What is SASE (Secure Access Service Edge)?
| SASE adds SD-WAN for access to the security of SSE. Offering increased access capabilities and the security of Cloud Access Security Broker (CASB), Firewall-as-a-Service (FWaaS), Secure Web Gateway (SWG) and Zero Trust Network Access (ZTNA). |
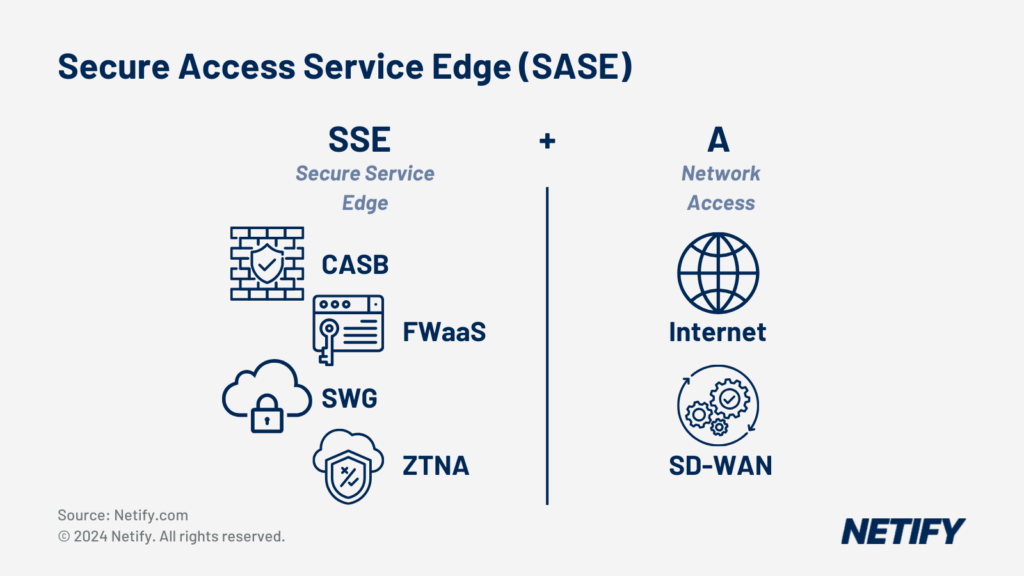
Secure Access Service Edge (SASE) is a networking framework designed to converge several networking features. SASE is cloud-native, therefore residing within the cloud and integrates extensive WAN capabilities with built-in security. This direct cloud connectivity enables features such as Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), Zero Trust Network Access (ZTNA) and Firewall-as-a-Service (FWaaS), all within a singular unified platform.
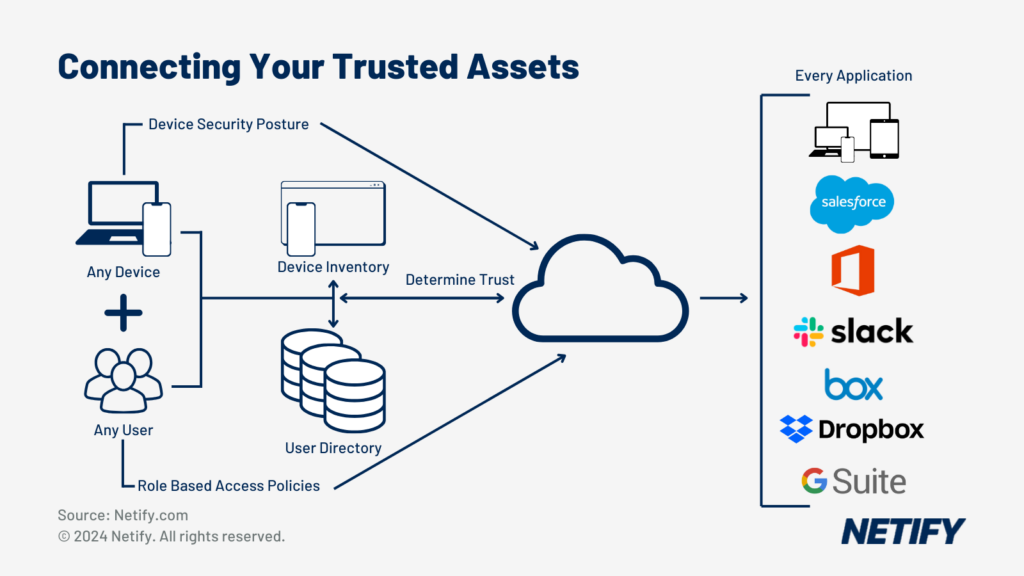
By unifying these features, SASE enables efficient connections across distributed and remote sites, providing access to the system based on identity not the connection origin location. This factor means that SASE supports all network edges, providing users with a seamless user experience (UX), whilst reducing the complexity for network administrators and enabling access to the cloud for effective use.
Evolution of SASE
Traditionally, networks used a centralised data centre and routed all network traffic via this centre. However, following the emergence of working from home and distributed networks, there has been a greater emphasis to move network perimeter to a decentralised location. The dynamic, cloud-native approach that SASE offers means that networks that move to the cloud can rapidly scale whilst still maintaining flexibility.
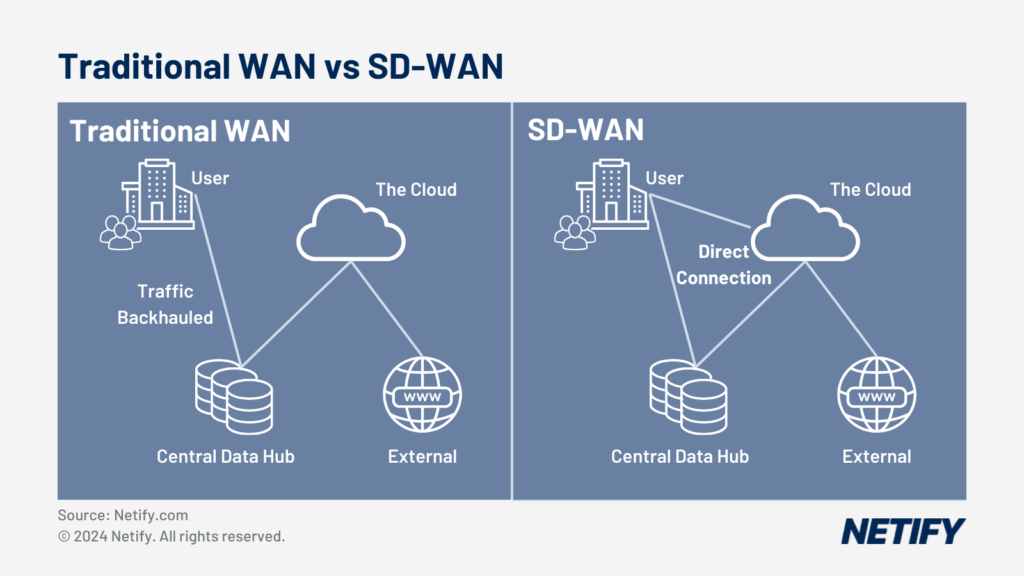
Prior to SASE, as there was no longer the secure perimeter with distributed working a “hub-and-spoke” model was used, meaning that network traffic had to be backhauled to the central data hub for inspection and all network policies were applied and enforce using on-premises appliances.
Remote working, Bring Your Own Device (BYOD) policies and cloud expansion showed the limitations of traditional networks through degraded network performance, poor user experience and an expanded attack surface (via VPN usage). SASE rectifies these issues and by leveraging microservices, using global Points of Presence (PoPs) for enabling nearby security checking, allowing the integration of security and policies such as authorising based on identification and not device. SASE also uses a central policy management strategy, which ensures that policies and permissions remain consistent across the system.
Core Components of SASE
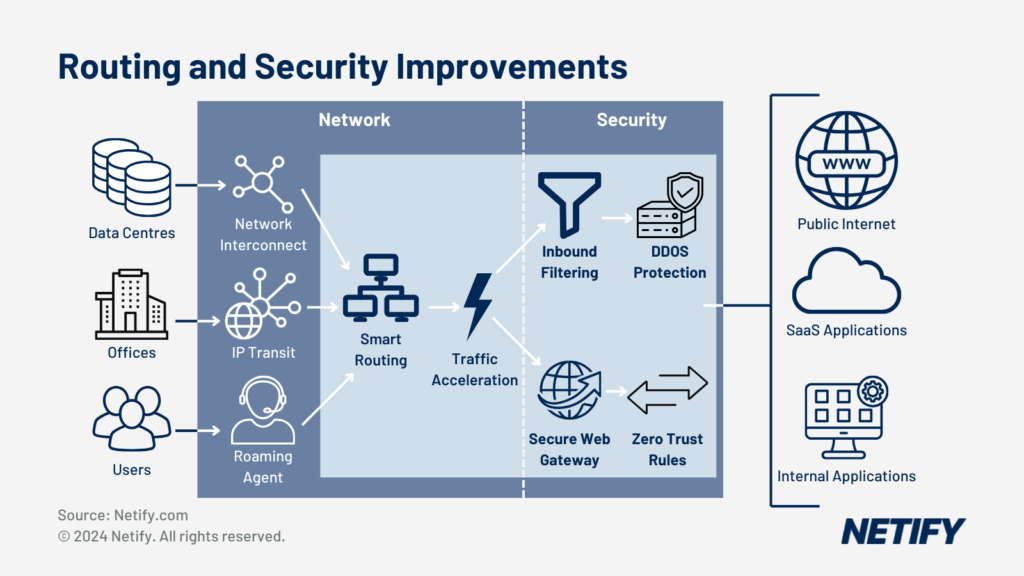
The core elements of SASE include:
SD-WAN (Software Defined Wide Area Network) is used to simplify the management of a network by providing automated traffic routing over several network links, a centralised dashboard for controlling user access, policy management and cloud integrations. SD-WAN facilitates direct cloud access from branch offices, removing the need to backhaul data from branch offices, and reduces WAN costs by utilising low-cost local internet. Due to these improvements, SD-WAN offers better cloud application performance by enhancing the routing of critical traffic.
FWaaS (Firewall-as-a-Service) simplifies moving firewall utilities to the cloud. FWaaS is scalable and can be managed via a centralised cloud control panel ensuring consistent policies across larger networks. FWaaS is often integrated into SD-WAN, reducing operational costs when compared to traditional firewalls as the scalability removes the need for over-provisioning resources.
SWG (Secure Web Gateway) monitors potential web-based threats and controls traffic through URL filtering, malware detection/prevention, application control for cloud apps, SSL/TLS decryption and inspection and user activity logging.
CASB (Cloud Access Security Broker) extends the visibility and control over network data within cloud applications. The 4 pillars of CASB are visibility into cloud application usage, ensure compliance with all regulations, protect data through access control and data loss protection (DLP) and provide threat protection (such as AI anomaly monitoring).
ZTNA (Zero Trust Network Access) provides least-privilege access to devices on the network, ensuring the security of the network by continuously verify the user before continuing authorisation.
AI and Machine Learning Innovations in SASE
SASE has seen Artificial Intelligence (AI) and Machine Learning (ML) innovations become integrated. One such case is the use of AI and ML to detect risks to the network via anomaly detection which can be done in real-time. This is an automated process which evaluates user behaviours, privileges, and network actions to find threats and then issue the appropriate incident response.
Due to AI and ML using big datasets, with some vendors collating threat data across organisations, the anomaly detection is able to identify day-zero threats such as malware intrusion and suspicious activity that traditional systems may not pick up on. AI systems can also adapt the network security policies to combat new threats, reducing the workload on network administrators whilst optimising the network performance. By enhancing the security posture and optimising performance, AI benefits the user experience.
Strategic Benefits of SASE
SASE reduces the complexity of network architectures and the amount of administrative overhead by unifying functions. This means that there is less overhead required to configure, integration, monitor and troubleshoot a network. By converging systems into a singular framework, SASE reduces costs, improves system efficiency, and allows hybrid systems of on-premises and remote work to have consistent policies and experiences.
The implementation of SASE emphasises the use of a single vendor for all networking solutions, removing the need for multiple separate appliances/licenses for SD-WAN, firewalls, Secure Web Gateway (SWG) and Virtual Private Networks (VPNs). As SASE is cloud-native it allows organisations to scale their network, including all of these security capabilities, making the scaling process easier and reduces the need for overprovisioning. This further reduces operational costs and resources can be managed automatically through the cloud.
Furthermore, as SASE integrates many technologies, users benefit from intelligent traffic routing, WAN optimisations, local security policies to minimise latency through PoPs and the ability to offload internet bound traffic locally.
The enhanced security posture that integrated Zero Trust Network Access (ZTNA), Secure Web Gateway (SWG), Cloud Access Security Broker (CASB) and Firewall-as-a-Service (FWaaS) provide, means that the networks expose less attack surface to potential threats to get into the network and there is granular control to ensure any breaches are contained. The use of identification-based policies rather than device or location based policies maintain security whilst enabling mobility for users, whilst universal policies for traffic inspection and threat prevention ensure the security of the network no matter what device is connected or where the device is connecting from.
SASE also simplifies secure access for mergers and acquisitions. Due to SASE being cloud-native, no physical changes are required to the architecture, and this means that organisations can quickly onboard new users and branch locations. The acquired company’s users and devices can easily be ported across to the SASE platform to enable secure access and the use of consistent policies within SASE reduces additional privilege management for these new users.
Case Studies and Implementation Examples
Focus Services, a global third-party call centre provider introduced SASE at the start of the Covid-19 pandemic. This enabled Focus Services to quickly deploy secure remote access to their 500 remote users, which was previously not possible with their legacy equipment. This also reduced the cost and complexity of their MPLS network whilst providing reliable access throughout distributed locations, including those with poor internet connections.
A fortune 2000 enterprise with 97 global sites and over 2500 users deployed SASE for on-premises and cloud users, causing a 20% improvement in security policy agility, 200% improvement in application performance, 60% reduction in latency and allowed IT administrators to focus more on strategic planning than manually administering system security.
Future Outlook and Emerging Trends
Emerging trends show that SASE vendors have begun implementing advanced threat prevention to further protect networks (in the form of antivirus, antimalware, url filtering and file sandboxing). These techniques utilise Artificial Intelligence and Machine Learning in order to combat zero-day threats via the use of analytics and real-time intelligence sharing across enterprises to pro-actively prevent attacks.
There has also been an uptake in SASE offering secure Internet of Things (IoT) and edge computing. This has come in the form of SASE vendors introducing IoT support with no additional hardware, meaning that one singular vendor for SASE can cover and act as the default security framework for a network.