What is Identity and Access Management (IAM) in Healthcare?
| IAM is essential for protecting patient data, maintaining regulatory compliance and preventing downtime to care systems. By integrating IAM with SASE (and SSE) solutions, healthcare providers can secure their systems while supporting remote and mobile services. |

Access control is arguably the most important factor for protecting sensitive information within Healthcare environments, allowing for compliance with industry regulations. The best way to implement this is via Identity and Access Management (IAM) solutions, which enforces privilege-based access systems to ensure that healthcare professionals can gain access to systems and data they require, meanwhile malicious actors and breaches are prevented access.
Table of Contents
In this article we discuss the core components of IAM within a healthcare environment, best practices for integration and explore case studies of how healthcare providers have used IAM solutions to better-comply with regulations.
Core Components of IAM in Healthcare
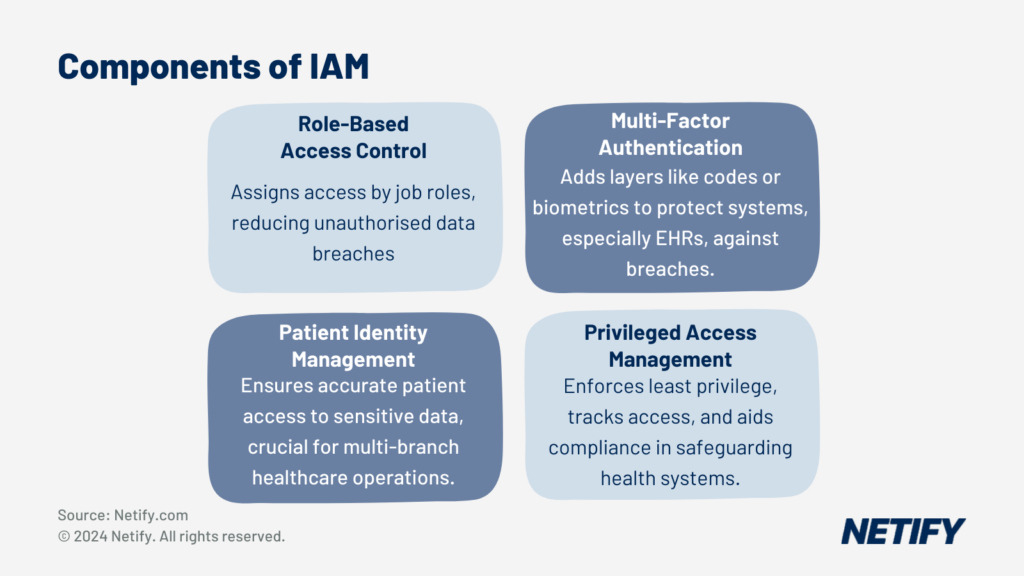
Role-Based Access Control (RBAC) in Clinical Environments
Identity and Access Management utilises Role-Based Access Control (RBAC) capabilities, enabling hierarchical privileges and access policies based on specific job roles. For example, a doctor would require different access to network resources in comparison to a receptionist/administrator.
By only providing access privileges to the resources necessary to allow professionals to fulfil their duties, healthcare providers can ensure that insider threats or breaches cannot access unauthorised patient data or systems.
A 2022 study found that hospitals using RBAC reduced incidents of unauthorised access by around 70%, emphasising the importance of leveraging RBAC and IAMs within healthcare environments.
Multi-Factor Authentication (MFA) for Protecting Patient Data
It’s common knowledge that a password provides basic protection for user accounts with the notion that having multiple passwords for an account would increase that protection.
Multi-Factor Authentication (MFA) adds multiple layers to the login process, such as using a password and an emailed/texted code or a fingerprint scan. By utilising further layers, MFA better-confirms a professional’s identity.
Healthcare settings often combine MFA with physical security measures, such as keycards, on top of passwords and authentication codes to maximise protection of their systems.
In practice, healthcare administrators should implement mandatory MFA measures in order for remote professionals to access systems such as Electronic Health Records (EHRs). This acts as a barrier to prevent healthcare services from breaches and ransomware, which typically target healthcare services.
Patient Identity Management
Many healthcare providers have begun providing patient portals, a way to view medical records, appointment booking and access healthcare services online. However, with this heightened accessibility comes greater risk.
To protect against this risk, Patient Identity Management (PIM) solutions ensure only the correct patient can access these details for improved privacy. This is particularly important when managing data across multiple healthcare branches, locations or telehealth platforms, where there are increased vulnerabilities.
Privileged Access Management (PAM) for System Administrators
Privileged Access Management (PAM) defines the policies behind access to health resources, including applications, specific network segments and patient health data. The principle of ‘least privilege’ is a fundamental of zero trust, ensuring only those who do need access, receive it and those that don't, cannot gain access.
To build upon access policies, PAM solutions also track all network activities, assisting healthcare providers to prevent misuse. Logging exactly what goes on can be especially important for network administrators in the healthcare industry to put remediation plans into place in the event of a breach or to meet regulatory requirements.
Integrating IAM with Healthcare Systems
Healthcare systems are typically spread across multiple interconnected platforms, such as EHRs, laboratory systems and Internet of Medical Things (IoMT) devices.
By utilising so many platforms, vulnerabilities tend to arise and therefore network administrators need to prevent these from being exploited.
IAM solutions help manage access to healthcare systems, ensuring data is securely shared without causing delays or downtime for professionals. The integration of IAM is therefore arguably essential in environments where multiple systems and devices work together to deliver a converged patient care service.
IAM’s Role in Protecting Healthcare Networks
In a healthcare network environment, the aforementioned ransomware are not the only attacks typically faced. Due to the volume of sensitive personal information, such as patient and care data, healthcare organisations are also at an increased risk of facing phishing and other attacks.
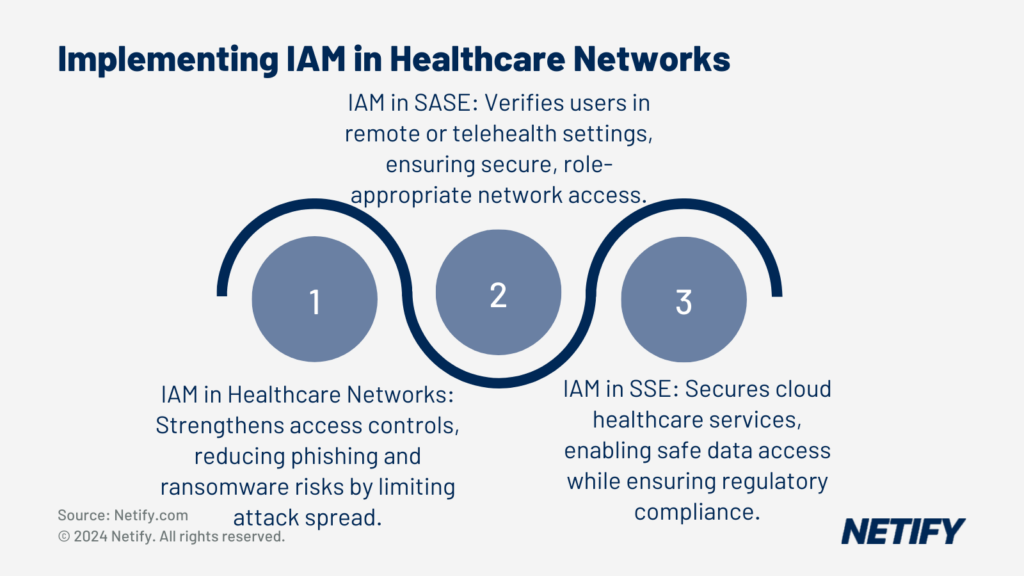
The implementation of an IAM can help to reduce the risk that these threats pose, providing more stringent access to both internal and external networks, minimising the effectiveness and lateral movement of these attacks.
IAM in Secure Access Service Edge (SASE)
One solution that can leverage IAM as a capability is Secure Access Service Edge (SASE). SASE is used within healthcare environments in order to connect remote clinics, mobile teams, and telehealth services. IAM ensures that users logging in from a range of devices or locations are verified and granted the appropriate access.
IAM in Security Service Edge (SSE)
However SASE utilises SD-WAN in order to provide the access portion of its name. Without the necessity for this access component, healthcare providers can alternatively utilise Security Service Edge (SSE). SSE focuses primarily on the security functions of networking, supporting cloud-based healthcare services by authenticating users and controlling their access to data stored online. IAM systems integrated with SSE allow healthcare providers to use cloud platforms safely, while meeting requirements like HIPAA compliance.
Healthcare-Specific IAM Case Studies
Preventing Ransomware in a Regional Health Network
In May 2021, Ireland's Health Service Executive (HSE) experienced a ransomware attack that disrupted hospital operations nationwide. The attack led to the cancellation of outpatient services and significantly impacted patient care.
Due to this attack, HSE decided to implement IAM in order to prevent re-occurring issues, with features including multi-factor authentication, role-based access control and privileged access management. The introduction of IAM, alongside this feature set, allowed HSE to ensure users verify themselves before gaining system access, ensured that roles were aligned with job duties and minimised sensitive data access, whilst those with elevated privileges were monitored to reduce the risk of internal threats.
As a response to a prior attack, HSE has now made their network much more secure, making sure that access is more tightly controlled in future, which should help minimise the risk of a future attack.
Expanding Telehealth at a Large Provider
During the COVID-19 pandemic, a large healthcare provider in the United States expanded its telehealth services to accommodate a surge in remote consultations.
However, by introducing a large volume of remote consultations meant that their traditional network were becoming overwhelmed and a SASE solution was needed in order to improve network performance. Further to this, by moving to a cloud platform rather than using a centralised data centre, the healthcare provider had to introduce security measures to protect against newly found vulnerabilities.
Implementing an IAM solution meant that secure, role-based access could be provided to cloud-based telehealth platforms, ensuring that only authorised professionals could access specific services.
Reducing Insider Threats in a University Hospital
Our final case study, a university hospital, identified instances where professionals had accessed patient records without proper authorisation. Whilst nothing official was reported to have come of this, the potential risks to patient privacy and data security that this posed necessitated that the university hospital put measures in place to prevent it from happening again.
To address the issue the hospital utilised privileged access management within an IAM solution in order to control and monitor access for users with elevated privileges. This meant that only authorised personnel could access sensitive information, prevent future issues from reoccurring.
Further to this, the university hospital also used the report generation functions within IAM in order to get audit-ready logs so that they could regularly scan through to ensure that no other issues had arisen.
Compliance in Healthcare
For network administrators, one of the more daily challenges is ensuring that their healthcare network complies with industry regulations. With a range of new systems being continuously integrated, it can be difficult to ensure that each one of them not only works in tandem with other systems, but also meets the security demands for legislation and regulatory purposes.
Given that these systems may not have any innate security features built in, IAM systems can be leveraged as a bolt-on in order for the healthcare industry to comply with regulations.
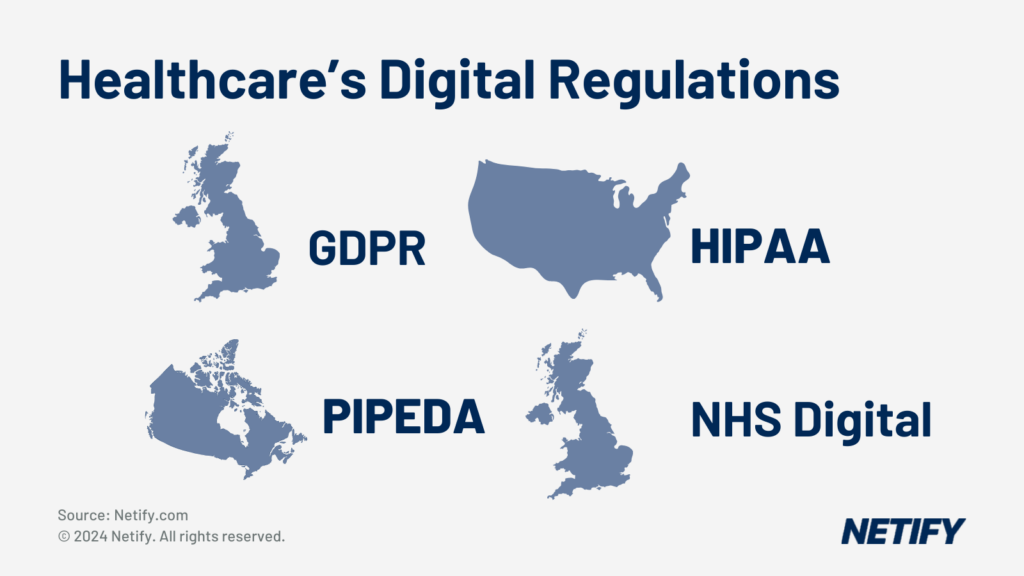
Some of the more notable healthcare regulations that this is applicable to are:
HIPAA (US):
Ensures only authorised personnel can access patient data and maintains records for audits.
GDPR (UK & Europe):
Protects sensitive data, particularly in cross-border healthcare settings.
HITECH Act (US):
Extends HIPAA requirements by requiring detailed tracking of who accesses electronic health records.
Challenges of IAM in Healthcare
There are many challenges when implementing IAM within healthcare networks:
Diverse User Groups
Within a healthcare environment, not all of the workforces share the same responsibilities. Healthcare organisations must manage the intricate differences in access that these roles require. For example, there should be access differences for full-time, part-time and temporary professionals, preventing out-of-hours access. Further to this, both contractors and patients may have to use healthcare systems but they should be isolated on the network with the smallest access possible due to the outside threat they pose. When implementing an IAM within these types of environments, solutions need to cater to these groups without slowing down operations.
Legacy Systems
Whilst in this article we previously referred to IAM being used as a bolt-on, this doesn’t always account for issues in integrations with older systems. These issues make implementation more difficult and therefore network administrators in the healthcare industry should consider all of their systems, what their limitations are and what infrastructure may need to be updated prior to rolling out IAM.
3. Securing IoMT Devices
There’s no doubt that Internet of Medical Things (IoMT) devices have made monitoring care much easier for professionals. However, connected medical devices, such as patient monitors and infusion pumps, can be vulnerable to cyberattacks. IAM can be introduced for IoMT, acting as a bolt-on solution, to help secure these devices by enforcing authentication and access controls.
Conclusion
IAM is essential for protecting patient data, maintaining regulatory compliance and preventing downtime to care systems. By integrating IAM with SASE (and SSE) solutions, healthcare providers can secure their systems while supporting remote and mobile services.