. |

It’s no secret that the healthcare industry is continuously facing threats. From ransomware to DOS attacks attempting to take down care facilities, network administrators for healthcare providers have to juggle maintaining system uptime with ensuring patient data is secure in order to meet compliance with industry regulations.
In this article we cover a range of security issues experienced by healthcare providers and how introducing SASE, SSE and AI-driven security solutions can play a pivotal role in protecting their network. These solutions are essential for preventing breaches and overall, providing patient care with no downtime through techniques such as Advanced Persistent Threat mitigation, encryption, firewalls and Zero Trust Architectures.
Table of Contents
Access Control
Arguably the most important facet of network security within the healthcare industry is the restrictions imposed on data access. Without data access, the healthcare industry couldn’t comply with regulations such as the General Data Protection Regulation (GDPR) in the UK. Data access isn’t only limited to regulations though – in a healthcare setting, typically all patient data is strictly confidential and should remain so unless required for diagnosis, treatment or care reasons. This means that healthcare providers have a duty of care to protect patient data from prying eyes, bad actors or malicious threats.
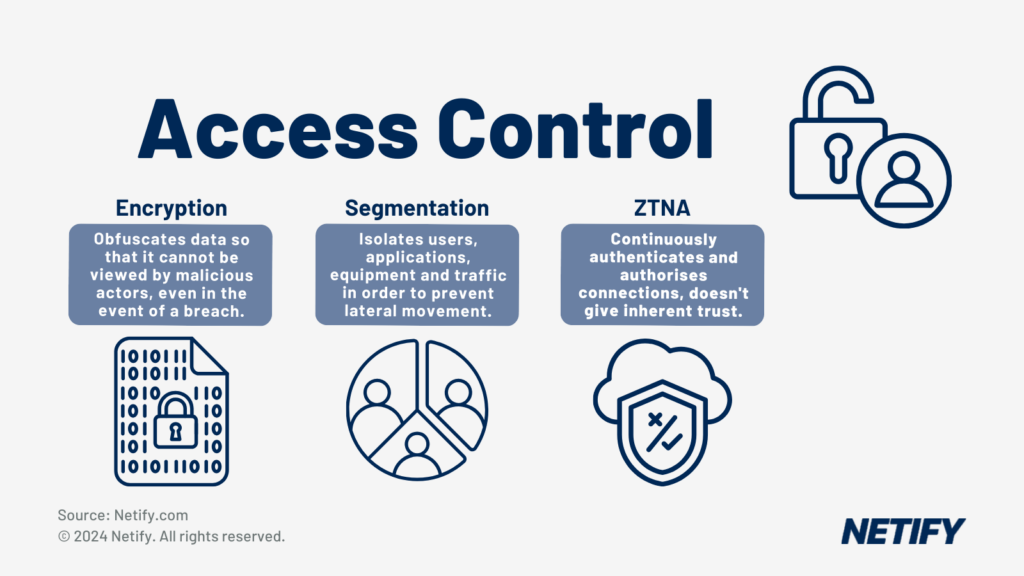
The best way for network administrators in the healthcare industry is to implement functions such as Zero Trust Network Access (ZTNA), segmentation and encryption. These features, all typically integrated into SASE and SSE solutions, restrict access to data by:
- Encryption: Removing the ability to read the data without decryption.
- Segmentation: Isolating the data from the rest of the network.
- ZTNA: Refrains from automatically trusting accessor based on user, device or location and continuously requires accessor to re-authenticate themselves in order to gain authorisation and access to data.
These features mean that patient records and sensitive medical data can be adequately protected from unauthorised access. Without them, healthcare networks can struggle to support role-based access, therefore emphasising the importance for healthcare providers to maintain access control.
However, even with access control implementations, healthcare networks are still vulnerable to more sophisticated attacks.
Advanced Persistent Threats (APTs)
One potential form of these sophisticated attacks that can be particularly effective in systems that have neglected to implement role-based access are Advanced Persistent Threats (APTs). APTs infect a network with the sole intention of gaining as much access as possible to different facets of the network over an extended period of time and then stealing data back to an attacker. APTs differ from more traditional attack vectors as they tend to be more complex and are persistent, remaining active after initial access. They also don’t necessarily start malicious activities straight away, with manual startups often being utilised (such as via a wait, trigger or command). By straying from an automated initialisation, APTs can be more subtle, appearing human-led to avoid detection.

Once started APTs will attempt to move laterally throughout the network, ascertaining the breadth that the APT has access to and the data that may be worth taking. Only once this has done, do APTs then start their attack, minimising detection and allows for the entire network to be attacked, not just a single section.
APT attacks typically follow the below timeline:
- Reconnaissance: Attacker finds potential vulnerabilities in the network or healthcare provider’s systems.
- Gain Access: The APT is deployed onto the network.
- Lateral Movement: The APT attempts to move across the network laterally, allowing for discovery of access limitations, data of interest and other potential vulnerabilities or weaknesses in the network and underlying infrastructure.
- Exfiltration: Once the APT has finished moving laterally, the process of stealing data can begin. Typically, this is sent to a remote location so that an attacker can then access the data without having to be present or on-site.
- Post-Exfiltration: The clean-up process of the attack. Whilst the APT can remain on the network, either exfiltrating more data or acting as reconnaissance for future attacks, post-exfiltration is usually made up of cover-ups. These cover-ups hide the malicious activity so that its harder for retroactive network scans to pick up on the activity.
With this in mind, network administrators within the healthcare industry must put counter measures in place for defending against reconnaissance and lateral movement, whilst also being able to utilise a dynamic Quarantine and Recovery (QaR) system to address the specific nuances of individual APT threats. By introducing a QaR, healthcare providers can counteract different APT functions and therefore minimise the impact that they can have on the network in the event of a breach.
QaR systems frequently use Artificial Intelligence (AI) to achieve this, with AI allowing for more adaptive responses to issues, rather than static policies or rules which may not catch all behaviours of the APT.
SSE (Security Service Edge)
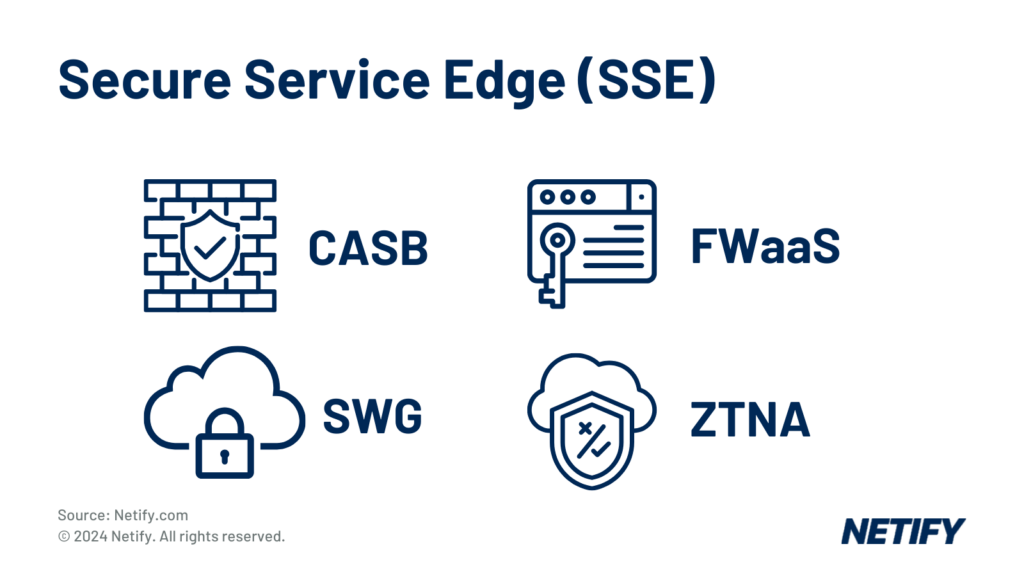
Secure Service Edge (SSE) provides the healthcare industry with the ability to decouple networks from their security measures. Increasingly adopted, SSE reduces the risk of leveraging disparate solutions and ensures that, through the use of a single vendor, that multiple security capabilities are bundled together via a cloud-centric model for ease of integration.
These cloud-based security services, such as Cloud Access Security Broker (CASB), Firewall-as-a-Service (FWaaS), Secure Web Gateway (SWG) and Zero Trust Network Access (ZTNA).
These features are essential for the Healthcare industry, who require strict security policies to be enforced across cloud applications. SSE can be particularly beneficial for patient management systems, telemedicine and meeting data privacy and compliance with healthcare regulations.
However, SSE is extended with SASE.
SASE (Secure Access Service Edge)
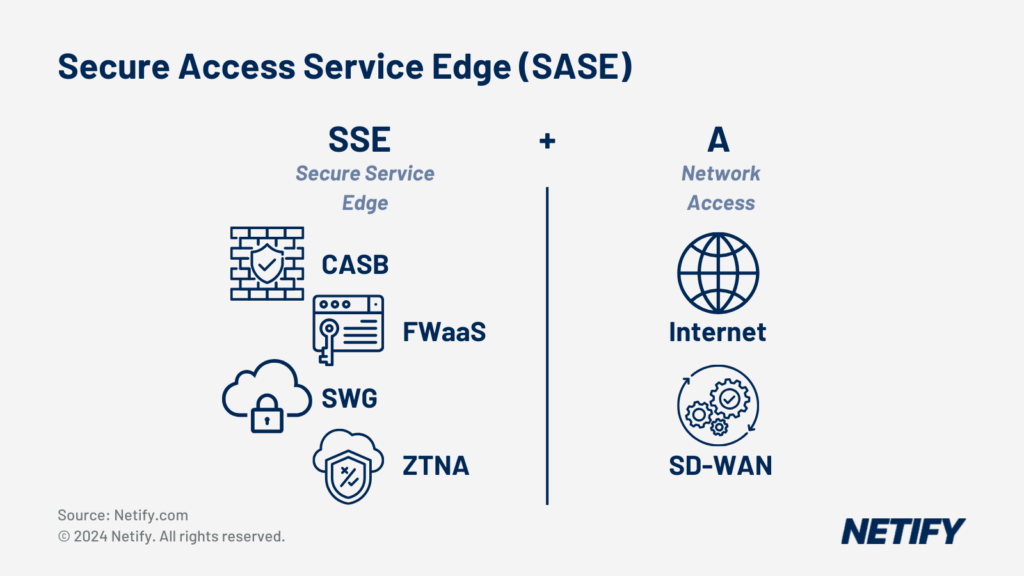
SASE combines SSE with the Access (A) of Software-Defined Wide Area Network (SD-WAN) solutions in order to make Secure Access Service Edge. SD-WAN is used to simplify the management of a network by providing automated traffic routing over several network links, a centralised dashboard for controlling user access, policy management and cloud integrations. By unifying these features, SASE enables efficient connections across distributed and mobile workforces, providing access to the healthcare network based on identity not the connection origin location. This factor means that SASE supports all network edges, reducing the complexity for network administrators and enabling local breakout access to the cloud for more effective use.
Through this increased connectivity, SASE can improve the security of remote medical services and telehealth by unifying security protocols to ensure that patient data is protected both on-premises and across remote facilities.
Artificial Intelligence (AI) in Network Security
Whilst not a new technology, in recent years Artificial Intelligence (AI) has seemingly been integrated into every aspect of computing and this is also the case for network security.
AI and machine learning algorithms are being implemented in order to improve threat detection and response capabilities. Learning from large datasets and combined threat intelligence, AI can adapt to new threats by learning malicious behaviours, catching even zero-day threats. Within a healthcare setting, AI network security tools analyse network traffic patterns in real-time to detect anomalies that may indicate breaches, malware or APTs that could affect patient care or cause downtime to hospital equipment.
Data Encryption

Encryption is an essential security measure that converts readable patient data (plain text) into cipher text, typically utilising a key or hashing algorithm, so that data can be stored/transmitted in a secure format only accessible by authorised users or systems.
Encryption is therefore an essential capabilities for healthcare networks, obscuring patient data so that the data cannot be read by unauthorised accessors, even in the event of a breach.
Artificial Intelligence is increasingly being used to improve encryption protocols by adapting them in real-time to ongoing threats, which introduces dynamic data protection in comparison to traditional encryption methods.
Essential to complying with regulatory requirements, encryption should be at the forefront of healthcare network design, making SSE/SASE solutions all the more desirable, especially those offering AI-driven dynamic data protection.
Data Loss Prevention (DLP)
In the same way that encryption can protect data even in the event of a breach, Data Loss Prevention (DLP) offers the ability to prevent unauthorised sharing or leakage of sensitive data if an APT or other threat manages to find a way onto the network and attempts to start exfiltrating data.
DLP works by identifying sensitive information within your business network, analysing traffic to pattern match against this sensitive information and stops transmission in its tracks in the event of a match.
For healthcare networks, Data Loss Prevention is a core feature that should be implemented, assisting with minimising the impact any potential breach may cause – which can be heavily tied to regulatory compliance. DLP tools are typically integrated into many SASE solutions and a range of vendors have introduced Artificial Intelligence to continuously update scanning policies. This has consolidated DLP’s capabilities in an industry that is constantly integrating a range of new technologies, such as IoT and telemedicine, allowing for new forms of sensitive information to be quickly identified without human intervention.
Further to this, DLP enables patient data to be kept secure when sharing across hospital departments or with external partners, all of which are transmission points over multiple mediums and lead to potential vulnerabilities for breaches.
Zero Trust Architecture
In the past, the use of in-house system architectures had helped standardise a perimeter-security model. This implies that any device connecting to the network from within the in-house healthcare network should be assumed to be authenticated and thus the network is designed to primarily prevent threats from outside the healthcare network.
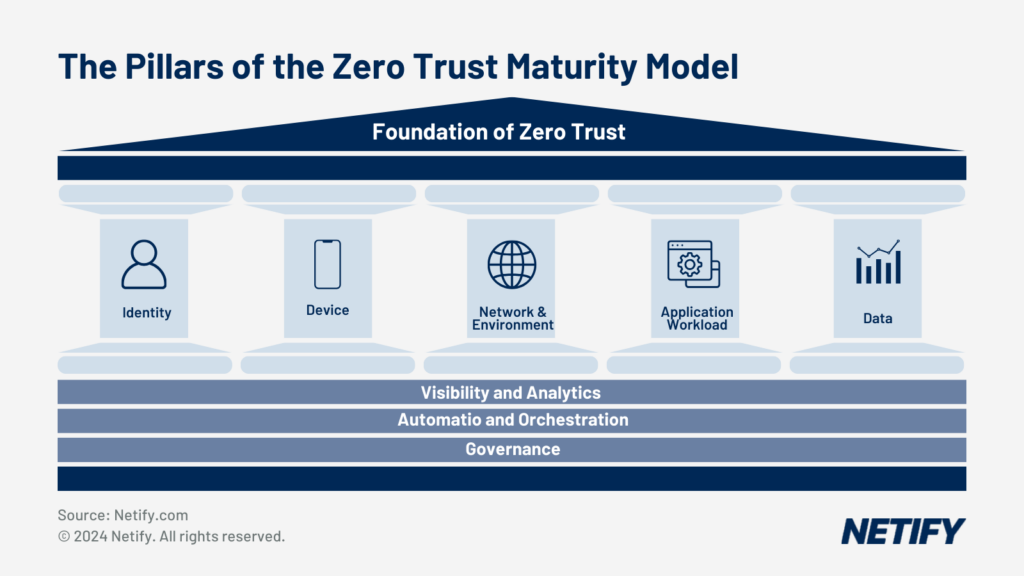
Zero Trust is an identity-centric security strategy designed to provide no trust-based access to systems and therefore moves the boundary to be from the system to the connecting device. There are three core principles to Zero Trust:
"Never trust, always verify"
Access trust is withheld until a full identity check is completed for the connecting professional or sensor system. Regardless of the device or application attempting to access the system, authentication is a must in order to access the healthcare network. By undergoing this trust brokering process, this treats each connection as if it were entirely new and ensures there is sufficient authentication and authorisation before granting access to any resources or patient data.
Least privilege for context
After the verification process is complete, the system must consider the requirements of the application and the range of privileges the accessing professional should have access to. This is a major consideration as, for example, a surgeon and a reception administrator should have very different access privileges. By differentiating, healthcare networks can provide the professional with the minimal access required in order to carry out their tasks. The professional should therefore have no visibility or access to parts of the system outside their permitted scope.
Device security
Finally, if all identification and privilege checks complete successfully, the system must validate that the user’s device is secure. This validation commonly includes: regulatory compliance tests and antivirus (or alternate security solution) on the connecting device are operational.
Following access being granted, the system must continuously monitor and validate the system. If there are any changes to any of the three principles the connection must be re-evaluated and should they no longer be deemed valid, the system must assume security has been compromised and revoke access.
By applying a Zero Trust architecture within the healthcare industry, providers can ensure that patient data is protected across all access points, with verification preventing inherent trust to critical medical systems.
Electronic Health Record (EHR) Security
According to the National Institutes of Health (NIH), in 2022 there were 1463 cyber attacks weekly, with one of the most common targets being Electronic Health Records (EHR). The reason for this being that EHR systems contain such a vast quantity of health history and treatment data, which can be used for a myriad of malicious activities, such as social engineering and ransom. Further to this, any downtime caused by EHR attacks can be severely disruptive to healthcare services, with the average downtime for hospitals at 24 days, with the average cost of $10 million.
This means that protecting EHR systems should be a major consideration for healthcare providers. Luckily SSE & SASE solutions have this covered, offering Next Generation Firewall (NGFW) integrations, allowing networks to protect EHR systems and setup alerts to administrators if suspicious activity is detected. In addition to the firewall, creating access control measures also mean that healthcare providers can limit access to EHR data, stopping unauthorised attackers.
Internet of Medical Things (IoMT) Security
IoT (Internet of Things) devices, often coming in the form of sensors and smart devices have changed computing by using vast amounts of data in order to convert analysis of the real-world into digitised formats.
And this is showcased by in the healthcare industry where Internet of Medical Things (IoMT) are increasingly being introduced. IoMT devices include:
- Remote patient monitoring devices,
- Glucose monitors,
- Heart rate monitors,
- Smart inhalers,
- Connected contact lenses,
- Wireless blood pressure monitors,
- Implantable cardioverter-defibrillators (ICDs),
- Smart pills,
- Personal Emergency Response Systems (PERS)
- Smart Hospital Equipment
Due to this widespread reliance on IoMT that will surely only continue to grow, implementing security measures for IoMT devices should be a major consideration for healthcare providers.
By isolating IoMT devices into their own segment, healthcare organisations can prevent lateral movement from and to other networked systems, protecting and containing IoMT devices.
ZTNA with multi-factor authentication (MFA) methods are ideal for restricting access to the data produced from IoMT devices, whilst device management techniques to maintain software and firmware of IoMT devices are essential best practices.
Endpoint Detection and Response (EDR)
Whilst firewalls are typically ideal for securing IoMT devices, for endpoint devices such as servers, laptops, tablets or handheld devices, Endpoint Detection and Response (EDR) is more preferable.
EDR solutions monitor, detect and respond to potential threats across endpoint devices that are used by doctors and staff, ensuring that patient information remains secure from unauthorised access.
Once a threat is detected, EDR analyses its nature and responds by either containing, blocking or rolling back the threat. Containing prevents threats from accessing a wider range of the network, blocking stops transmissions of malicious or exfiltrated patient traffic and roll backs rewind the network to an earlier state.
Telehealth and Remote Care Security
The introduction of Telehealth and Remote Care has eased restrictions previously imposed on patients that previously had to go into a clinic or hospital for treatment. However, by connecting remote or mobile workforces, equipment and sensors, healthcare providers are essentially extending their network edges, exposing a greater attack plane that must be protected.
Whilst the US Department of Health and Human Services provides privacy and security tips for patients, one way that healthcare providers can protect against these is with SSE and SASE security. By integrating encryption from SASE, telehealth services can provide encrypted connections to networked systems, regardless of the geographical location that the remote care workforces are accessing from.
Network Segmentation
Network segmentation is the process of isolating network traffic, applications or data into their own subsections of the network. Often considered as a foundational security strategy, segmentation can be utilised to improve network performance and also to prevent lateral movement in the event of a breach.
Network segmentation has been adopted into many SD-WAN and SASE solutions and provides a shift from static VLAN to a dynamic, policy-based approach. Whilst VLANs are effective, SD-WAN mitigates their limitations in flexibility and cost-efficiency through easily configurable software configuration-based segmentations.
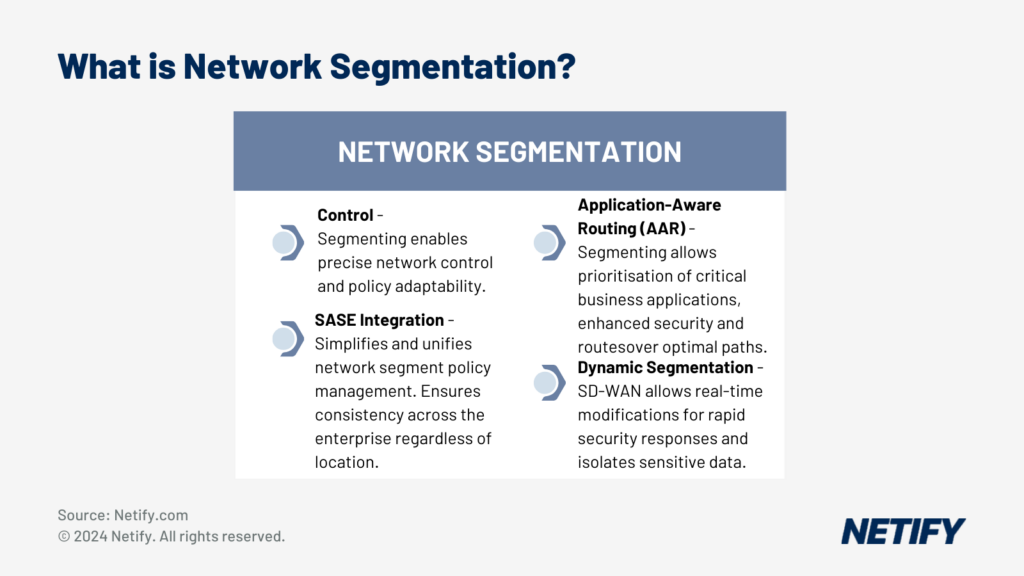
For the healthcare industry, network segmentation is essential for isolating sensitive patient data, research databases and equipment traffic from general administrative traffic, minimising the amount of exposed attack planes and minimising potential breaches.
Phishing and Social Engineering Prevention
Phishing and Social Engineering go hand-in-hand for arguably some of the most powerful tools in an attacker’s arsenal. These are tactics built to exploit vulnerabilities in humans rather than computer systems, by pretending to be someone or something they’re not in an attempt to gain trust or access to a restricted system.
Although email filters and similar techniques are simple solutions for more basic prevention, phishing and social engineering doesn’t have to be computer-based. Any forms of deception or information exfiltration are examples of phishing and social engineering,
Therefore, the best way to prevent against social engineering and phishing is to focus primarily on the deception and exploitation of a workforce, rather than dedicated computer-based restrictions. This means that workforces should undertake rigorous training to teach them what to look out for, the importance of securing the network and the principles of verifying before trusting.
Once achieved, healthcare providers should then look to implement computer-based techniques, such as AI-powered email filters, which detect and block phishing emails that are targeting healthcare employees before they even get the chance to read them.
Alongside training and filtering, using Zero Trust Architecture within SASE allows for the network to constantly re-authentication accessors, therefore nullifying attackers' attempts to phish for credentials.
Ransomware Protection

In Microsoft’s Digital Defence Report 2024, 389 US-based healthcare institutions were successfully hit with ransomware, which caused a range of issues, such as network and system downtime, critical medical operations delayed and appointments rescheduled.
When considering this, healthcare institutions should ensure that they are implementing adequate ransomware protection in order to prevent such occurrences, stopping files from being encrypted and held for payment.
As these attacks are often aimed at the most critical systems within healthcare networks, implementing AI-based threat detection and SASE solutions to isolate these systems, utilise a Zero-Trust architecture and find potential threats before they can encrypt files for ransom.
Regulatory Compliance (e.g., HIPAA, GDPR)
It’s important for network administrators within the healthcare sector to maintain regulatory compliance, an issue that is only emphasised by differences in regulations from one geographical region to the next. Our focus matrix below highlights on just some of the major differences in legislation between the UK and North America, with GDPR and NHS Digital guidelines providing the UK with the majority of their regulations and for North America HIPAA dictates US regulations and PIPEDA for Canada.
Different Aspects of Healthcare's Digital Protection Regulations From UK and North America
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Aspect | UK (GDPR, NHS Digital) | North America (HIPAA, PIPEDA) |
|---|---|---|---|---|---|---|---|
| 1 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Legislation Type | Comprehensive data protection (GDPR) with healthcare-specific guidelines (NHS Digital) | Healthcare-specific regulation (HIPAA) in the USA, and general data protection regulation (PIPEDA) in Canada, with adaptations for the healthcare sector |
| 2 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Scope | All personal data, including healthcare data handled by both public and private sectors | In the USA, applies to healthcare providers, insurers, and their business associates. In Canada, applies to all personal data, including healthcare data handled by commercial organisations |
| 3 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Data Sharing within Networks | Strict rules about sharing with third parties without explicit consent, NHS Digital oversees secure data sharing within NHS networks | Allows sharing of patient data for treatment, payment, and operations without explicit consent but requires safeguards in the USA. In Canada, allows sharing with adequate consent, organisations must establish policies for data exchange security |
| 4 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Data Encryption Requirements | Encryption is recommended under GDPR as a security measure, NHS Digital has strict guidelines for encryption to protect patient data during transfer | HIPAA mandates encryption of electronic Protected Health Information (ePHI) during storage and transmission, particularly in networks. In Canada, PIPEDA recommends encryption as a best practice for secure data exchange, focusing on minimising unauthorised |
| 5 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Data Breach Notification | Mandatory notification to the ICO within 72 hours for breaches, including those impacting healthcare networking | Mandatory notification to HHS and affected individuals without unreasonable delay, generally within 60 days, in the USA. In Canada, mandatory notification to the OPC and affected individuals is required when a breach poses a significant risk of harm |
| 6 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Patient Consent | Explicit consent is required for the processing of patient data, NHS Digital provides a framework for managing patient consent for data sharing | Implied consent is sufficient for treatment, payment, and operations in the USA, while written consent is needed for non-standard use. In Canada, implied consent is used for essential healthcare services, while explicit consent is needed for secondary use |
| 7 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Data Portability | Patients have the right to request copies of their data in a portable format, including healthcare records (applies under GDPR) | HIPAA guarantees patient access to health records, allowing digital copies if feasible, but no specific portability format is mandated. In Canada, PIPEDA requires organisations to provide access to personal data in an accessible format upon request |
| 8 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Third-Party Vendors | GDPR holds both data controllers (e.g. hospitals) and processors (e.g. vendors) accountable, Data Processing Agreements are required | Both HIPAA in the USA and PIPEDA in Canada require organisations to ensure third-party vendors meet privacy obligations. HIPAA mandates Business Associate Agreements (BAAs) for all third parties handling ePHI, whereas PIPEDA recommends contracts to ensure |
| 9 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Data Localisation | Data can be processed within the EU/EEA or other countries with adequate protection, special considerations apply to NHS patient data for security and privacy | No localisation requirements in the USA, patient data can be stored offshore provided HIPAA requirements are met. In Canada, there are no specific localisation requirements, but organisations must protect transferred data, including cross-border data shar |
| 10 | hyelland | 07/11/2024 02:42 PM | hyelland | 07/11/2024 02:42 PM | Interoperability & Standards | NHS Digital supports interoperability and data standards such as FHIR (Fast Healthcare Interoperability Resources) to facilitate secure networking between systems | Encourages interoperability through ONC standards and FHIR adoption in the USA, focusing on secure communication channels within healthcare networks. Canada also supports interoperability, often guided by provincial regulations, and generally follows FHIR |
Incident Response Planning

Whilst preventing breaches is ideal, it is unrealistic to expect that no breach will ever happen, especially with such a targetable asset such as a healthcare network containing patient data. This means that having a strong incident response plan is essential to minimising damage and impacts caused by a breach.
One example of this is leveraging AI for predictive analysis and real-time threat responses, allowing healthcare providers to minimise disruptions to patient care and restrict the volume of exfiltrated or ransomed data.
Another example should be a set of written instructions that outlines how network administrators should respond in the event of a security incident. The goal of the IRP is to limit potential damage that healthcare providers may face, including stolen patient data or equipment downtime.
Security Information and Event Management (SIEM)
A Security Information and Event Management (SIEM) solution is used to collect and analyse data security in order to monitor and respond to potential threats. More recent iterations of SIEM solutions have introduced Artificial Intelligence, which can more dynamically assess for potential threats, including zero-day threats, due to the ability to comprehend their actions and the threats they pose even if the exact threat-skillset hasn’t yet been seen before.
This is important for the healthcare industry as AI-powered SIEM protection can manage and analyse logs from connected medical devices/systems, allowing for identification of suspicious patterns before they get the chance to escalate.
Medical Device Patch Management
One of the main reasons that potential vulnerabilities and exploits arise is due to issues with firmware that becomes exposed over time. Typically, to rectify these issues, providers of the devices/software, release updates to patch over these exploits in order to maintain security. Unfortunately, these updates may not be automatically rolled out, which can lead to unmanaged vulnerabilities popping up over time within a healthcare network.
Whilst device patching can be managed by humans, we would argue that a more effective technique is to utilise AI-driven patch management tools to handle the bulk of the update management process, alleviating manual work and allowing for administrators to monitor patch management at a high-level.
By using AI-driven patch management tools, healthcare providers can ensure that connected medical equipment stays updated, reducing the risk of there being exposed vulnerabilities to attack/exploited.