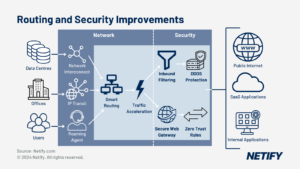
| ZTNA is a security feature that replaces implicit trust and requires continuous verification in order to gain access to networked systems. |
For the second in our Netify series of security service market guides, we focus on zero-trust network access (ZTNA), which strengthens user and device authentication and authorisation by replacing static passwords with a cryptographically strong session – or transaction-based model. ZTNA rests on a strong foundation of network – and packet-based security where firewalls — whether physical or virtual is an implementation choice — are the first line of defence.
As we discussed in our earlier market guide on next-generation firewall-as-a-service (FWaaS), the proliferation of cloud services within both large enterprises and SMBs have fractured traditional perimeter-based traffic controls by moving workloads and applications outside the confines of private data centres and company offices.
Perimeter networks were further permeated by pandemic lockdowns and the resulting mass migration to a remote workforce using consumer broadband and wireless services to access internal systems, cloud infrastructure and SaaS applications. Protecting enterprise employees, applications and data in such a distributed, diverse and disorderly environment is impossible without shifting to a software-defined security infrastructure. Just as every other form of enterprise infrastructure and software has been cloud-ified, network security products have followed the cloud migration, with a thriving market in security-as-a-service offerings including:
- Next-generation firewall (NG-FWaaS)
- Zero-trust network access (ZTNA)
- Secure Web Gateway (SWG)
- Cloud Access Security Broker (CASB)
- Extended Detection and Response (XDR)
Netify is profiling each and after laying a foundation with firewall services, examines network authentication and access in this installment. To recap, most vendors bundle products addressing each of these security functions with SD-WAN into a SASE (Secure Access Service Edge) suite. Like most software-defined infrastructure, these use a centralised, cloud-based control plane with distributed enforcement and management nodes delivered via a worldwide set of PoPs positioned within a few milliseconds of most users. For example, Cato Networks has 60 PoPs providing localised access on every continent. PoPs are connected to multiple data carriers like AT&T, BT, NTT, Telia and others to onboard traffic and provide reliable, secure, high-bandwidth connectivity. Likewise, Equinix, which offers network security services from several vendors, including two (Palo Alto and Versa) of the five profiled here, has edge onramps in dozens of locations around the world.
Source: Network Edge–Modernize Your Network Datasheet; Equinix
ZTNA is an adaptation of the general concept of zero-trust access (ZTA) which requires users, devices and applications to explicitly verify their identity for every transaction or network session and replaces the implicit trust of traditional enterprise networks, which grant access rights to any device on a private network or user with the correct password. A conventional enterprise castle-and-moat security architecture places implicit trust in other devices on a LAN or in any individual presenting a valid username-password combination. In contrast, ZTNA is designed for today’s de-perimeterised networks and expressly distrusts all devices and users until they present cryptographically strong credentials.
“Thus, ZTA reverses the maxim of “trust, but verify” to be “never trust and repeatedly verify.”
Kurt Marko writing for Netify.
Because ZTNA uses cryptographic certificates (e.g. X.509) to establish both user and device identity and also to establish TLS encrypted tunnels between users/devices and gateways or endpoints, it can replace tunnel-based VPN schemes for remote access. Indeed, many organisations adopt ZTNA to simplify remote access networking for work-from-home (WFH) employees that are often flummoxed by VPN clients and network connectivity problems, particularly in organisations that don’t allow split tunnelling and insist on funnelling all traffic through a corporate VPN gateway.
As discussed in the vendor profiles, zero-trust implementations differ, but, conceptually they are quite similar. Since it isn’t part of a broader network security portfolio, Google’s BeyondCorp Enterprise isn’t included in our list; however because of Google’s expertise, having pioneered zero-trust technology for its internal use, BeyondCorp is an outstanding example of ZTNA principles, namely:
Security controls are enforced peer-to-peer based on a combination of an initiating device (client), the initiating user on said device and the target application or IT service (for example, a file share, mail server or database).
- Authenticity is guaranteed by PKI using:
- Crypto certificates for users, devices, servers and even applications.
- A certificate authority (CA) to vouch for the validity and authenticity of presented certificates with tools for managing, renewing and revoking certificates.
- An IAM or directory service (e.g. Active Directory, RADIUS) and device inventory database (CMDB) to tie users, devices and groups to certificates. The directory service ideally supports SSO protocols like OAuth, SAML 2, Shibboleth, and OpenID Connect.
- User identity is further verified via two-factor authentication (2FA) using a combination of hardware tokens (e.g. FIDO keys) and application-based key generation (e.g. Google Authenticator, Cisco Duo).
- A security policy database with scriptable APIs that facilitate pushing enforcement actions to various network nodes and systems. Rules enforcement often entails using a device access proxy server to broker and authenticate remote connections.
- A monitoring and incident management system (a SIEM product or similar open-source implementation like the ELK stack) to aggregate network metrics and events.
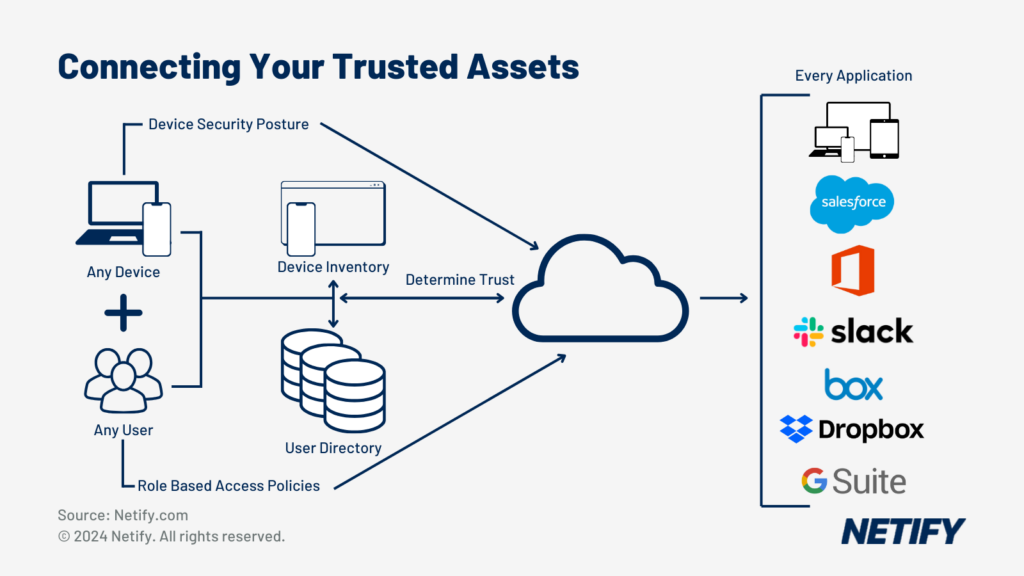
A NIST paper on Zero Trust Architecture expounds on these principles at length, including emphasizing how access to a particular resource is only granted after evaluating the requestor’s security credentials and limited to “the least privileges needed to complete the task.” The paper also notes that access requests are dynamically assessed based on a combination of factors that includes:
- The client and device identity
- Device provenance (to verify that the hardware and software haven’t been altered with malware or other malicious code)
- Real-time behavior analysis, device telemetry, geo-location, time and network state to detect anomalies or activity consistent with previously identified or ongoing threats.
As the third point implies, ZTNA implementations require continually updated data from infrastructure monitoring systems to enable tightening authentication checks in response to heightened security risks.
What are ZTNA benefits and use cases?
ZTNA significantly improves both internal (campus and data centre LAN) and external (remote access employees and contractors) security by eliminating reusable passwords, validating the provenance of connecting devices and enforcing least-privilege role-based access controls (RBAC). The combination of RBAC and session-based resource authorization also greatly limit the blast radius should a persistent threat penetrate a system and attempt to spread throughout the network. Other benefits include:
- Vendor neutrality by using standard network, application and cryptography protocols. ZTNA can also extend an existing security design as either an adjunct for particular users (e.g. remote access) or to protect new infrastructure.
- Facilitates and simplifies application micro-segmentation, particularly in cloud-native microservices implementations using containers and serverless functions.
- Supports multiple tenants for service providers
- Simplifies regulatory compliance and audits by allowing customised security policies for particular applications, data sources and users.
- As mentioned, improving the access security of remote employees and contractors is a primary reason many organisations implement ZTNA, however, other factors behind growing adoption include:
- Insuring and auditing the security of devices on or accessing the network, which is increasingly important with the proliferation of easily-hackable IoT devices.
- Enabling application-based microsegmentation.
- Protecting against supply chain threats such as the Solarwinds attack.
- Improving the security of hybrid cloud and distributed edge architectures which distribute infrastructure across many cloud environments and remote locations.
Who are the Top 5 ZTNA FWaaS providers?
Both traditional vendors of network security products and a new generation of cloud-based security services offer ZTNA products. Many also license their software to carriers, CDNs and ISPs who offer a ZTNA service to complement their other connectivity and security products. We don’t have space to profile all of them, but these five represent some of the best products and technology currently available.
What is Cato Networks ZTNA?
Founded in 2015, Cato Networks was one of the first cloud-native network security companies that sought to solve “network security complexity, which opens up organisations to attacks as hackers can slip through the cracks of misconfigurations and software vulnerabilities by moving software-defined network and security controls to the cloud.” The intervening years have seen its technology mature into the Cato SASE cloud, which uses globally distributed POPs and private backbone to onboard traffic to Cato’s converged network and security system.
Cato uses zero trust to validate and control access to its cloud services via a client-based or clientless browser-based interface that supports 2FA and SSO. Access policies can be based on a combination of user identity and application-specific controls. All Cato PoPs are connected in a full mesh using encrypted tunnels protected by symmetric 256-AES with keys rotated every hour. Clients connect via either a Cato Socket appliance using DTLS, traditional IPSec tunnels or a Cato Client application.
What is Open Systems ZTNA?
Open Systems offers ZTNA as a stand-alone product or an add-on to its Enterprise and Enterprise+ SASE services. Like other cloud security services, Open Systems intelligently routes incoming traffic through one of its PoPs to minimise that network path and latency and disaggregates the ZTNA enforcement engine from the identity management system (IAM), providing flexibility in the choice of user directory and SSO federation protocol and supports on-premises ZTNA enforcement points.
Open Systems provides both agentless browser/cloud-based and agent-based clients. Agentless implementations support HTTPS, SSH and RDP while agent-based deployments route all traffic over encrypted links to a secure Web gateway (SWG). Both clients support 2FA and security controls for enterprise and SaaS applications, individual users and groups, device signature and an XDR (extended detection and response) risk score.
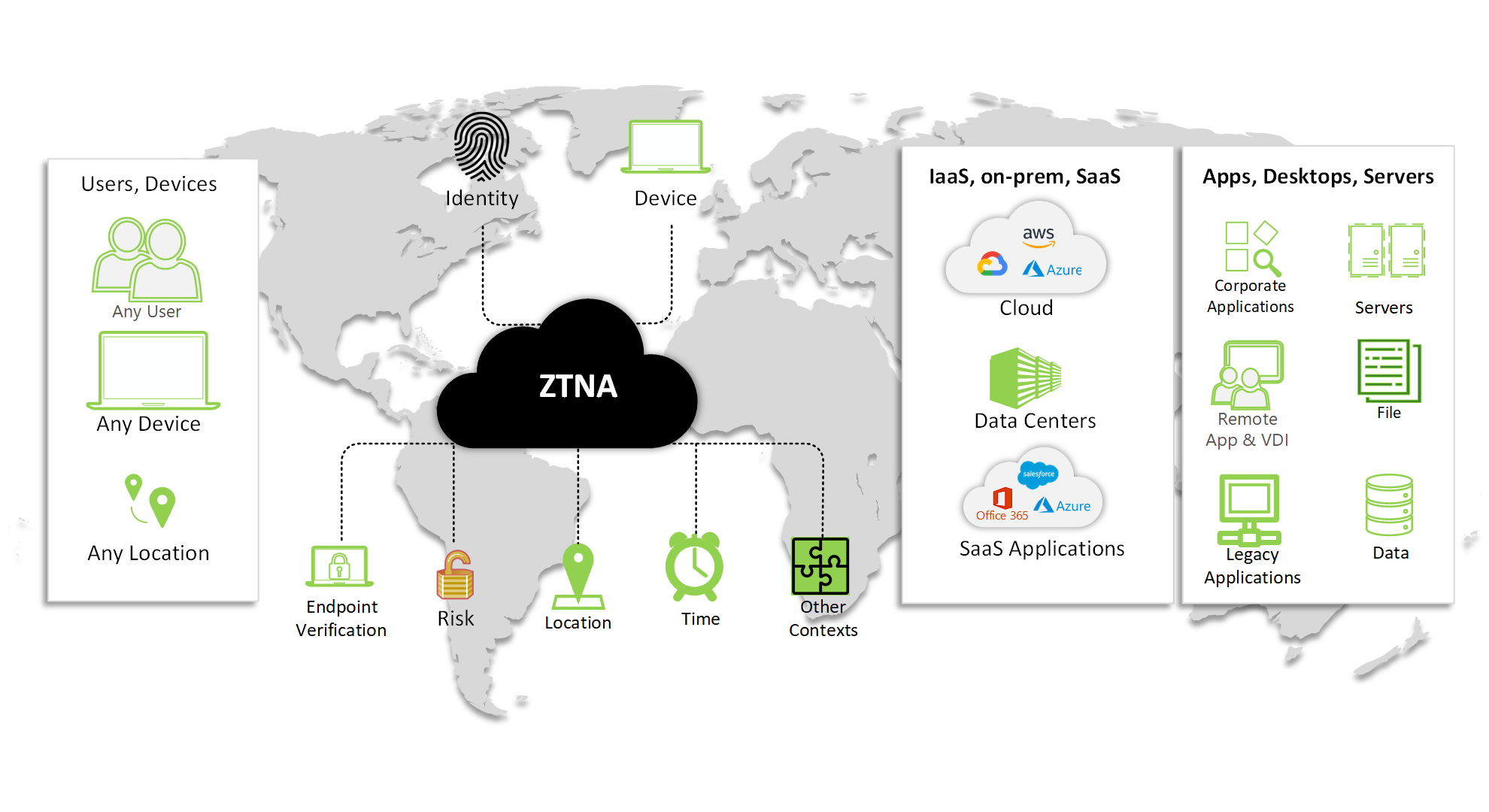
Source: Open Systems ZTNA product brief
What is Palo Alto ZTNA?
Palo Alto supports zero trust policies on its NGFW via authenticated access to network segments using Active Directory or similar IAM. It also includes ZTNA in its Prisma Cloud and Access SASE product which protects both edge networks and remote users. Prisma Cloud uses identity-based microsegmentation to control traffic and access based on user and application IDs instead of IP addresses. Prisma Cloud can automatically discover and learn application communication behaviours inside and across clouds. After applications are tied to a unique ID, Prisma Cloud automatically maps application communication behaviours inside and across clouds, which administrators can use to set restrictive policies that isolate workloads.
Prisma Access consolidates its networking and security capabilities, including FWaaS, into a single cloud-delivered SASE platform which automatically establishes an IPsec/SSL tunnel to the cloud control plane for policy enforcement, including malware detection, DLP, and malicious behaviours after connection. Policies are based on RBAC and Prisma Access supports both agentless and agent-based clients. Palo Alto uses more than 100 PoPs in 77 countries to onboard Prisma Access and Cloud traffic and promises five-nines availability per month (26 seconds of downtime).
What is Versa Networks ZTNA?
Like all of the vendors in this list, Versa incorporates ZTNA into a comprehensive SASE product that can be internally deployed in a data center (self-managed), hosted by a service provider, delivered as a Versa-managed cloud service or as a hybrid combination of internal and managed services. Its VOS software supports multiple tenants and uses a single-pass architecture that parallelizes packet processing and security components to improve performance and scalability.
- Versa Secure Access (VSA) provides a host of zero-trust capabilities including:
- Application-specific network segmentation
- User and group authentication to applications and networks.
- Integration with enterprise authentication systems (e.g. AD) with 2FA support.
Network obfuscation and topology hiding to prevent remote users from identifying an application server’s IP address and a server from seeing the user’s address, prevent users from mapping an internal network’s connections (topology), block port-scanning and limit lateral movement on a protected network.
ZTNA can be combined with other VSA services including NGFW, DDoS protection, IPS and SWG-URL filtering.
What is Zscaler ZTNA?
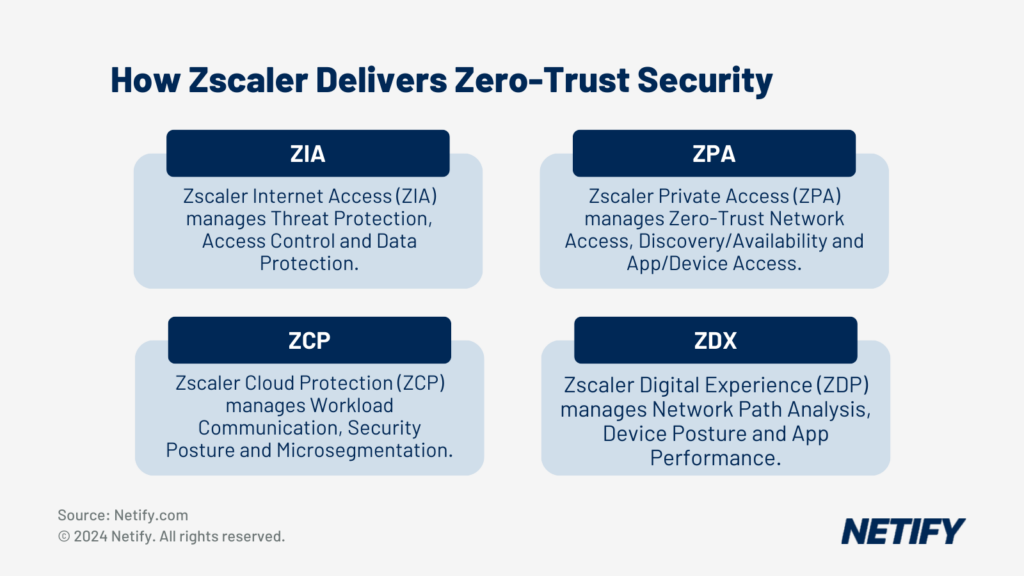
Zscaler’s Zero Trust Exchange is a cloud-based security service that supports ZTA policies for users, applications, IaaS and SaaS environments. Zero Trust Exchange can be used in place of a VPN to enforce policies for remote users and with private applications via Zscaler Private Access (ZPA), a ZTNA product for enterprise networks. ZPA has several components:
- A cloud-based engine for policy configuration and enforcement
- A client connector to verify user and device identity and configuration.
- A service edge hosted by either Zscaler or on public cloud infrastructure that checks security policy and sets up a connection to the closest application instance (for example, when using SaaS or a multi-region cloud service). Upon validating the connection, the service edge establishes a secure tunnel between the client and application.
ZPA works with popular SSO providers such as Azure AD, Okta and Ping and stream log data to most SIEM and log management applications. ZPA accounts for 27 percent of Zscaler’s new billings and 44 percent of Global 2000 companies currently use both ZPA and ZDX (digital experience monitoring).
Recommendations
In the era of hybrid workforces with many employees spending a substantial portion of their time outside company offices, ZTNA has become an essential security tool. It is particularly advantageous for organisations building distributed cloud architectures by aggressively using cloud services, migrating legacy applications to IaaS, developing cloud-native applications using container-based PaaS and replacing installed software with SaaS.