| Cloud Access Security Brokers (CASBs) enhance cloud application security with features like visibility, data protection, threat mitigation and compliance. |
Netify Market Guide to CASB Services
What is CASB?
A persistent theme in our market guide series to security services has been a significant change in enterprise plans for provisioning IT infrastructure and applications favoring cloud services over internally deployed and operated systems. The shift began as developers loved the convenience and executives appreciated the low overhead of cloud infrastructure, but accelerated during the disruptions of 2020 when most employees were forced to work remotely, which devalued the advantages of on-premises infrastructure and undermined the effectiveness of traditional approaches to IT security. The nexus of increased use of external cloud services and a remote workforce greatly exacerbated already brewing problems with traditional perimeter-based enterprise security that focused on hardening network defenses at the boundary between internal LANs and external WANs by distributing both enterprise applications and users across the Internet. Thus, the conventional ‘hard and crunchy on the outside and soft and chewy on the inside’ security design made little sense when both critical infrastructure and most employees were on the outside.
Securing modern enterprises with a hybrid workforce dependent on cloud resources requires a software-defined security strategy, which we believe is best provided by a new generation of cloud security services. As we have noted in previous market guides, network security products have followed the exodus of other enterprise applications to the cloud, creating a thriving market in security-as-a-service offerings including:
● Next-Generation Firewall (NG-FWaaS)
● Zero-Trust Network Access (ZTNA)
● Secure Web Gateway (SWG)
● Cloud Access Security Broker (CASB)
● Extended Detection and Response (XDR)
Netify is profiling each and part four of the series addresses Cloud Access Security Brokers (CASB). To recap our previous articles, most vendors bundle products addressing these security functions with SD-WAN into a SASE (Secure Access Service Edge) suite. Like most software-defined infrastructure, these use a centralised, cloud-based control plane with distributed enforcement and management nodes delivered via a worldwide set of POPs positioned within a few milliseconds of most users.
Unlike the product segments profiled in previous guides, CASB moves up the protocol stack to focus squarely on the application layer. While other security products like firewalls and web gateways have application-layer (L7) functionality, these primarily target network connections and protocols (L3-4). CASBs are largely cloud-based security services (although there are some on-premises options) that provide an umbrella of protection by mediating connections between users and cloud infrastructure and applications. Cloudflare uses the metaphor of a private security service to describe CASB this way,
“Think of a CASB as being like a physical security firm that offers a number of services (surveillance, foot patrol, identity verification, etc.) to keep a facility safe, rather than a single security guard. Similarly, CASBs offer a variety of services rather than one, simplifying the process of cloud data protection.”
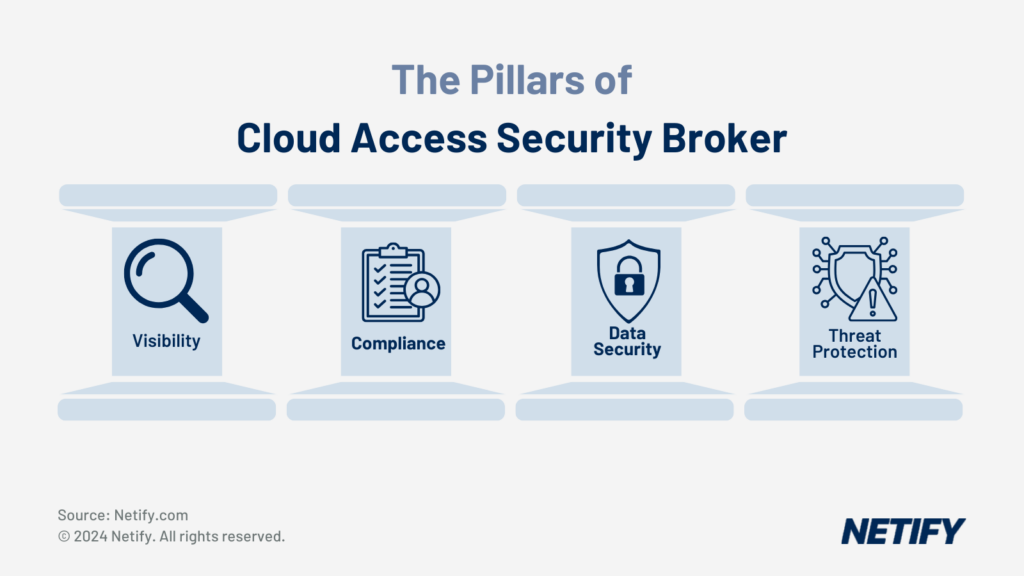
CASB is particularly useful for providing security controls to SaaS applications and file-sharing services and usage of CASB services has grown as organisations replace on-premises systems and self-managed applications with SaaS. Most CASB products conform to Gartner’s four categorical pillars.
● Visibility discovers and catalogs all cloud services used by an organisation, categorising them by a risk score. Visibility features are valuable for detecting unauthorised SaaS usage by individuals or departmental shadow IT and applying access controls to particular sites and data, including read-only, read-write and upload restrictions.
● Data security is like Data Loss Prevention (DLP) for cloud resources where CASB can identify sensitive information on cloud services and apply read and write access, sharing and encryption policies.
● Threat protection blocks external attacks and exploits such as malware or trojans via context-aware (or adaptive) access control. It also limits the threat proliferation by stopping malicious files from being uploaded to cloud storage. Many products also include application sandboxes to block zero-day exploits by running suspicious or unknown applications in isolated environments.
● Compliance allows auditing cloud applications and data repositories against regulatory or internal governance standards, summarising results in customisable reports and dashboards. CASB products maintain lists of known SaaS applications that they evaluate against a set of risk factors and can combine these risk scores with an organisation’s security policies to determine its adherence to various information security standards such as GDPR, SOC 2, PCI and HIPAA.
As our product profiles detail, most CASB products are part of a broader SASE or managed security suite allowing the CASB component to integrate and share data with other security systems, notably Secure Web Gateways (SWG) and Zero-Trust Access Controls (ZTNA). Such feature integration increases the effectiveness of CASB protections.
CASB market
Like the other products in our market guide series on cloud security, making market estimates for CASB services is challenging since most are part of broader SASE suites. Thus, it is almost impossible to ascribe revenue to individual SASE components since they are often purchased as a package. Nonetheless, some market watchers have attempted to disentangle the data or provide clues to CASB uptake.
Gartner’s annual forecast of the security and risk management market estimates that spending across all categories will grow 12.4 percent this year to $150.4 billion, up from 6.4 percent growth in 2020. Of the market segments, cloud security products are both the smallest at less than $1 billion this year, but fastest growing with spending up more than 41 percent partly due to increased interest in CASB. In summarising the results, Gartner writes,
“The smallest but fastest-growing market segment is cloud security, particularly Cloud Access Security Brokers (CASB).
“‘The pace of client inquiry indicates that CASB is a popular choice for cloud using organisations,’ said Mr. Pingree [Gartner research director]. ‘This is due to the growing popularity of using non-PC devices for interacting with core business processes, which creates security risks that can be mitigated effectively with a CASB. CASBs also enable safer interaction between SaaS applications and unmanaged devices.’”
Statista estimates overall CASB product revenue to be about $2.1 billion this year, increasing by 35 percent annually to $3.8 billion in 2023. It’s unclear why Statista’s revenue estimate is so much higher than Gartner’s number for “cloud security” products, but likely because, as Gartner explains in a CASB report, “Gartner draws a distinction between delivering security from the cloud and securing access to the cloud.” Thus, some CASB spending shows up in other Gartner categories like application, data and other security products.
Benefits and use case
CASB fills a gap in application security controls created by SaaS and cloud-hosted data whether in file shares or databases. When Forrester and Code42 surveyed U.S. “IT and security decision makers,” they found that the primary motivation for adopting CASB or cloud DLP services were to:
1. Better control user access to data (53%)
2. Improve security threat visibility and monitoring (53%)
3. Improve detection and prevention of attacks (50%)
4. Satisfy legal and compliance requirements (49%)
5. Reduce risk and compliance of insider threat requirements (48%)
6. Reduce incident mitigation time (43%)
Additional benefits include offloading system management and updating to the CASB provider, having a consolidated dashboard showing security posture for all cloud applications and data sets and the availability of APIs that can extend CASB protections to custom applications or commercial SaaS products not already integrated into the solution. The efficiencies of consolidated management and data sharing are magnified for most products, like those profiled here, that include CASB in a broader SASE or managed security portfolio.
Conversely, the Forrester survey found that the chief reasons cited for not implementing CASB are:
1. Frustration over the difficulty of configuring, maintaining and administering the products (73%)
2. Belief that they already have adequate security protections in place (57%)
3. Lack of personnel with the security expertise required to manage a CASB system (55%)
Five leading CASB providers
A growing number of enterprises prefer to deliver security capabilities via managed cloud services instead of internally deployed systems. In light of these changes in customer demand, many traditional vendors of network security products have joined an innovative group of cloud-native security developers in offering managed security services that include CASB. Some vendors also license their software to carriers, content delivery networks (CDNs) and Internet Service Providers (ISPs) who offer a CASB service to complement their other connectivity and security products. We don’t have space to profile all of them, but these five represent some of the best products and technology currently available.
Cato Networks
Cato Networks’ SASE product does not include a distinct CASB module, but has some CASB features in its firewall and threat protection systems. As we detailed in our FWaaS market guide, Cato’s CASB-like features include:
● L7 application awareness with a complete list of signatures and parsers to identify common applications that can be extended with custom application definitions identified by port, IP address or domain.
● URL filtering for web applications.
● A regularly-updated managed signature database updates as Cato evaluates emerging threats and develops and tests firewall rules to stop them including protections against malware and phishing attacks.
● Event and traffic analytics.
Open Systems
Open Systems has a comprehensive SASE product that offers CASB as an optional component to any of its service plans. Its CASB provides three primary features:
● Security audit of cloud applications to identify and inventory applications accessed by employees or others within an organisation’s network. Its monitoring system then tracks cloud service usage and creates a customised risk profile based on an organisation’s needs and risk tolerance.
● Policy enforcement of security controls over application usage, data storage and sharing and content creation on cloud applications and social media sites.
● New application assessment and blocking depending on one’s security policy, app API, file or data type or authenticated user and group identity.
Palo Alto Networks
Palo Alto Networks recently introduced a CASB module in the latest release of its Prisma Access 3.0 SASE product and its NGFW hardware. It includes the following key features:
● Integrated support for “thousands of SaaS applications” and the myriad online applications that aren’t delivered by HTTP/S and thus missed by most SaaS and Web-focused CASB and SWG products. Palo Alto claims to use Machine-Learning (ML) scanning of online properties with ML analytics to identify and automatically categorise new apps in its database.
● Real-time DLP uses Optical Character Recognition (OCR) and deep learning powered Natural Language Processing (NLP) to identify non-textual sensitive information, including Personally Identifiable Information (PII), such as a credit card or Social Security number embedded in a scanned document.
● Zero-day Threat Protection using the same malware detection, analysis and blocking technology pioneered by Palo Alto’s NGFWs and by using its “global network of 80K customers with millions of sensors across SaaS, IaaS, Endpoint, Network and world leading Unit 42 research.”
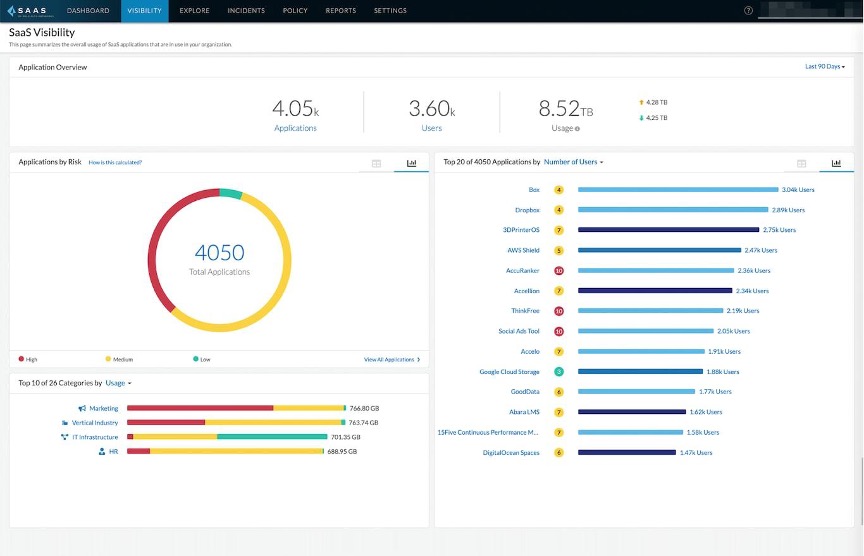
Source: Palo Alto Networks next-generation CASB product page
Versa
Versa Networks includes CASB in its SASE product, integrating the functionality into its in-line scanning engine. Versa CASB contains the following features:
● Application discovery and visibility via network scanning and firewall log ingestion. The software then provides a risk assessment and rating based on an application’s reputation and behaviour and an organisation’s security profile and policies.
● Data protection via policies to detect sensitive content, including non-textual documents using OCR and image recognition, enforce encryption and tokenisation and rules to detect misconfigurations.
● Threat protection, including malware detection and prevention, adaptive User Behavior Analytics (UBA) and strong Multi-Factor Authentication (MFA) policy enforcement.
● Regulatory compliance and auditing using pre-defined policy templates, custom reports and automatic remediation of regulatory violations via custom rules.
CASB policies can be enforced at several control points including branch or user devices, in-line proxy gateways and out-of-band using API integrations to the Versa cloud service.
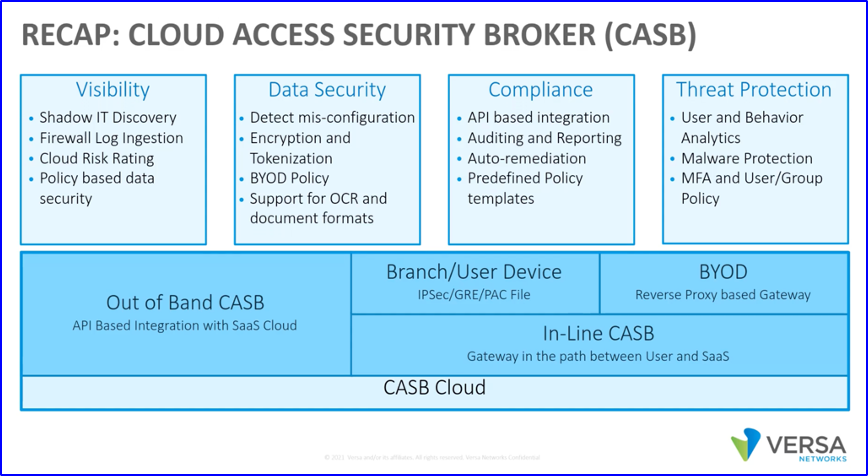
Source: Versa webinar: CASB: An Integral Part of Network Security
Zscaler
More information.
Zscaler includes CASB in its Zscaler Internet Access (ZIA) product, but most features are reserved for the premium Enterprise License Agreement (ELA) edition. These include:
● Customisable controls with real-time enforcement for thousands of cloud applications with user- and group-based limitations on usage, read/write and upload/download data access.
● Threat identification and protection by inspecting connections to cloud applications and flagging known vulnerabilities and suspicious activity. Unknown applications are shunted to a cloud-hosted sandbox for further analysis to block zero-day and ransomware attacks.
● Data classification and protection (Data Loss Prevention) examines data in transit and storage for sensitive information and data matching configured policies.
● Threat and exposure reporting cheques SaaS applications and IaaS configurations against pre-defined best practices and identifies and optionally remediates infractions. The system can also audit SaaS applications and usage for compliance with laws, regulations and security standards and automate remediation of violations.
● Application usage reporting and analysis via a logging system and dashboard that aggregates data across applications and users.
Zscaler’s CASB can share data and policies with its SWG and firewall as part of its broader SASE product.
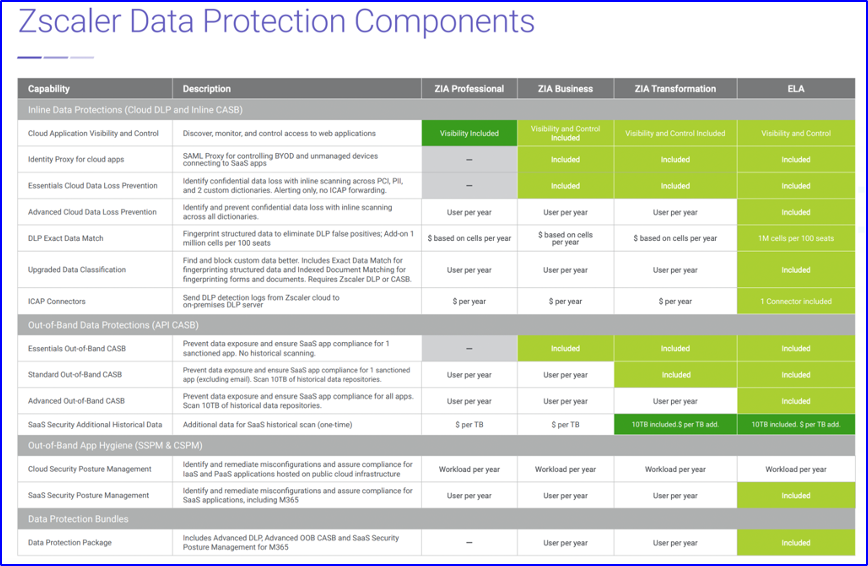
Source: Zscaler CASB Benefits at a Glance
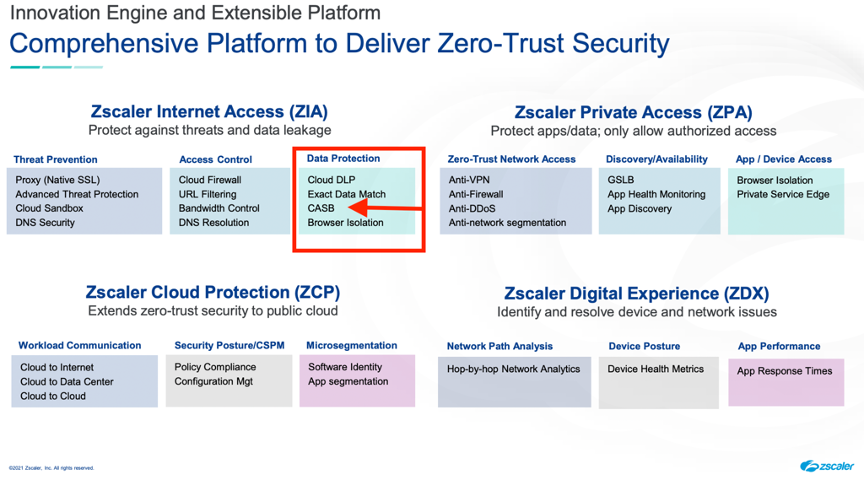
Source: Zscaler Investor presentation, 9/21; Securing your Cloud Transformation
Summary
CASB has become an essential security component now that organisations are aggressively replacing locally installed, self-managed applications with SaaS. The era of remote work and hybrid offices has highlighted the convenience and reliability of cloud services, but left holes in traditional tools and processes for application security. However, CASB is insufficient in isolation and is ideally part of a comprehensive SASE security suite like those profiled here. Thus, organisations should evaluate CASB products in the context of other solutions in a vendor’s cloud security suite and not focus on checklist items like the number of supported SaaS sites or the length of a vendor’s CASB feature list.


