| XDR services unify threat detection, response and analytics to improve security operations, offering automated responses, simplified management and integration across varied environments. |

- What are XDR CyberSecurity Services?
Our market guide series has included a mix of mature but retooled and new product categories but paradoxically, XDR is a blend of old wines in new bottles. First labeled only a few years ago by the CTO and co-founder Nir Zuk of Palo Alto Networks, according to the company, XDR results from the evolution and confluence of many software technologies.
Zuk dubbed the combination eXtended Detection and Response (XDR) and the name stuck, however, products are still early in their development, nearing the peak of inflated expectations on Gartner’s hype cycle for endpoint security. Indeed, as recently as mid-2020, some analysts debated whether XDR was a valid product category or merely a design platform, SOAPA (Security Operations and Analytics Platform Architecture) in industry parlance.
The accepted definition of XDR includes four elements:
- Threat detection and incident response features.
- A unified and centralised management system that Integrates multiple security features, ideally from different vendors (so-called open XDR products).
- SaaS consumption model.
- Real-time ingestion and analysis of activity, incident and threat data.
Many XDR features evolved from the antivirus and endpoint protection products from which it evolved. Some products are mostly closed systems designed to replace existing SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation and Response) products. In contrast, open XDR products are designed to work with existing products, for example, by triggering an automated remediation process controlled by a SOAR system.
What are the features of XDR Cybersecurity?
- Antivirus and malware detections using Machine Learning (ML) and behaviour-based analysis to improve threat detection and prevention.
- Detection models feed programmatic response scripts that remediate many threats without manual intervention, including the ability to restore infected hosts and files automatically.
- Uses dynamically updated threat intelligence networks to identify new attack vulnerabilities and methods. Intelligence networks use a combination of anonymised data collected from Internet probes and customers and crowdsourced incident reports. Some also support third-party intelligence feeds expressed in a structured format like JSON, YAML and CSV.
- Self-optimising by using incoming data and events to improve detection rules and models.
- Supports customised rules and blocklists for particular applications and groups.
- Automated device discovery and inventory management.
- Archival of device, network, authentication and application log, event and incident data to enable long-term analysis looking for Advanced Persistent Threats (APTs) designed to evade conventional threat detection software.
- Simplified alerts with customised criteria that summarise multi-faceted attacks and include recommended remediation steps.
- Data sharing with other security systems, including network and host firewalls, IDS/IPS devices and content gateways (SWG, CASB). Also integrates with SIEM, SOAR and security validation tools to enhance and streamline existing security workflows.
- Support for multiple environments, including on-premises, remote and cloud-hosted endpoints and applications.
What is the market size for XDR?
As a new product category, sales of XDR software and services are still small, with one estimate pegging revenue at about $500 million in 2020, but projected to grow about 20 percent annually through 2028. If accurate, that would put XDR sales at about $2.1 billion in 2028. Given rapid innovations in IT and changes in how enterprises use technologies like IoT, edge computing and cloud services, the final number could be wildly different.
Currently, the market consists of both installed software and services with the former accounting for 60 percent of the sales. The thesis behind our market guides is that cloud services will ultimately dominate the market for enterprise security products. Furthermore, as we have pointed out in previous market guides, product consolidation in the security industry and changing customer preferences have led most vendors to subsume product categories like XDR under comprehensive, managed, cloud-hosted services like SASE. Such category consolidation makes accurately specifying the market size of any functional category almost impossible.
What are the benefits and use cases for XDR?
There are several catalysts behind the growth of XDR that primarily stem from the increasing complexity and diversity of modern IT environments and the consequent difficulty of monitoring them for threats. According to one survey, some of the security challenges facing IT and security operation teams that XDR is expected to improve or address include:
Facilitating a security architecture that integrates multiple products (82%)
Desire to consolidate on a single security vendor (80%) or to reduce the number of security vendors in an IT environment (77%)
Simplifying threat detection and response, since for most, the process is more difficult than it was just two years ago (76%)
Another survey identified the following as the most compelling and beneficial capabilities of XDR.
- Simplified visualisation of complex attacks and their sequence of events (42%)
- Advanced analytics to detect sophisticated attacks (38%)
- Automated response features to block nascent attacks (31%)
- Reduction in the mean time to detect and respond to attacks (31%)
- Aggregation and correlation of security data from multiple sources and control points (30%)
- Consolidation of multiple security tools into a single system (26%)
- Prioritisation of security incidents and alerts based on attack severity (25%)
- Reduction in the number of security incident escalations to second- and third-tier engineers (24%)
Altogether, XDR increases the productivity of IT and security operations teams by consolidating tools under a single management console, automating many previously manual tasks and reducing alert overload which can lead front-line administrators to miss threats and anomalous behaviour. By proactively stopping threats before they afflict endpoints, XDR also reduces employee disruptions or downtime.
What are the top/best XDR vendors?
A primary premise behind our SASE market guide series is that most enterprises prefer to deliver security capabilities via managed cloud services instead of internally deployed systems. Such changes in customer demand have led most vendors of legacy network security software and appliances to join an innovative group of cloud-native security developers in offering managed security services that include XDR. Some vendors also license their software to carriers, CDNs and ISPs who offer XDR to complement their other connectivity and security products.
We don’t have space to profile all of them, but these five leading SASE vendors, whose products we have covered in our previous market guides, have some of the best technology and capabilities currently available. They also illustrate the two methods cloud security providers use to deliver XDR: via integrated XDR modules or integrations to popular third-party XDR products.
What is the Cato Networks XDR service?
As one of the pioneers of cloud security services, Cato Networks has a comprehensive SASE offering that includes XDR, which it calls Managed Detection and Response (MDR). As the name implies, Cato MDR is intended to fully offload endpoint security to Cato’s SOC and includes the following features.
- ML-enhanced threat detection using models trained from billions of network flows and events that Cato aggregates in a data warehouse. These ML models work with heuristic (rule-based) processes to detect sophisticated evasive threats.
- Threat verification by Cato researchers who review novel attacks from flagged endpoints for validity and risk severity. Such expert verification minimises false-positives.
- Automatic threat prevention and isolation by blocking domains and IPs used for command and control networks and botnets. Cato also quarantines infected systems to minimise the spread of malware inside a compromised network.
- Remediation recommendations and guidance from Cato’s SOC to speed recovery after an incident.
- Integration with Cato’s other cloud security services to enable sharing threat data between different control points and protection mechanisms.
Aside from providing real-time alerts as it discovers significant threats, Cato MDR also delivers monthly audit reports that categorise threat investigations by type, source location and date along with details on each incident.
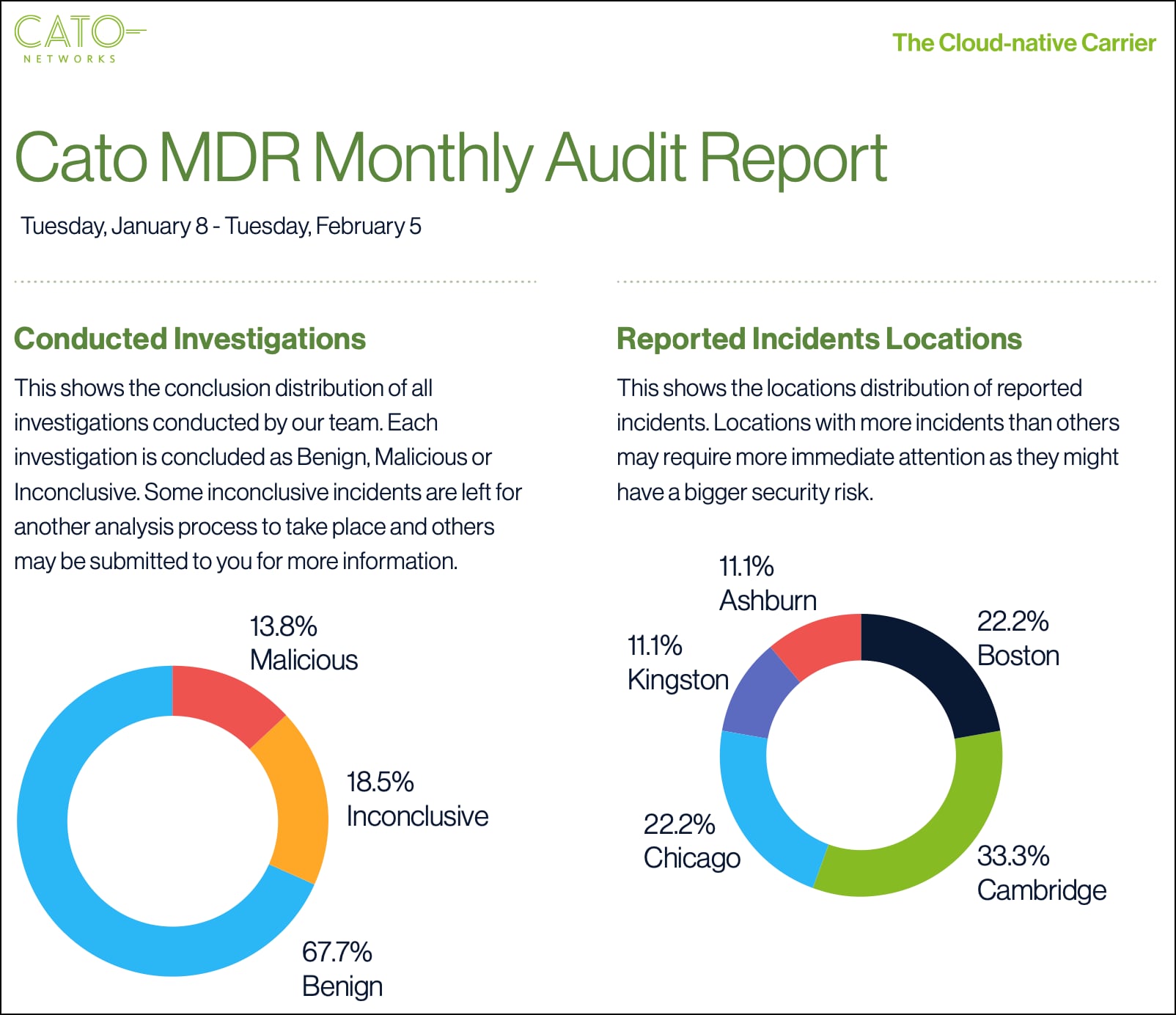
Source: Sample MDR audit report; Cato Networks
What is the Open Systems XDR service?
Open Systems XDR+ unifies three previously independent managed services:
- Network Detection and Response (NDR) to scan network traffic using Open Systems’ firewall, Secure Web Gateway (SWG) and IDS sensors to detect malicious code and suspicious activity and block the spread of malware within a private network.
- Endpoint Detection and Response (EDR) which logs activity to PCs, edge servers and other endpoints to identify breaches, malicious content and anomalous behaviour and provides immediate response by blocking intrusions, isolating infected systems and repairing any damage.
- Managed Detection and Response (MDR+) providing a managed SOC run by Microsoft’s Azure Sentinel SIEM system.
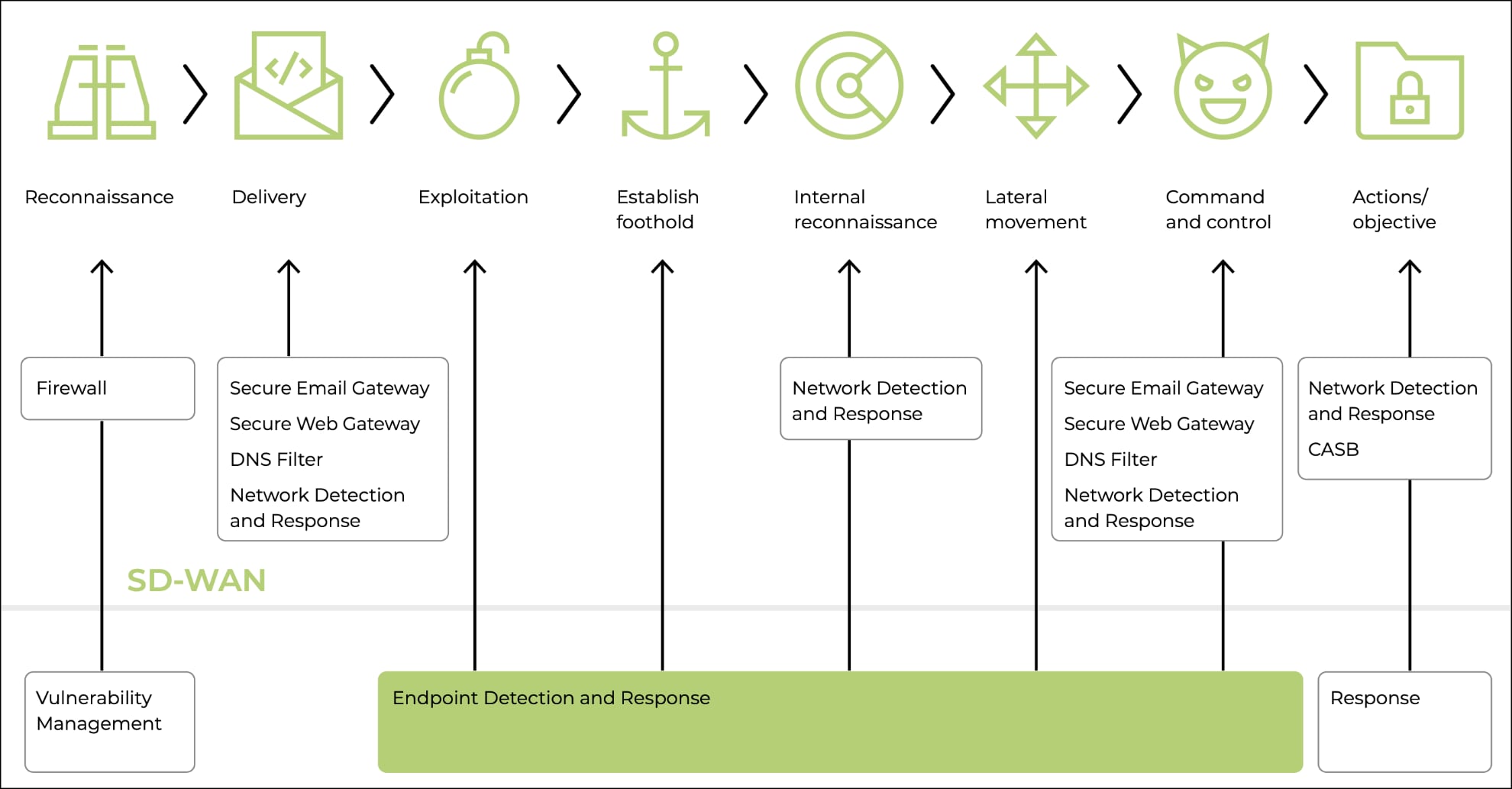
Source: Open Systems EDR data sheet.
What is the Palo Alto Networks XDR service?
More information.
Palo Alto Networks does not offer a managed XDR service, but has a highly rated product in Cortex XDR which is part of a broader suite, including Cortex XPANSE (device discovery and visibility) and Cortex SOAR (workflow and runbook automation), design for SOC teams.
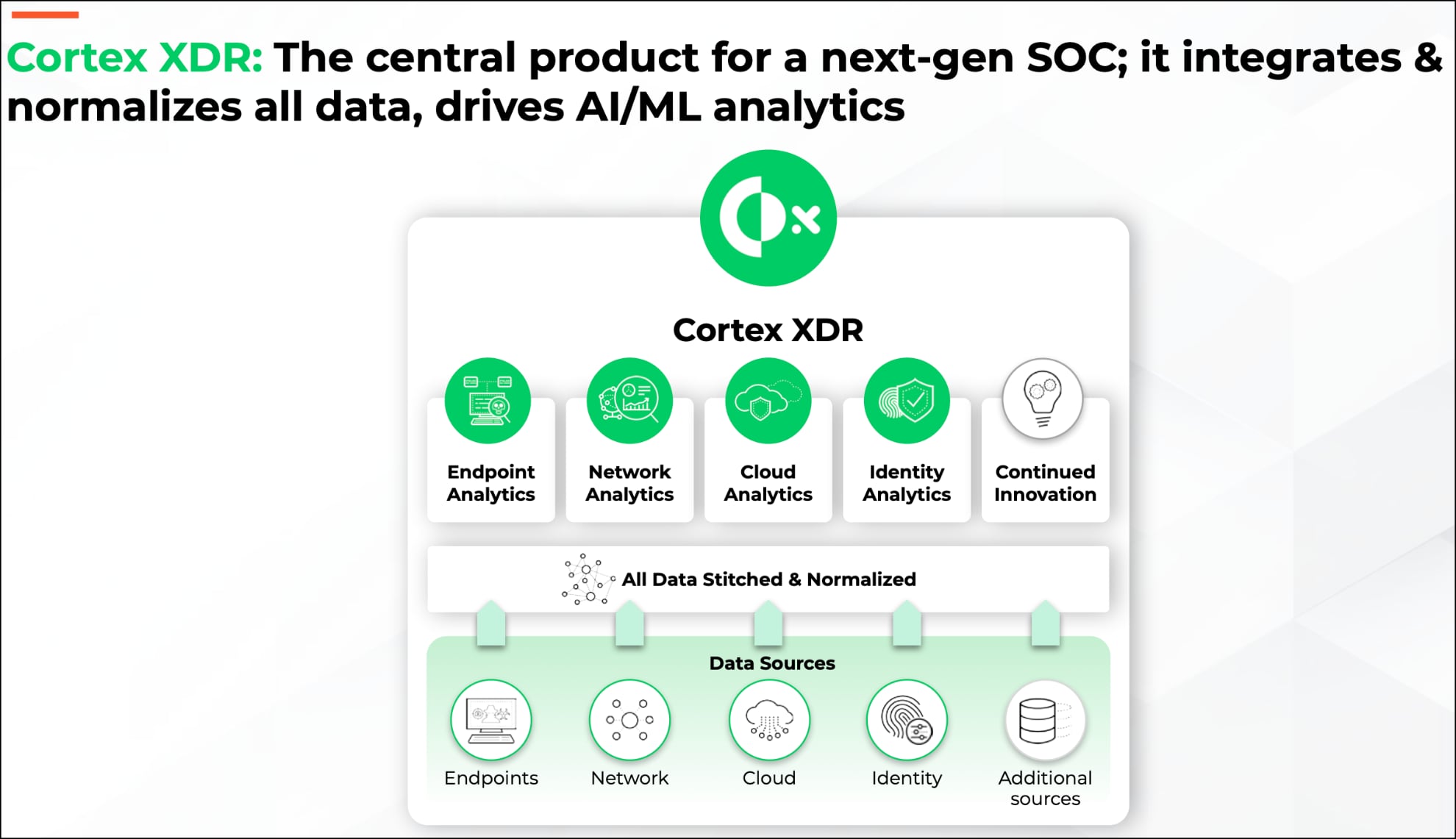
Source: Palo Alto Networks 2021 Analyst Day Master Deck.
Cortex XDR includes the following capabilities:
Endpoint protection via an agent that prevents malware, ransomware and fileless attacks using a local ML-enhanced detection engine that analyses code signatures, software behaviour and crowdsourced entries from Palo Alto’s WildFire service.
- Device control to block exploits using USB.
- Endpoint firewall and disk encryption.
- Consolidated event visibility and visualizations from all data sources.
- Search engine and query language to find and correlate APTs.
Palo Alto also offers Cortex XDR add-ons for incident forensics examination and response, host insights with a real-time dashboard showing vulnerability exposure and current patch levels across endpoints and a managed threat hunting service that continuously monitors an environment’s XDR data to proactively detect and report on advanced threats, such as state-sponsored attackers, cybercriminals, malicious insiders and malware.
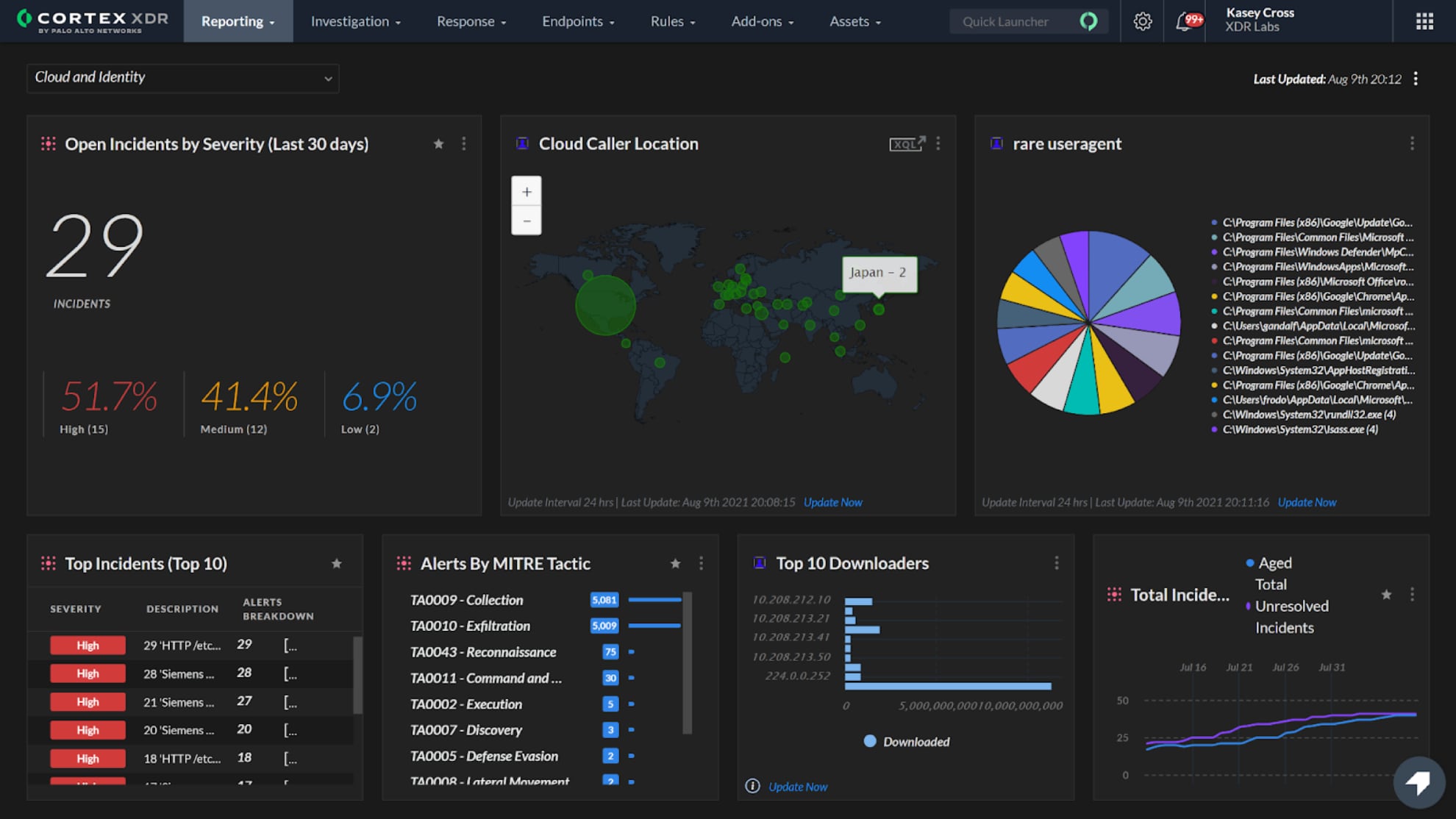
Source: Palo Alto Networks Cortex XDR data sheet; sample dashboard.
What is the Versa Networks XDR service?
Versa does not have an XDR product, but includes Versa Analytics with its SASE offering to monitor traffic, detect anomalies, summarise network usage, firewall incidents and application usage. The module also provides threat profile reports from Versa’s security controls for URL filtering, IDS/IPS, anti-virus scanning and certificate anomalies. It also can capture packets from known applications and detect vulnerabilities to facilitate forensic analysis. Sample reports include the top L7 applications by risk, traffic volume and throughput and top firewall rule violations by source, destination, domain name and geo-location.
Versa is often the choice of carriers and MSPs for their SD-WAN and SASE services and many of these also provide XDR/MDR services they integrate with Versa’s VOS software.
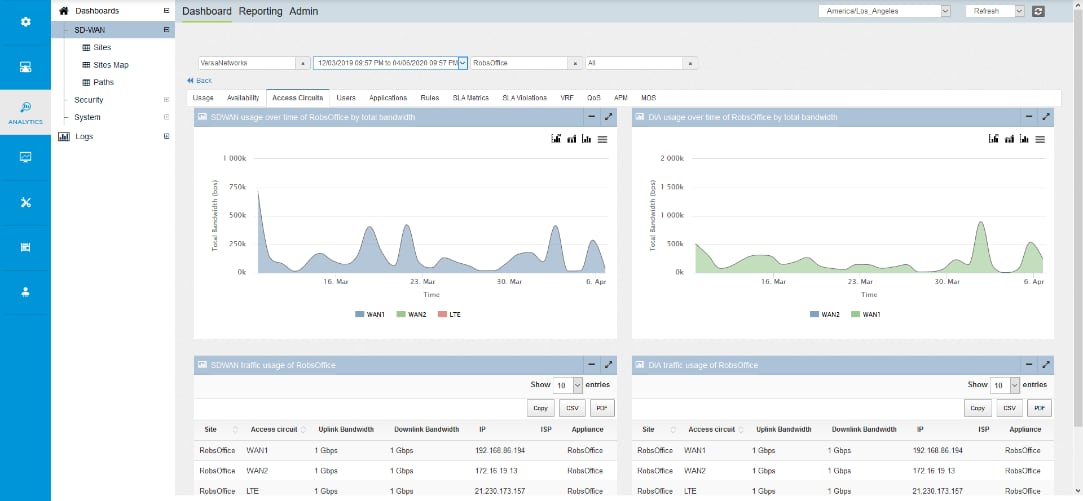
Source: Versa statistics and reporting; sample report
What is the Zscaler XDR service?
Zscaler is another cloud security company that opts to deliver XDR via partner integrations rather than a branded product. Zscaler currently works with Crowdstrike, SecBI, Secureworks and several other SOAR providers.
These solutions work by streaming logs and other data collected from Zscaler Internet Access (ZIA) and Nanolog Streaming service (NSS) to the XDR platform which analyses it using statistical, ML and other anomaly detection methods to detect suspicious activity by particular users, devices or locations. The XDR systems combine and correlate these into a set of suspicious incidents that are fed back to ZIA where changes to various security policies can be block the flagged activity.
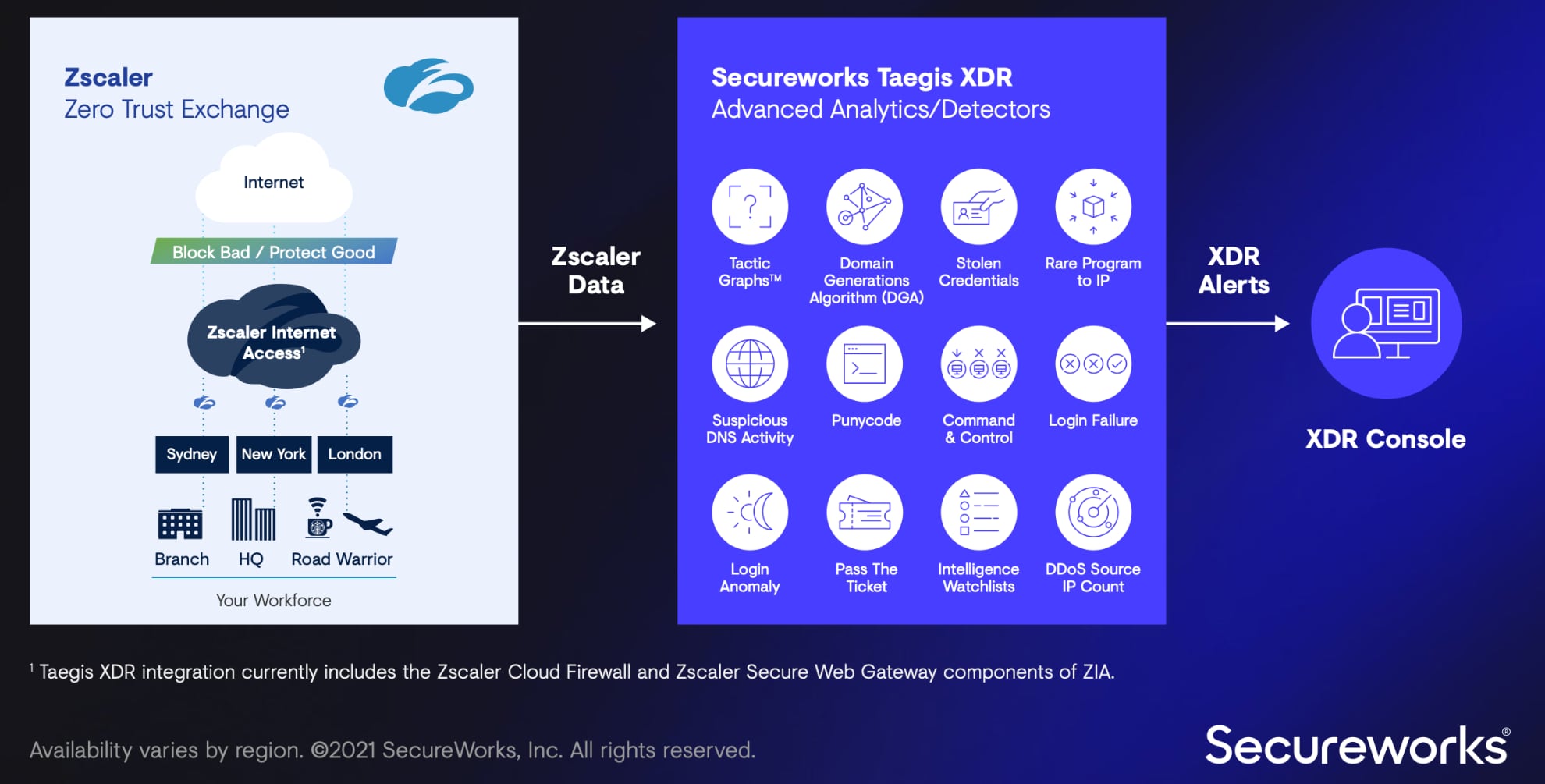
Source: Secureworks and Zscaler; Solution Brief
Netify XDR recommendations
Unlike other categories in our market guide series, XDR extends the security capabilities many organisations already have deployed via endpoint management and SOAR software.
Thus, security departments that already have (or can easily upgrade to) robust XDR functionality via products like Crowdstrike, Broadcom/Symantec, McAfee, Secureworks or SentinelOne will prefer a SASE product like Palo Alto Cortex, Versa or Zscaler that can stream telemetry to their existing system. In contrast, those looking for an all-in-one solution will prefer cloud-native products like Cato and OpenSystems.