| When choosing SD-WAN for manufacturing, consider performance, reliability, security, scalability, and compatibility with legacy systems to ensure seamless, cost-effective, and secure network management. |
The manufacturing sector faces many networking challenges, including high reliability and uptime requirements, integrations with legacy systems, support for geographically dispersed locations and ensuring strict security is enforced. As network downtime can lead to financial loss, halts in production and disruptions to supply chains, it is essential for manufacturers to find a network solution to prevent potential issues. The best solution for this is Software-Defined Wide Area Network (SD-WAN), which can not only address these challenges but also optimise network performance within your manufacturing environment.
How to choose an SD-WAN for Manufacturing
This page details the significance of SD-WAN solutions within the manufacturing sector, the common challenges that SD-WAN can resolve and the best practices for deployment. The integration of SASE/SSE is also covered, with pricing details and real-world case studies used to help you match up SD-WAN with your business objectives.
Table of Contents
Manufacturing Sector Challenges
The manufacturing sector often faces many unique challenges and the impact of these challenges can be a strain on business activity.
Unique Networking Challenges in Manufacturing
Businesses within the manufacturing sector often require their network to meet many demands. These can include high reliability and uptime, integration with legacy systems and equipment, support for diverse and geographically dispersed workforces and ensuring security across the entire network to protect against threats from competitors and nation-sate actors, aiming to access proprietary processes or trade secrets.
Impact of Downtime and Connectivity Issues
The impact of network downtime or connectivity issues can be severely damaging to manufacturing businesses. It is estimated that these issues can cause financial losses of up to $50,000 per minute due to production halts, supply chain disruptions and reduced operational efficiency. Interruptions to operations can also affect safety measures, which are required for manufacturers to maintain compliance with the Health and Safety at Work Act (HWSA), which mandates uninterrupted safety measures.
Role of SD-WAN in Addressing Manufacturing Challenges
These issues can, however, be mitigated by leveraging SD-WAN solutions to provide and manage your business network.
Enhanced Reliability and Redundancy
Manufacturing campuses often contain multiple buildings, assembly lines and machinery rooms, all requiring real-time data transmission. SD-WAN offers enhanced reliability and redundancy through its ability to leverage multiple transport links.
To ensure performance, manufacturers typically use leased lines, however SD-WAN builds on this by enabling multiple paths to be utilised for load balancing and resiliency. Path selection provides manufacturing branch-office or remote users with the ability to automatically and seamlessly switch network path based on bandwidth, packet loss or latency. When used with network segmentation, the manufacturing business can separate and apply security based on specific requirements.
Network uptime is essential for meeting regulatory compliance such as the Control of Substances Hazardous to Health (COSHH) as this requires manufacturers to constantly monitor and control any hazardous substances. If network downtime occurs, path selection with segmentation will allow network admin staff to ensure applications associated with COSHH are capable of utilising different paths without interruption.
Optimised Network Performance
SD-WAN, through Application-Aware Routing (AAR), prioritises critical manufacturing applications, ensuring that high-bandwidth tasks like real-time video monitoring for quality inspections get the needed bandwidth. In manufacturing environments, AAR gives priority to data from IoT sensors and quality control labs, ensuring timely quality reports. For manufacturers needing detailed documentation, such as chemical use for REACH compliance, SD-WAN offers better network performance than traditional WAN networks.
To further improve network communications, SD-WAN routing uses techniques such as Forward Error Correction (FEC), packet duplication and packet reordering. These increase the reliability of communications by reducing the impacts of packet loss, improving network availability and further enhancing the real-time connectivity between systems such as quality control reporting.
Simplified Network Management
SD-WAN orchestration is a tool that provides Software Defined Wide Area Networks with a centralised management. For manufacturers, this central management system provides a single interface to quickly and remotely manage all connections, such as across multiple production lines. This feature adds capabilities for automation, coordination of network functions, and policy enforcement across the entire network, simplifying management for network administrators. This means that manufacturers can issue rapid responses to any changes in regulations in order to maintain compliance.
Simplified network management also enables easy integration with existing infrastructure. This reduces workload on network administrators in order to integrate existing systems, such as Operational Technology (OT) and Industrial Control Systems (ICS), which are critical for manufacturing operations.
For manufacturers, protecting operations and intellectual property from threats is of utmost importance. In the event of a breach, the consequences can be detrimental to the business. Whilst security in traditional WAN networks can be difficult to implement, SASE and SSE are being integrated with SD-WAN to improve network security. These frameworks provide secure access and the protection of data across the network, preventing operations from being compromised.
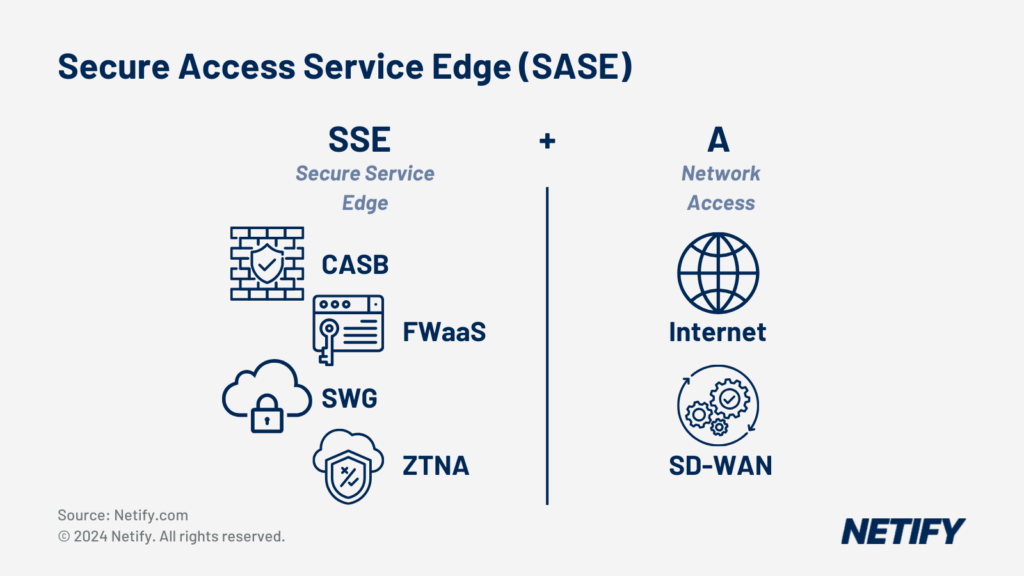
Secure Access Service Edge (SASE) is SSE + SD-WAN (Access).
Overview of SASE and SSE
Manufacturers are increasingly using the cloud for its scalability, enabling Software-as-a-Service applications such as CAD to be cloud-delivered. Unfortunately, this alone is not truly scalable, as traditional WAN networks require additional security to be added to enable such activity. Security Service Edge, on the other hand, comprises of many security features that would enable manufacturers to utilise cloud applications. These features ensure the protection of the network through consistent policies across users and devices regardless of location. Features such as Cloud Access Security Broker (CASB), Zero-Trust Network Access (ZTNA) and Firewall-as-a-Service (FWaaS) enable Zero Trust policies to be implemented and reduce the need for additional security appliances to be integrated into the network, securing the manufacturer’s intellectual property from breaches.
SASE then integrates SSE as part of its solution with SD-WAN, providing users with a holistic network management tool, leveraging a combination of security and network performance benefits. This can be helpful for manufacturers looking to attain ISO/IEC 27001, as the ability to rapidly manage the entire network security demonstrates commitment to information security, a key aspect of the regulation.
Benefits of SASE/SSE for Manufacturing
For manufacturers, there is an increasing threat from competitors and nation-state actors attempting to gain access to proprietary manufacturing processes, designs and trade secrets. These actors often use espionage tactics to infiltrate networks in order to steal intellectual property and valuable manufacturing data. Manufacturers therefore want to protect against cyber threats targeting their systems, such as industrial control systems (ICS). SD-WAN handles this through the enhanced security posture provided by the integration of ZTNA, SWG, CASB and FWaaS, which means that the network exposes less attack surface to potential threats.
Scalability
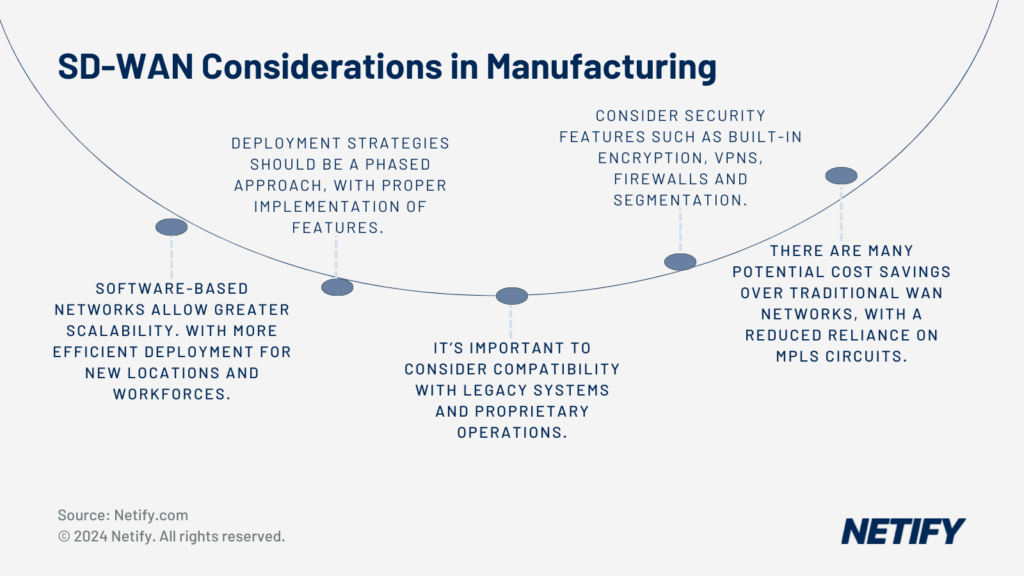
For growing and seasonal manufacturers, the ability to scale production is often essential. Networks should therefore be capable of scaling to accommodate this, however often with traditional networks, this is not the case. This means that manufacturers have operational inefficiencies either due to unneeded network systems being in place or a lack of systems, which bottleneck and delay production lines from starting whilst new systems are setup. As SD-WAN acts as a software-based network overlay with a centralised management, it allows system administrators to efficiently deploy, manage and scale networks. This enables rapid scaling and deployment of new network systems, which in turn prevents losses due to delays in starting new production lines.
Deployment Strategies
System downtime must be avoided for manufacturers, but without the correct deployment strategy, this may be an issue faced. To minimise impact on operations, IT decision makers should consider a phased approach to ensure that all features are properly implemented, giving time for potential issues and vulnerabilities to be identified and network administrators to be provided training and expertise where applicable. This prevents a system-wide outage in the event deployment is unsuccessful, which reduces the potential losses to the manufacturer from switching.
Deploying a new network architecture may also open up new system vulnerabilities, which manufacturers will want to quickly identify and rectify before their intellectual property or production line traffic is compromised. By rolling out the network in stages, each system can be checked to prevent breaches.
Compatibility with Legacy Systems
Typically, manufacturers are starting to move towards Industry 4.0. Industry 4.0 is the integration of advanced technologies like Internet of Thing (IoT), Artificial Intelligence (AI) and automation to create smart factories that enhance productivity, efficiency, and flexibility in production processes. However, manufacturers often find great difficulty when integrating an industry 4.0 approach with existing Operational Technology (OT) and Industrial Control Systems (ICS).
With SD-WAN, Industry 4.0 initiatives can be integrated whilst supporting existing operational technology and industrial control systems, enhancing manufacturing efficiency and innovation.
Security Features
To protect manufacturing data, intellectual property and underlying systems, manufacturers secure their networks to protect from threats. Unfortunately, with traditional WAN, these aren’t typically included and require additional hardware with manual integrations, which can require expertise and take man-hours to setup. SD-WAN offers built-in security measures such as encryption, VPN, firewalls and segmentation. These isolate data, ensuring that test reporting data is separated from production line data and this in turn is isolated from administrative or CAD designing traffic. This helps ensure the integrity. confidentiality and availability of all aspects of the network, which can be vital to prevent production interruptions.
With the addition of SASE and SSE, cloud-based security implementations can be integrated to enable secure local internet access to cloud applications, improving both security and network performance for services such as Software-as-a-Service (SaaS) to CAD and CAM applications.
Cost-Effectiveness
Profit margins can be key to a manufacturer’s success. With traditional WAN, manual work is required to deploy, configure, monitor and troubleshoot the network, which increases operating expenses dramatically. SD-WAN, however, features a centralised management pane and automation of network processes. These reduce operating expenses for network administration and troubleshooting due to the reduced workload and competencies required, meaning that manufacturers can utilise their budgets elsewhere.
SD-WAN Considerations in Manufacturing
For the manufacturing sector, the criteria for evaluating SD-WAN solutions are typically related to performance, reliability, scalability, security integrations, ease of deployment and costs. When comparing different solutions, it’s important for IT decision makers to evaluate the level of vendor support and the vendor offerings. Not all SD-WAN solutions are equal and some offer different features to others, so it is important to consider these prior to selecting a vendor.
To assist with this process, we would recommend our comparison of SD-WAN vendors article.
Pricing Considerations for SD-WAN in Manufacturing
Pricing is influenced by factors like bandwidth, number of sites, security features, deployment model (DIY vs managed) and additional services. Depending on the level of support, performance or scale you require, some SD-WAN solutions may not be as applicable as others.
Case Studies of SD-WAN in Manufacturing
New Wave Group is a European growth company that produces corporate goods, sports and leisure items and gifts and home furnishings. They needed to rapidly connect new sites across Europe while improving their cloud access and by replacing their outdated MPLS with Cisco’s SD-WAN solution, they achieved seamless integration with existing systems, enhanced security through segmentation, and improved agility to meet business demands.
Alewijnse, a manufacturer with locations across the Netherlands and Romania, faced similar challenges with their old MPLS network. The costs, complexity, and slow deployment times were a hindrance to business activity and by migrating to SD-WAN, it enabled them to connect new project sites quickly, gain centralised network visibility and control, prioritise critical applications, and simplify security. SD-WAN’s flexibility allowed them to use MPLS, broadband, and 4G/5G for optimal cost-efficiency and performance.
Regulations and frameworks are specific to where in the world your manufacturing organisation is operating, Netify can recommend where to obtain legal advice and check local regulatory requirements before making a decision on vendors and solutions. Additionally, depending on the type of product a company manufactures, your business could potentially be subject to additional regulations which mandate specific product security controls. For example, in the United States, manufacturers may be subject to regulations from North American Electric Reliability Corporation’s Critical Infrastructure Protection (NERC CIP) Standards and the U.S. Nuclear Regulatory Commission’s Regulatory Guide 5.71 when producing energy, or using manufacturing equipment subject to these regulations, or when manufacturing products subject to these regulations. Additionally, one of the most prevalent examples of regulatory requirements for specific product security controls is the Food and Drug Administration (FDA) security requirements for medical devices. Most of the content of the U.S. regulations at least partially overlap with the National Institute of Standards and Technology’s recommendations in the industry specific “NISTIR 8183 Revision 1, Cybersecurity Framework Version 1.1 Manufacturing Profile”, so there is some opportunity for compliance mapping. In the European Union, organisations have to work within the European Network and Information Security Agency’s Network and Information Security (ENISA NIS) Directives and in the United Kingdom the Centre for Protection of National Infrastructure (CPNI) offers advice and plans as well as resources to help ensure the safety of critical infrastructure. While both the NIS Directives and CPNI requirements were originally meant for critical infrastructure organisations like utility companies, they have quickly become both relevant and, at least partially required, for manufacturers as more and more are using ICS for plant automation.
After looking at the applicable regulations to an organisation, it is time to map needs to potential solutions. For local or remote access to ICS, organisations will need a strong IAM solution in place as well as PAM.
For remote access, VPN has been the go-to remote access solution for ICS. While VPNs typically provide strong encryption to prevent intercept of network traffic, they often provide authorised users with too much trust. So, as we move toward zero-trust security models, ZTNA is needed for both encryption of network traffic and provision of the minimum necessary trust for access to network resources.
While most ICS networks today are either isolated from the internet or only have limited connectivity, more and more of these solutions are embracing the benefits of cloud. So, in these cases, the components of SASE, including cloud security solutions combined with secure SD-WAN and ZTNA, can offer a comprehensive solution.
In any organisation where critical infrastructure components are used or manufactured, even if they’re not connected to the internet, an XDR (Extended Detection and Response) solution that specifically addresses IT/OT/ICS threats should be used to differentiate between benign and genuine threats, detect anomalies, and enable real-time monitoring and response.
Although IT/OT/ICS may use different technologies than other IT or IoT systems managed by an organisation, vulnerability management tools that address the specific IT/OT/ICS technologies in use should be used to ensure devices are up-to-date and provide situational awareness in case known vulnerabilities pose an imminent threat to manufacturing operations.
Then, since regulations are likely involved, auditing and compliance management is needed. There are several well-known security companies that aim to provide comprehensive (or as comprehensive as possible) IT/OT/ICS solutions including Tenable, Armis, Nozomi Networks and Claroty. While each of these have a lot of product overlap, each has their strength and weaknesses in their deployment models or areas of focus.
For instance, Tenable offers IT/OT/ICS vulnerability management solutions and they also offer industry-leading vulnerability management solutions for on-premise and cloud network infrastructure, so they stand to provide a more tightly-integrated vulnerability management solution vs competitors.
Nozomi Networks offers SaaS threat detection and response and threat intelligence which are specific to a growing list of ICS devices, and a centralised command centre application that can be deployed in-cloud or on-premise. Neither of these two vendors offer XDR solutions, though – but they both offer extensive integration capabilities.
As with all organisations in any industry operating in today’s digital landscape, the threat of data breaches and cyber attacks is increasing every year. More and more organisations are having to enhance and upgrade their security solutions, both physical and digital, as they continue to converge as technology evolves.
Some legacy technologies, like VoIP for example, can be relatively easily adapted to modern networking technologies and modern security solutions. Other technologies, like Operational Technology (OT) and Industrial Control Systems (ICS) used in critical infrastructure, energy and manufacturing, are not evolving as quickly or adapting as easily, making them difficult to protect with the same security technologies that protect most other networked systems.
There are many reasons for this ranging from architectures which aren’t easy to change to regulations that haven’t caught up with modern technology. Therefore, there are many emerging cybersecurity solutions that are aimed at meeting the unique challenges of ICS and manufacturing environments.
While traditional cybersecurity controls like PAM (Privileged Access Management), MFA (Multi-factor Authentication), monitoring and intrusion detection can be implemented for ICS, their regulatory considerations as well as unique risk factors since ICS compromise could lead to real-world risk to life of property. Thankfully, we’re beginning to see new resources, tools, and guidance for securing IT/OT and ICS in manufacturing environments. One of the most useful resources available to manufacturing organisations regarding IT/OT security is the MITRE ATT&CK Framework for ICS. The framework provides a matrix that tries to cover the entire lifecycle of an attack or breach and then map the lifecycle stages to their tactics, and in turn, their mitigations, as well as ways to test these areas in any given organisation.
In summary, while we’re beginning to see some really useful resources for organisations who need to implement or enhance ICS security, there is still a lot to consider: there are various regulations regionally, there are many national resources with recommendations or standards for ICS security and there are emerging frameworks like the MITRE ATT&CK Framework for ICS which are aimed at comprehensive security covering all areas and offering a guide to organisations looking to enhance and upgrade their ICS security.