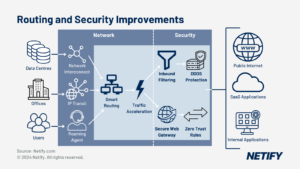
| FWaaS combines next generation firewall features with cloud scalability. |
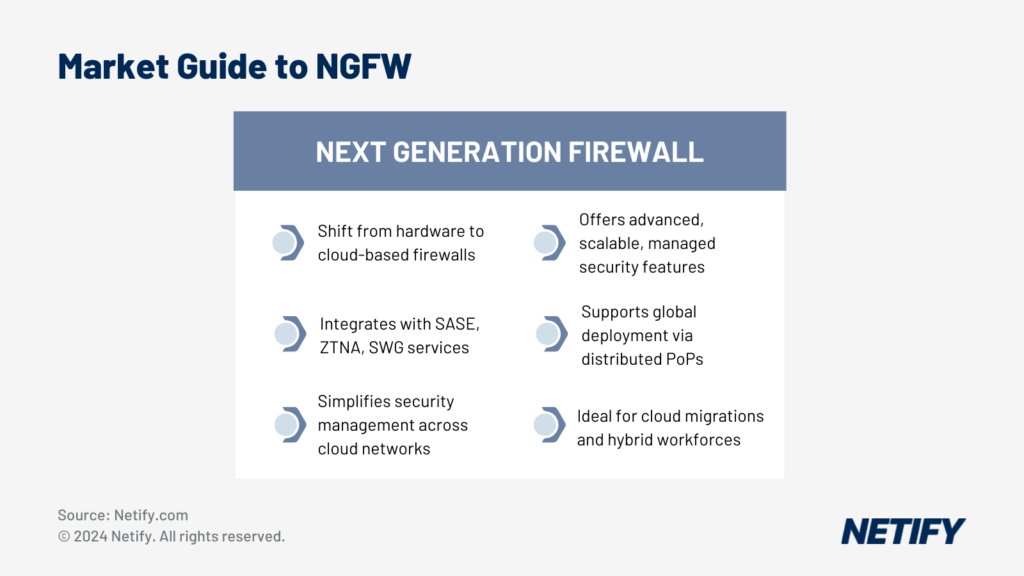
- Market Guide to NGFW
The spread of cloud services throughout the enterprise has long threatened traditional security designs based on a protected perimeter with hardware firewalls to control traffic flows. As organizations increasingly use cloud infrastructure (IaaS) to host custom applications and migrate commodified software from internal systems to SaaS products, securing clients, data, systems and applications has become impossible without replacing hardware-based controls over physical network segments with software-defined services managing virtual networks. Just as every other form of enterprise infrastructure and software has been cloud-ified, network security products have followed the cloud migration, with a thriving market in security-as-a-service offerings including:
- Next-generation firewall (NG-FWaaS)
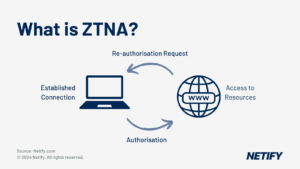
- Zero-trust network access (ZTNA)
- Secure Web Gateway (SWG)
- Cloud Access Security Broker (CASB)
- Extended Detection and Response (XDR)
Netify will profile each in the coming weeks, but start at the most fundamental layer of network security: the firewall.
Firewall-as-a-service (FWaaS) provides the features of a next-generation firewall as a managed, hosted, shared service available from both traditional firewall providers like Palo Alto Networks or a new breed of cloud-native security companies like Cato Networks or Zscaler. As such, they provide all the features of an NGFW including:
- Stateful and deep packet inspection (SPI/DPI)
- Intrusion detection and protection (IDS/IPS)
- Layer 7 application awareness to protect software delivered over HTTPS, SMTP or other protocols (for example, these are the dozens used by Apple software)
- Support for encrypted traffic (TLS, DTLS)
- Access to threat intelligence platforms that aggregate, correlate, and analyse anonymised data from thousands of networks and customers to proactively update security policies to counter new threats. According to Cisco, it takes most enterprises between 100 to 200 days to detect a threat, ample time for professional attackers to scan a network, find security gaps and infiltrate weak systems. Updating NGFWs with data from a threat intelligence service can reduce the detection time to minutes.
- Integration with identity and access management (IAM) platforms and federated identity and SSO protocols like OAuth, OpenID Connect (OIDC) and SAML to enable customised policies for users and groups.
- Network visibility and reporting of traffic statistics, events, anomalies and network performance.
- Web-based management console that consolidates policy configuration, deployment and reporting under a unified interface.
- Programmable APIs and integrations to third-party products and services that enable automating routine tasks like policy management, risk assessments, and compliance audits. These also facilitate sharing alerts and data with other security tools.
FWaaS providers typically offer other network security services like ZTNA and SWG that are delivered from a worldwide set of POPs positioned within a few milliseconds of most users. For example, Cato Networks has 60 POPs providing localised access on every continent. POPs are connected to multiple data carriers like AT&T, BT, NTT, Telia and others to onboard traffic and provide reliable, secure, high-bandwidth connectivity to the FWaaS infrastructure and other cloud providers. For example, Zscaler can sustain more than 700Gbps to many cloud providers.
FWaaS and other security service providers increasingly use AI machine learning (ML) and deep learning (DL) models to analyse network telemetry, event logs and packet flows to identify and flag anomalous behaviour. Vendors often aggregate anonymised data from all customers to better trAIn AI models and find new and unusual threats before they become widespread. Many combine AI analysis with a cloud-based application sandbox that will contain and test suspicious files or code, but not positively identified threats, for malicious behaviour in an isolated virtual environment before passing the code or packet stream onto its destination.
Aside from providing regularly updated NGFW features, running on shared cloud infrastructure allows FWaaS products to dynamically scale firewall capacity to meet changing needs. Such scalability is particularly important for companies like retailers or online entertainment and gaming providers with highly variable and seasonal traffic or anytime an organisation’s network is under DDoS attack.
FWaaS implementations are typically segmented into several logical components, namely:
- A centralised, highly available control plane for enforcing policy across all firewall instances.
- Edge nodes for onboarding and inspecting traffic and enforcing security policies via localised firewall nodes. The control plane usually uses geolocation of the client IP address to automatically direct traffic to the nearest edge node. Should users move and get redirected to another node, the control plane ensures that user- and location-specific security policies follow along.
- Logging and telemetry collection and analysis. Log servers can also stream data aggregated from an organisation’s fleet of firewalls to enterprise SIEM or data analysis systems.
- Sandbox servers to store and analyse suspicious files or code segments.
Other than the edge access nodes, the backend components are invisible to the user with traffic and data automatically flowing within the provider’s cloud environment to the appropriate subsystem.
Benefits and use cases
Traditional firewalls, whether implemented as a hardware device or virtual appliance running on a multi-NIC server, were designed for enterprise networks using perimeter-based security with little internal network segmentation. However, the rise of cloud infrastructure (IaaS), SaaS applications and home-office employees has broken this moat-and-castle security model and left users vulnerable without cloud-based security systems. FWaaS fixes the limitations of perimeter firewalls via a cloud control plane and virtual edge architecture that can deploy firewall instances on any enterprise network segment, including cloud VPCs.
FWaaS is appropriate for any organisation migrating workloads and applications to the cloud and can be used on any network including enterprise data centres, public cloud environment, branch and home offices, distribution centres and remote manufacturing and retail locations. FWaaS typically supplements existing data centre firewalls that are still used for internal network segmentation, although smaller companies with minimal internal infrastructure might choose to go all-in with cloud security services like FWaaS.
Aside from the flexibility to be deployed at any location worldwide, FWaaS has several other benefits:
- Scalable infrastructure to handle seasonal and other workload variations.
- A distributed network topology that doesn’t require backhauling traffic to data centre chokepoints to perform firewall inspection, causing large increases in latency.
- Facilitates micro-segmented network designs that create tight controls around individual applications or systems to limit the propagation of APTs and provide additional access controls for sensitive applications and data.
- Significant reduction in the overhead of managing firewall infrastructure and software.
- Easily integrated with public cloud environments which enables applying consistent security policies and configurations across multi-cloud deployments.
- Rapid scalability to handle temporary capacity spikes and long-term growth without requiring new hardware or software licenses.
- Tight integration with a vendor’s other connectivity and security services such as SD-WAN, ZTNA, SWG and CASB.
As the last point implies, most vendors offer FWaaS as part of a broader suite of security services, however, our focus here is solely on their firewall products.
Many firewall vendors now have a FWaaS product, while others are cloud-native startups without a legacy product line. Additionally, many carriers, CDNs and ISPs offer a FWaaS based on one of the commercial NGFWs.
We don’t have space to profile all of them, but these five represent some of the best FWaaS products and technology currently available.
Who are the top FWaaS (Firewall-as-a-service) providers?
The top FWaaS (Firewall-as-a-Service) providers are Cato Networks, Open Systems, Palo Alto, Versa and Zscaler. Comparison requires understanding stateful packet inspection, intrusion detection and protection, Layer 7 app awareness, encrypted traffic, threat intelligence, identity and access management, statistics and cloud-based management.
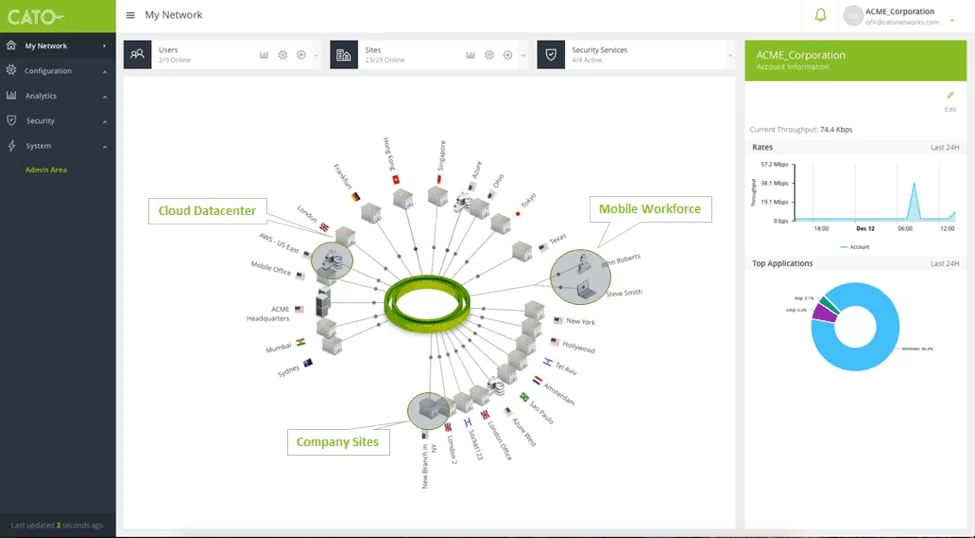
Cato Networks
Founded in 2015, Cato Networks was one of the first cloud-native network security companies that sought to solve “network security complexity, which opens up organisations to attacks as hackers can slip through the cracks of misconfigurations and software vulnerabilities by moving software-defined network and security controls to the cloud.” The intervening years have seen its technology mature into the Cato SASE cloud, which uses globally distributed POPs and private backbone to onboard traffic to Cato’s converged network and security system.
Cato’s NGFW is integrated with its SASE suite and provides a single, logical, globally distributed firewall with a unified application-aware security policy. It provides the standard features of a conventional hardware firewall, including:
- Stateful DPI and ACL filtering including rules based on network entities, time restrictions, and type of traffic. The DPI engine can classify applications or services by their headers without having to decrypt the payload.
- L7 application awareness with a complete list of signatures and parsers to identify common applications that can be extended with custom application definitions identified by port, IP address or domain.
- URL filtering
- Managed signature database updates as Cato evaluates emerging threats and develops and tests firewall rules to stop them.
- An Event Discovery feature that organises more than 100 network and security events into a single, queryable timeline.
- Event and traffic analytics
Open Systems
Open Systems firewall is available as a standalone product, but typically sold as part of its Enterprise and Enterprise+ SASE services. The firewall segments traffic into different security zones across the network to facilitate consistent policies worldwide. It also supports site-specific ACLs for more granular control of particular applications or users. In a typical implementation, IT would define global policies for each security zone — for example, remote worker WAN, data centre LAN, production cloud, public Internet, SaaS Internet — with local firewall rules and zones/network segments to accommodate particular security requirements. Open Systems’ firewall also includes typical NGFW features, including L7 packet inspection and application identification including the ability to filter SaaS applications by IP protocol, port and address.
Palo Alto
Palo Alto Prisma Access consolidates its networking and security capabilities, including FWaaS, into a single cloud-delivered SASE platform. The FWaaS includes all the features of its successful Next-Generation Firewalls (NGFWs), including:
- A single-pass inspection architecture
- L3-7 packet inspection and URL filtering with TLS support and IPS.
- User authentication and access control with a proprietary User-ID technology that uniquely identifies users across locations, regardless of their device type or OS.
- MFA (multi-factor authentication) for any application, including those built without innate MFA support, with integrations for popular IAM services such as Duo, Okta, Ping Identity and RSA.
- The Wildfire shared threat intelligence system with AI-based zero-day prevention to automatically block unknown threats and malware.
- DNS security with ML-based predictive analytics to block DNS-based attacks.
- Log aggregation data lake and reporting.
Palo Alto has more than 100 POPs in 77 countries and promises five-nines availability per month (26 seconds of down time).
Versa
Like all of the vendors in this list, Versa incorporates a FWaaS into a comprehensive SASE product that can be internally deployed in a data centre (self-managed), hosted by a service provider, delivered as a Versa-managed cloud service or as a hybrid combination of internal and managed services. Its VOS software supports multiple tenants and uses a single-pass architecture that parallelises packet processing and security components to improve performance and scalability. Versa’s NGFW has a similar feature set to the other firewalls in this article, namely:
- L3-L7 SPI with zone-based protection with standard address-port ACLs and rules based on geo-location or the time-of-day.
- Application awareness and filtering with built-in rules for more than 3000 applications and protocols.
- URL categorisation and filtering.
- IDS/IPS with default and custom signatures and profiles.
- Anti-virus scanning with automatic signature updates and support for more than 35 file types.
- DDoS protection.
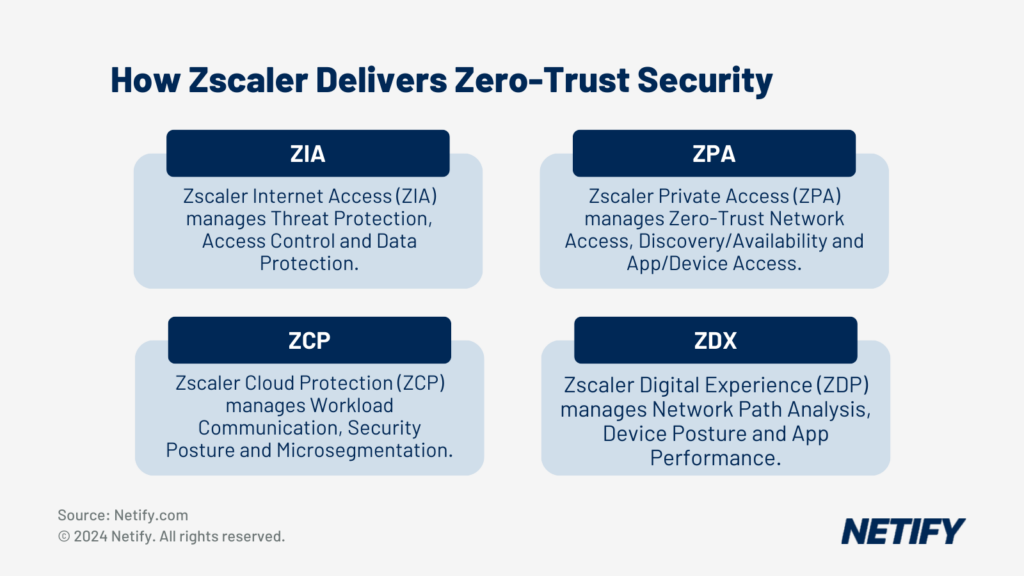
Zscaler
Zscaler’s Zero Trust Exchange is a four-pronged cloud-based approach to user, application and cloud security that uses FWaaS in several areas and allows contextual information to be shared between the firewall and other security services. Zscaler runs on 150 data centres around the world that process more than 160 billion transactions per day. Like all FWaaS products, Zscaler uses a unified, distributed control plane that provides policy consistency across all firewall instances. The Zscaler Cloud Firewall feature set is consistent with its competitors in this article and includes:
- Standard IP, port and domain name policies (aka ACLs).
- DPI with TLS support.
- Integrated IPS.
- DNS security and control that can block malicious domains, detect and prevent DNS tunnelling, and enable policies based on user, app, and geo-location.
- Log aggregation of data from all firewall instances with analytics to predict trends, expose anomalous behaviour and facilitate troubleshooting.
- Managed threat database that identifies new exploits from the billions of pooled requests in the Zscaler cloud and automatically updates blocking policies for all customers.
Trends and recommendations
The FWaaS market is dynamic and thriving with estimated revenue growth of 25 percent annually. While many organisations paused infrastructure upgrades last year due to more pressing needs handling an entirely remote workforce, the market should resume robust growth as IT teams are forced to upgrade aging hardware and weigh the benefits of a managed service against the costs of traditional hardware and virtual appliances. FWaaS is particularly advantageous to help make the following strategic changes:
- Aggressively adopting cloud services by migrating legacy applications to IaaS, developing cloud-native applications using container-based PaaS and replacing installed software with SaaS.
- Permanently adopting a hybrid workforce in which some employees return to traditional offices, some are entirely WFH (Working from Home) and some are a mix of both on-site and remote.
- Organisations with a high percentage of end-of-life security hardware requiring immediate replacement and facing significant CapEx for new systems. Also, the Enterprise needing to increase the capacity and throughput of existing security systems due to growth and new application architectures.
- Business adopting zero-trust access security to address the added vulnerabilities of a hybrid workforce.
There is a vibrant FWaaS market comprised of both traditional network equipment vendors and a new generation of cloud-based SASE providers that provide abundant choices for organisations seeking to move their security into the cloud.