What is ZTNA (Zero Trust Network Access)?
| Zero Trust Network Access is a security capability part of SD-WAN & SASE architectures, requiring users to constantly authenticate themselves to gain access to network resources. |
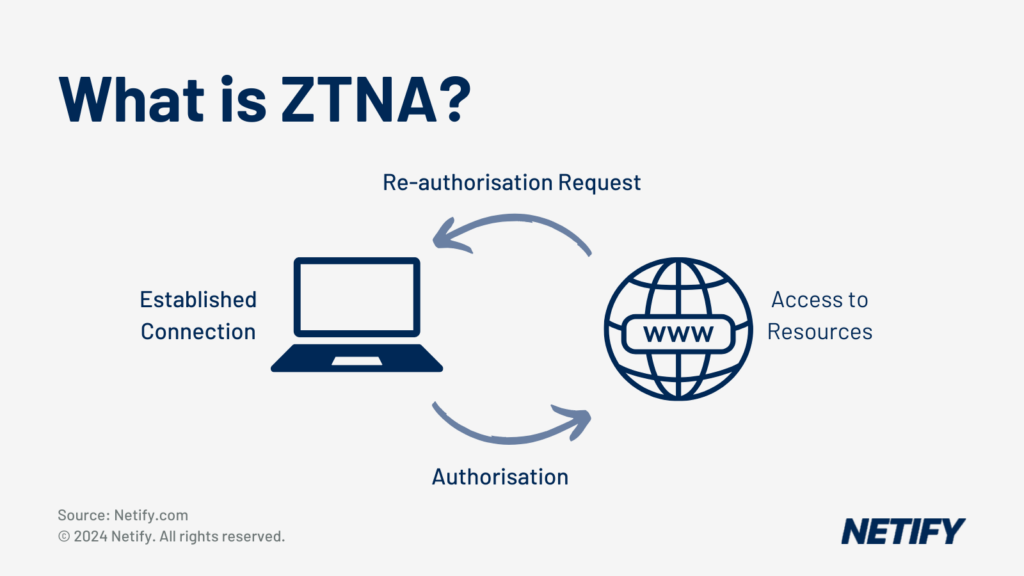
The term Zero Trust Network Access (ZTNA) is a security principle that defines that networks should “never trust, always verify”. With ZTNA, the network assumes that no device, user, or physical connection should be inherently trusted by the network and so these all require constant authentication to initially gain but also to maintain access to the network at every interaction.
ZTNA has become more prevalent over recent years, where more businesses are practising remote or hybrid work. These new work locations extend the boundary of the business network from a traditional on-site premises to areas such as user’s home networks, where the security may not be so secure. Due to this, where traditional networks relied on firewalls and VPNs to bridge the gap between branch office networks, remote work across a range of locations requires access to the cloud and so these alone are no longer sufficient.
Core Concepts
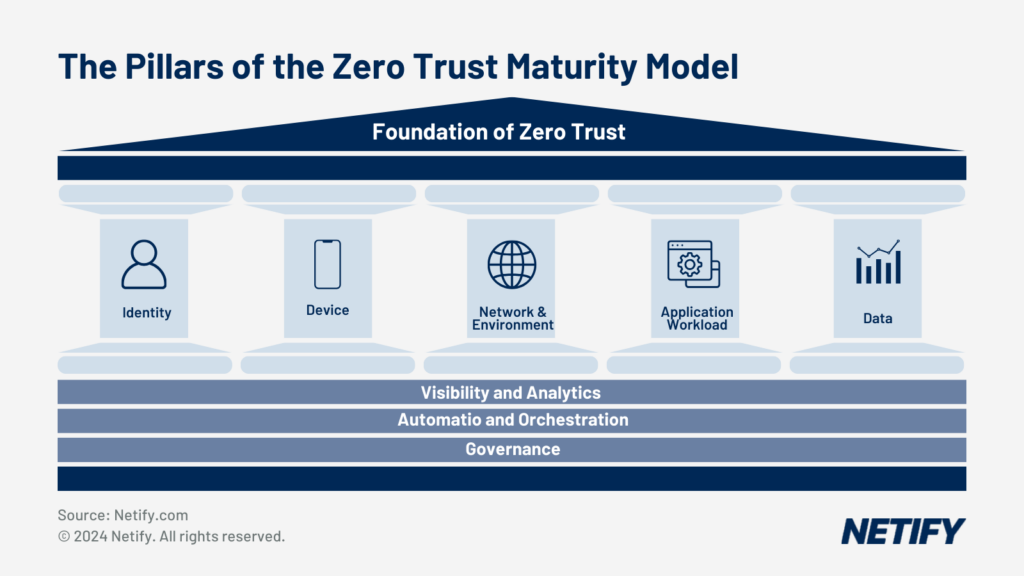
The strict verification process implemented by ZTNA must be adhered to both inside and outside of site premises. This not only maintains consistency for network usage but also adds an additional layer of security for connections from on-site connections.
Zero Trust Network Access uses Multi-Factor Authentication (MFA). This combines authentication techniques such as a password, text code, email code, or graphical password in order to ensure there is plenty of proof the user is who they say they are prior to authorisation of access.
Once authorised, the actions a user can take are controlled via an Identity and Access Management (IAM) system. Within this, users can be created, maintained, and managed via granular access controls, enabling administrators to set strict policies based on user attributes, roles and risk. Zero Trust states that within an IAM, it is important to implement the Principle of Least Privilege (PoLP), where users are only given the minimum amount of permissions in order to complete their actions. In the event of a breach, this granular-level control prevents spread across the network from the source of the breach.
ZTNA acts on a pre-session basis, meaning that users have to re-verify between sessions. ZTNA acts as a broker for this between the user and the application, meaning that there is less attack surface than via a VPN to the overarching network, should there be a breach.
Emerging Trends
An emerging trend within ZTNA is the introduction of Artificial Intelligence (AI) and machine learning (ML). These technologies are being used to analyse data such as user behaviour and device posture amongst many other factors to determine user authentication and continuously assess potential risks to the network.
Managed services for ZTNA are becoming more prevalent, offering a vital role in helping organisations implement ZTNA, reducing not only the network architecture requirements but also reduces the requirement for knowledgable staff. These services are making ZTNA more accessible to a broader range of businesses and allow for businesses without technical knowledge to still adopt advanced cybersecurity capabilities into their network infrastructure.
Challenges in Implementation
When implementing ZTNA, network administrators may need to integrate existing technologies which may not all be compatible. This issue is made more complex in networks where legacy systems using outdated components are required. This means that network administrators will need to consider compatibility prior to implementing ZTNA.
Due to ZTNA relying on applying strict policies to users, it is important that network administrators continuously manage and change network policies in order to balance resources, critical system access and the risks to the system. Reducing access can affect User Experience (UX) as it may slow down productivity but increasing access may pose threats to the network. It is therefore important to consider the cybersecurity skills of network administrators to ensure this balance does not become negatively affected.
Advanced Use Cases
ZTNA is a crucial element for securing cloud environments. By providing direct and secure access to cloud-hosted applications, ZTNA prevents cloud-hosted applications from being publicly accessible and reduces the risk of these systems being attacked.
ZTNA is a component of SASE, which combines networking and security functions into a singular cloud-native platform. By integrating ZTNA into SASE, alongside components such as Next-Generation Firewall (NGFW) and Secure Web Gateway (SWG), businesses are able to provide their users with a flexible and manageable way of connecting to cloud systems whilst also maintaining comprehensive security.
ZTNA 2.0 is an advancement in the Zero Trust model, focusing on continuous verification and security inspection of network connections in order to address the complexity of modern networks. This advancement further highlights the importance of granular identity management and security controls.
Future Directions
As ZTNA is being adopted by more and more businesses, the emergence of ZTNA-specific roles has also increased. Roles such as “Chief Zero Trust Officer” and “Zero Trust Czar” are responsible for bridging the gaps between security and network operations and driving the ethos of Zero Trust across all company systems. These ensure that all systems and administrators are aligned around zero trust goals.
ZTNA is becoming foundational within SASE/SSE integrations and so tighter integrations are being seen across the market. ZTNA is also adapting by integrating AI and ML for automated and adaptive policy enforcement, reducing the complexity and requirements of work for IT administrators. ZTNA is expected to incorporate more advanced features such as remote browser isolation (RBI) and additional API security, which further enhance the security posture of any organisation using ZTNA.
ZTNA is growing in importance to cybersecurity, enabling flexible, granular user management, enhancing user experience, and preventing threats from spreading between systems on the network. As uptake increases, it is anticipated that future regulations may require the introduction of zero trust principles in sectors that handle sensitive data (such as finance and healthcare), therefore ZTNA is an excellent way for businesses to be prepared for any new regulations.
Conclusion
Zero Trust Network Access has emerged as an essential security framework for any organisation catering to remote, hybrid or distributed work forces. By mitigating the threats posed by moving the network boundaries to less secure locations, ZTNA allows greater flexibility and scalability for network architectures.
The core principles of “never trust, always verify” ensure that users only get minimal access to the network and reduces the potential attack plane for breaches, thus reducing overall threat to the network.
With increasing integrations into technologies such as the SASE framework, ZTNA has become a foundational element to network architectures and for managing user control. Organisations that adopt ZTNA into their network architecture will be well positioned to protect their applications, data and enable secure connectivity for their workforce regardless of the location or device.