| SD-WAN helps manufacturers navigate complex compliance regulations by improving network security, enabling data segmentation, and supporting real-time monitoring. |
With the ever-growing quantity of regulations faced, manufacturers are beginning to question the best routes to achieve compliance. One innovation that can be key to manufacturers compliance strategy is Software Defined Wide Area Network (SD-WAN) solutions.
Manufacturers are becoming more digitised, meeting industry demands by utilising a connected network of production lines, sensors and applications for increased productivity. Complex laws that mandate safety, environmental sustainability and ethical business practices are just a few types of regulations that can put barriers on this digitisation and, without the right plan, manufacturers may face great difficulty complying.
Introducing SD-WAN over a traditional WAN network helps remedy this issue, whilst also improving connectivity, providing segmentation capabilities, optimised performance and increased cost efficiencies. This article explains why SD-WAN must be considered by manufacturers and details the common considerations to determine prior to selecting a vendor.
Regulatory Frameworks Relevant to Manufacturing
Data Protection Regulations
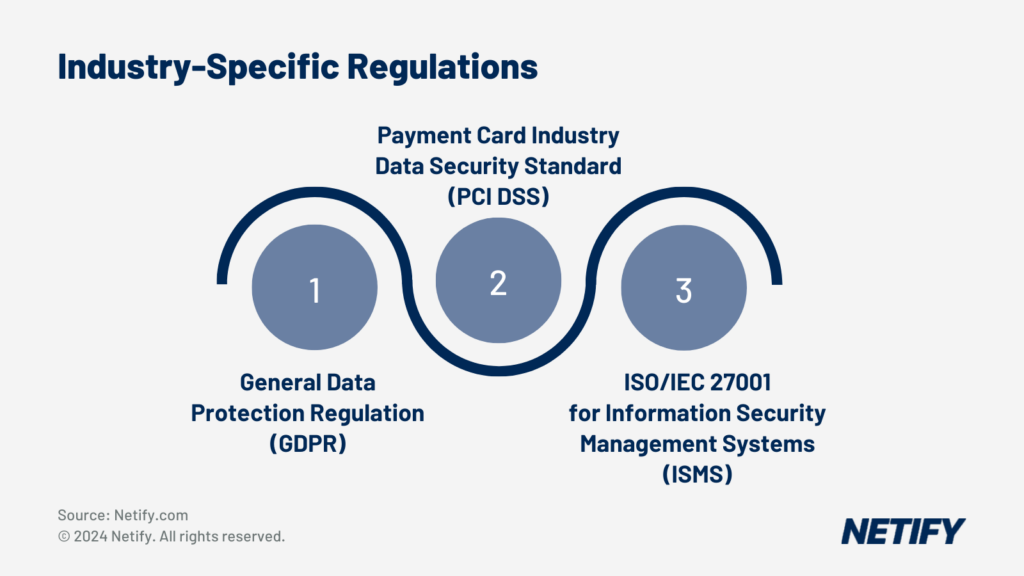
The General Data Protection Regulation (GDPR) has undoubtedly had a significant impact on businesses. This introduced an emphasis on the need to gain consent and securely process personal data, such as machine data showing individual operator performance, personnel data on number of employees, time worked and productivity of each employee. Not only do manufacturers have to securely process this data, but they also must offer the ability for individuals to access, rectify and erase their personal data. For EU-operating manufacturers, non-compliance with GDPR can result in large fines.
Manufacturing Regulations
Another regulation that manufacturers typically face is the Payment Card Industry Data Security Standard (PCI DSS), which mandates that businesses install and maintain security features such as firewalls, encryption and anti-virus are configured to protect cardholder data. Due to being payment details, access to the data must be restricted to a need-to-know basis, and any access must be track and monitored in the event of any future investigations into malicious activity.
Industry-Specific Regulations
There are many industry-specific regulations that can apply to manufacturers, one of which is the North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) Standards. This regulation states that security must be in place for manufacturers connected to the North American power grid, which can include establishing a baseline set of cybersecurity measures for regulating, enforcing, monitoring and managing the security of the North American Bulk Electric System (BES). These measures include identification, security management, incident reporting, configuration management, information protection, supply chain security and physical security, which requires the identification of critical assets and regular risk assessments to be performed. Once these assessments are completed, manufacturers must define their policies for monitoring, who can access and maintain proof of compliance in the event of an audit.
Manufacturers have to abide by a range of environmental regulations, which can be mandated at local, national or even international level. The Clean Air Act is in place to regulate air quality and pollution with emission standards, whilst the Clean Water Act is in place to measure the impact of manufacturing operations on water supplies. Manufacturers also have to adhere to the Resource Conservation and Recovery Act (RCRA) which regulates the management of hazardous waste, whilst emerging regulations have added requirements for energy efficiency and sustainability reporting.
These regulations all require heavy amounts of monitoring and reporting mechanisms, which has arguably caused the rapid growth of Internet of Things (IoT) devices, which include components such as sensors in order to detect if operations meet these regulatory metrics. However, IoT comes with its own security considerations that manufacturers should be aware of.
Security Considerations
Whilst sensors and Internet of Things devices can assist with the tracking of these metrics to ensure compliance, these devices also come with their own regulatory implications. For example, the logical separation of industrial systems from enterprise networks is mandated by the Industrial Control Systems (ICS) for ISA/IEC62443. However, the segmentation capability offered by SD-WAN is a key improvement over traditional WAN networks and applies policies to control access, privilege and functionalities for specific zones of the network. Segmentation is essential for enabling innovations such as Internet of Things (IoT), the integration of sensors and analysis components, as IoT hardware is often incapable of hosting its own security functionality on-board, and also provides a logical separation from the rest of the network, helping to meet regulations.
Segmentation can also be utilised to restrict user access to only the data they need access to, such as preventing quality control, warehouse, management and supply chain teams having access to each-others resources. This restricts any data leak or security breach from affecting the entire network and contains it within a small partition, preventing loss of intellectual property or damage from espionage and other malicious actors.
SD-WAN isn’t only limited to segmentation though and often comes with features such as Next-Generation-Firewall (NGFW) and Intrusion Prevention Systems (IPS) for protecting against breaches, Cloud Access Security Broker (CASB) and Secure Web Gateway (SWG) for secure integrations of cloud service utilisation and IPsec and AES for encrypted data transfer, improving confidentiality and protecting business intellectual property. This means that SD-WAN enables compliance via industry standards and regulations, encryption and tunnelling for data protection requirements like NIST 800-53 and NIST 800-82 for ICS.
Compliance with International Standards
ISO/IEC 27001 is the leading international standard for information security management systems (ISMS). It provides a framework for establishing, implementing, operating, monitoring, reviewing, maintaining and improving an ISMS. ISO 27001 is required by manufacturers to help protect confidential information and intellectual property. The regulation covers security of digital information, paper documents, knowledge of employees, physical assets like computers and networks and takes a risk-based approach to information security. Gaining ISO 27001 certification demonstrates to customers, partners and stakeholders that a manufacturer’s information security meets global standards.
The NIST Cybersecurity Framework provides a policy framework of computer security guidance for how manufacturers can assess and improve their ability to prevent, detect, and respond to cyber attacks. It has a strong focus on protecting critical infrastructure and provides a set of standards, guidelines and best practices to help manufacturers better manage and reduce risk. This enables manufacturers to align their network security activities with business requirements, risk tolerances and resources, whilst focusing risks as part of the organisation’s network management processes. NIST is therefore applicable for manufacturers of all sizes, degrees of cybersecurity risk, or sophistication and complements, rather than replaces, an organisation’s existing cybersecurity methodology and risk management processes.
Continuous Monitoring and Reporting
SD-WAN Monitoring and Reporting for Manufacturers
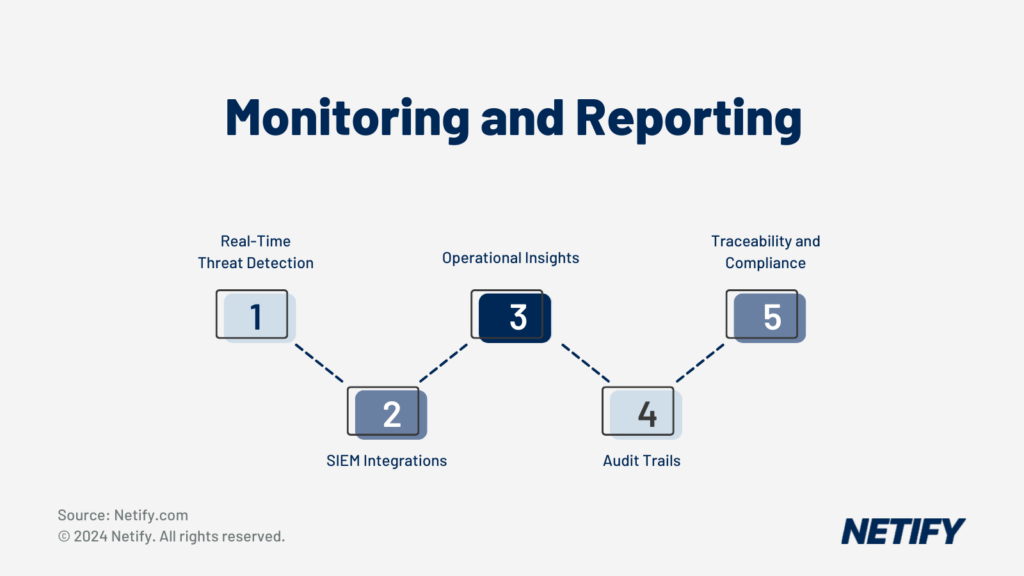
Real-time monitoring and reporting mechanisms are crucial for manufacturers to detect and mitigate potential threats to production and design. By continuously monitoring network activity, connected devices, critical systems and identifying anomalies, manufacturers can quickly detect security incidents or operational issues in order to rectify them. One way that SD-WAN handles this is through Security Information and Event Management (SIEM) system integrations, which enable the aggregation and logging of data from various sources in real-time and applies machine learning to flag suspicious or abnormal activity. This real-time monitoring of operational metrics provides manufacturers with insights such as equipment performance, productivity output and quality control effectiveness, which enables proactive maintenance and optimisation of production lines. This data-driven approach can be pivotal to manufacturers gaining an advantage over competitors and strengthens the position of SD-WAN as a key asset to production.
Audit trails capture chronological records of system activities, changes and events, which can provide documented evidence of what occurred, when, where and by whom. The granular-level of detail that SD-WAN reports, provides manufacturers with an automated level of logging, reducing the complexity for meeting the needs for audit trails. This traceability is critical for manufacturers in regulated industries, as regulations such as FDA 21 CFR Part 11 require electronic records and signatures to be kept for accountability purposes.
Vendor Considerations
When selecting an SD-WAN vendor, manufacturers must ensure that the vendor complies with relevant standards and certifications, such as FedRAMP for US government-related manufacturing. The Federal Risk and Authorisation Management Program (FedRAMP) is a key compliance requirement for cloud service providers that work with US federal agencies. FedRAMP provides a standardised approach to security assessment, authorisation, and monitoring for cloud services. For manufacturers that are US government contractors or subcontractors, choosing an SD-WAN vendor that is FedRAMP authorised helps ensure compliance with federal security requirements. One vendor that recently achieved FedRAMP Authorisation to Operate (ATO) is Cisco for its cloud-based SD-WAN for Government solution.
Another consideration is the interoperability of each SD-WAN vendor’s offering, due to the integration with existing network infrastructure often being rather complex, especially if legacy systems are from multiple vendors. Incompatibility can cause issues with already-present compliance reporting and monitoring tools, therefore, to maintain audit trails and adherence to regulations, manufacturers must consider the interoperability of potential SD-WAN solutions with their own business network. This is due to varying levels of support for firewalls, intrusion detection/prevention and SIEM and requires any chosen SD-WAN solution to provide service chaining to these security functions.
Risk Management and Mitigation
Compliance with many regulations requires manufacturers to apply security measures, forming a risk management and mitigation plan. One way of integrating these are advanced threat detection technologies, such as intrusion detection and prevention systems (IDPS), which are integrated with SD-WAN solutions to identify and respond to potential security breaches. SD-WAN utilises Artificial Intelligence (AI) and Machine Learning (ML) to analyse large volumes of data from various sources, such as network logs, endpoints and cloud services, helping to identify potential threats. AI enables manufacturers to detect subtle patterns and outliers that may indicate an attack or operational outage, that human-management may be unable to detect.
Developing and regularly testing incident response plans is essential to comply with regulatory requirements and minimise the impact of security incidents. SD-WAN can help streamline incident response by providing centralised management and control, as centralised management enables full visibility into network traffic. Enhanced analytics and reporting allow rapid responses of configuration changes and security policies to contain threats, which is further improved by SD-WAN solutions ability to automate many of the network management processes. By dynamically responding to changing network conditions and minimising the need for manual intervention. This reduces the workload for network administrators, whilst also reducing the need for trained on-site staff to handle network management, meaning that businesses can save costs through a reduced administrator workforce.
Case Studies and Best Practices
A leading European dairy manufacturer implemented Cisco SD-WAN across 90 sites to improve network agility, simplify management, and ensure compliance. This meant that they could segment their traffic, mapping virtual networks between factories and data centres to improve their security capabilities and meet data protection regulations, such as GDPR.
An American manufacturer integrated Fortinet SD-WAN in order to achieve Cybersecurity Maturity Model Certification (CMMC) and retain large defence contracts. The Fortinet Security Fabric, part of the SD-WAN offering and integrations, provided the manufacturer with the ability to monitor, mitigate and report on threats to facilities, which aligns with the NIST Cybersecurity Framework as required for CMMC. The benefits of SD-WAN were also felt by the teams responsible for network management, with a Significant reduction in time spent managing devices, which made resources available to work on compliance rather than management tasks.
Future Trends and Innovations
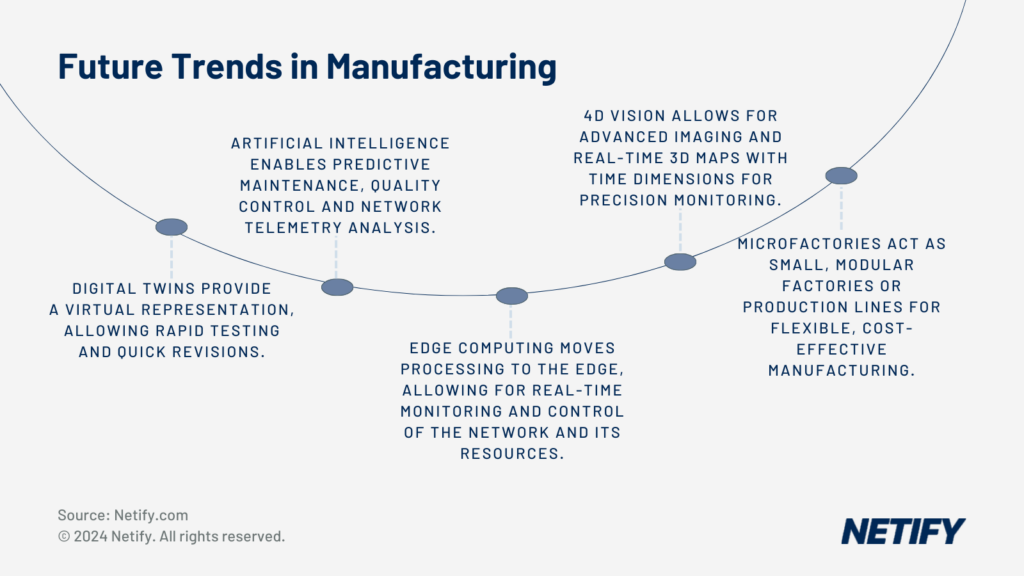
Recent innovations in SD-WAN capabilities is the introduction of monitoring and maintaining regulatory compliance by leveraging Artificial Intelligence. AI can continuously monitor network activity and configurations against predefined compliance policies, such as NIST, ISO, NERC CIP and any deviations can trigger automated alerts and responses to ensure consistent adherence to industry regulations and standards.
Future Trends within the Manufacturing Sector
Another innovation is the introduction of Edge Computing, which enables integrations such as Internet of Things components and sensors to be utilised within production lines. These devices form smart manufacturing environments but, due to their lack of inbuilt security measures, come with new compliance challenges. Edge Computing allows SD-WAN processing to be shifted to the network edge rather than centrally and these capabilities directly on IoT gateways and edge devices allows extending compliance policies and monitoring to the network edge. This ensures that edge devices adhere to the same rigorous standards as the rest of the network and assists in the process of meeting regulatory compliance.
Conclusion
As the number of regulations increase for manufacturers, solutions such as SD-WAN where compliance mechanisms are built-in or offer integrations to assist with compliance, have become in-demand. By adopting an SD-WAN approach, manufacturers can gain a strategic advance for enhanced connectivity, performance and security benefits and improve compliance for regulations such as data protection, environmental or industry-specific laws. The integration of Artificial Intelligence and edge computing has broadened the capabilities of SD-WAN to further ensure compliance and operational efficiency going forward.