| SWG enhance content filtering precision, forming a key component of SASE frameworks. |
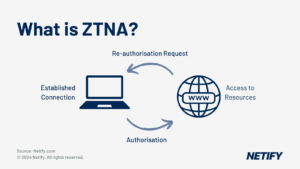
What are Secure Web Gateways?

- What is SWG?
All firewalls filter content and the most advanced, like the Next Generation (NGFW) products we reviewed in our first market guide, go beyond basic IP and port ACLs and Deep Packet Inspection (DPI) to provide some degree of application layer (L7) protection. However, even the best firewalls are blunt instruments when trying to control web applications since they are tunnelled within HTTP and HTTPS ports that must be open to allow normal browsing. Filtering web content with a firewall is akin to tuning to a particular frequency with an old crystal oscillator radio versus the precision and noise rejection of a modern digital tuner.
Further compounding the problems with using an NGFW for content filtering is the fact that almost all major websites use Transport Layer Security/Secure Sockets Layer (TLS/SSL) to improve security. While all modern firewalls can decrypt SSL traffic, it is resource intensive and significantly reduces firewall throughput. The same applies to the all in one Unified Threat Management (UTM) appliances, so popular with Server Message Blocks (SMBs) and for remote office installations and whose throughput is reduced considerably for each enabled security feature. Indeed, a 2018 study of eight NGFW products by NSS Labs found that enabling TLS/SSL decryption reduced performance by between 80 and 92 percent depending on the metric. Thus, most organisations and almost all of today’s SASE products use a Secure Web Gateway (SWG) for an added layer of protection.
Traditionally, SWGs acted as a man-in-the-middle (MITM) proxy that brokers connections between users and websites. Thus, it behaves similarly to a MITM attack, but instead of illicitly intercepting users’ passwords and sensitive information, an SWG uses its privileged path in the traffic flow to inspect traffic looking for harmful, illicit or otherwise prohibited information. Depending on the type of content, the risk severity and configured security policies, the SWG either blocks transmission, filters the questionable objects or warns the user.
As we shall see below, SWG features vary by implementation, but most vendors conform with Gartner’s definition that specifies the following features:
- URL filtering Malicious code (malware) detection and blocking.
- Specific controls for popular web applications such as messaging sites (iMessage, Facebook Messenger, WhatsApp, etc.), video conferencing services (FaceTime, Zoom, Google Meet, etc.) and SaaS business applications (Office 365, Google Workspace, Slack, etc.).
- Optional Data Loss Prevention (DLP) to block sensitive information from leaving an organisation via a web application.
- Products might also include customisable traffic filters for non web protocols like FTP, BitTorrent or other P2P file sharing applications using non-standard protocols.
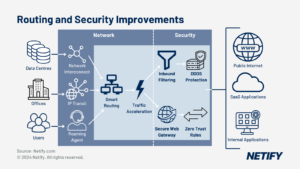
SWG – a core component of SASE
As with all security products, SWGs emerged as hardware appliances deployed in parallel to gateway routers that were configured to direct all outgoing traffic through the SWG before passing it on to the Internet. And like the other security services in our series of market guides, SWG software has migrated to the cloud as part of comprehensive SASE security suites. Indeed, an overriding theme of this series is that as organisations have adopted an array of cloud infrastructure and application services and embraced remote and hybrid work arrangements, protecting enterprise employees, applications and data in such a distributed, diverse and disorderly environment is impossible without shifting to software-defined security infrastructure.
Security vendors have adapted accordingly by developing a set of cloud security services that collectively form a SASE portfolio composed of six elements:
- An SD WAN network foundation Next-Generation Firewall (NG-FWaaS)
- Zero-Trust Network Access (ZTNA)
- Secure Web Gateway (SWG)
- Cloud Access Security Broker (CASB)
- Extended Detection and Response (XDR)
According to Gartner, revenue for SWG products amounted to $2.2 billion in 2019 with about half coming from hardware appliances and the remainder from cloud services. However, sizing the market is increasingly challenging since SWG has become intertwined with the increasingly popular SASE products. For example, Research and Markets estimates the SWG market to be more than twice as large, growing from $4.6 billion in 2019 to $10.9 billion in 2024, a 19 percent Compound Annual Growth Rate (CAGR). However, Dell’Oro, is closer to Gartner, pegging the SWG market at about $2 billion in annual revenue, with double digit growth.
Most industry analysts agree with the premise of our SASE market guide series that enterprises increasingly prefer managed security services over locally installed appliances. As Dell’Oro puts it in announcing their recent network security report, “Cloud-based SWGs have emerged as the preferred network security tool to address the shortcomings in traditional perimeter and VPN solutions and accelerate the shift to SASE and Zero-Trust.” Similarly, Gartner weighted cloud services more heavily in its last SWG magic quadrant “due to the growing customer adoption of cloud-based services.
As we wend through our market guide series on SASE components, it’s worth reminding those that might have missed the first two instalments that SASE services are grounded in software-defined infrastructure, using a centralised, cloud-based control plane with distributed enforcement and management nodes delivered via a worldwide set of Points of Presence (PoPs) positioned within a few milliseconds of most users. POPs are connected to multiple data carriers to onboard traffic and provide reliable, secure, high-bandwidth connectivity, with many POPs located in colocation centers that have carrier-neutral connectivity to major telcos and cloud service providers.
Benefits and Use Cases
As our introduction indicated, the rationale behind using an SWG instead of a firewall is to improve filtering performance, precision and coverage. In particular, the principal benefits of an SWG are:
- Higher filtering throughput and detection accuracy via an L7 proxy design. Furthermore, caching previously analysed content improves performance even more by reducing round-trips over the Internet and serving requests directly from the proxy cache.
- Better visibility and understanding of Web and SaaS applications allows SWGs to support more granular control over application and content filtering. More detail about application characteristics and behaviour also translates into better reporting and auditing of security enforcement making it easier to comply with regulatory requirements.
- Most SWG vendors collect anonymised data from customers that is aggregated and analysed in a continually updated threat intelligence database. Collecting data from thousands of sites worldwide reduces the time required to identify new threats and push out policy updates. For example, Symantec (Blue Coat) gathers threat information from 175 million users and processes 4 billion URL requests daily. This results in greater accuracy with one test showing that a popular NGFW missed 72 percent of the 200 URLs Symantec’s SWG flagged as posing a severe threat.
- More flexible URL categorisation policies, which are particularly important for social media, collaboration and other dual use sites, including LinkedIn, Twitter and YouTube that can be used for both business and leisure. Indeed, SWGs can often categorise four or five times as many web applications as the typical firewall.
- Customisable filtering and detecting policies that allow administrators to fine tune policies to minimise false-positive detections. One example would be a policy for Amazon that allows downloading Kindle and Audible books, but blocks access to other parts of the store.
- Integrates with existing Identity and Access Management (IAM), both on-premises and cloud-based and enterprise directories to tailor content filtering policies to particular users and groups.
These features make SWG a critical SASE component with 63 percent of Forrester clients listing it as either the top or second priority when deploying security services. Indeed, the content control features of SWG are so broad and fundamental that it applies to both enterprise, campus and remote locations. However, SWG is vital for WFH and hybrid office environments when used as part of a SASE implementation with SD WAN connectivity and ZTNA secure authentication.
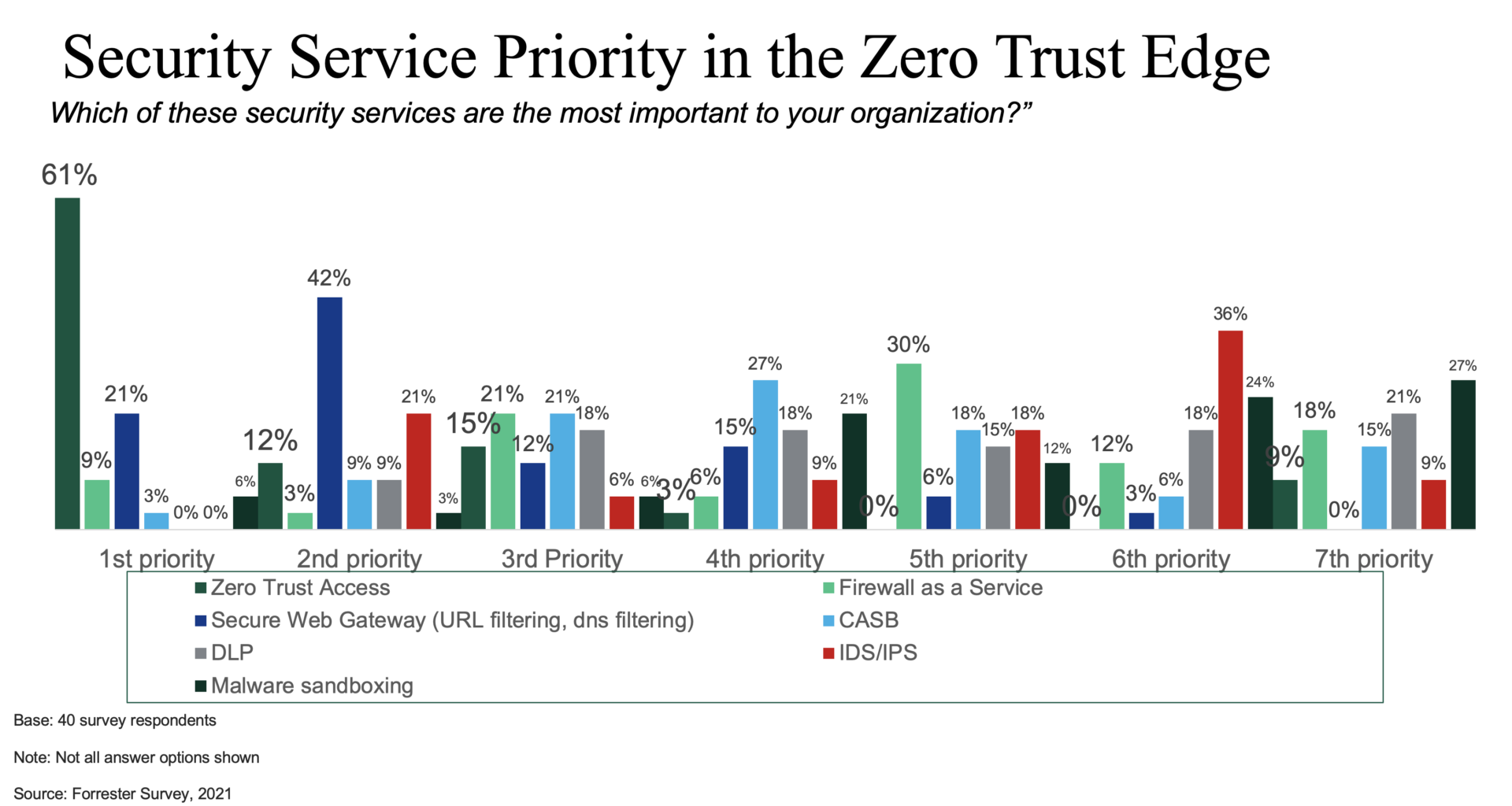
Source: Forrester blog: Take Security to the Zero Trust Edge
The top five FWaaS providers
Many security vendors have an SWG product as do most cloud security services. Some companies also license their products to carriers, Internet Service Providers and Managed Services Providers (ISPs and MSPs) who offer SWG as part of a suite of managed security services. We don’t have space to profile all of them, but these five represent some of the best SWG products and technology currently available.
Cato Networks
As we have discussed in previous market guides, Cato Networks was a pioneer in developing cloud security services and is one of the first companies to release a complete SASE suite. Like all cloud SASE products, Cato onboards traffic via more than 50 globally distributed PoPs and has a central control plane delivering consistent policies across the network. Its SWG product inspects both encrypted and unencrypted traffic and can automatically scale to handle increasing workloads. It provides granular control over URL filtering with pre-defined categories for content such as games, pornography, spam, phishing, violence and anonymizers. To aid in audit compliance, Cato’s SWG also logs all security events including the access time, filter category and device (or user if using ZTNA).
More information.
Open Systems
Open Systems‘ SWG is one element of its single-pass design for SASE services. Like other cloud services, it provides globally consistent policies and enforcement of web application and content restrictions using category based URL and DNS filtering. The company’s SWG also includes:
- User authentication enables users to tailor filter policies to particular employees, groups or departments and supports popular protocols including LDAP (Active Directory, Red Hat Directory Service) and Kerberos.
- TLS interception and certificate validation to identify encrypted threats using forged or untrustworthy credentials.
- Malware scanning for both TLS (encrypted) and unencrypted HTTP and FTP traffic and can detect previously unknown threats using heuristics.
Palo Alto Networks
Readers of our previous market guides will know that Palo Alto Networks consolidated many of its security products, including SWG, into the Prisma Access SASE platform. Like most SWG products, the Prisma component acts via a pass-through proxy that provides URL filtering, web access tracking and controls, malicious content inspection, web access controls and DLP by blocking unauthorised data transfers.
Prisma Access also uses its CloudBlades extension platform to work with Ericom Shield, a Remote Browser Isolation (RBI) product. RBI renders web content in secure execution containers to isolate users from malicious codes. RBI can also be configured to render websites in a read-only mode that blocks user input and thwarts phishing campaigns that trick employees into entering sensitive information.
Aside from its SASE product, Palo Alto also provides SWG features on its GlobalProtect VPN client for iOS and Android devices.
Versa
Versa’s SASE product is based on its VOS software that can be deployed in branch offices, large campuses, data centres and cloud environments by enterprises, carriers or managed service providers. The SWG provides customised URL filtering based on users, groups, device IDs, device types, location. It also logs web usage to identify suspicious activity and produce compliance reports for industry and government regulation. Like all cloud-based products, Versa SWG uses a centralised control plane that consistently applies policies across all locations, users and devices and allows administrators to respond to new, imminent threats. It also includes DLP filters that block unauthorised transmission of private, sensitive data.
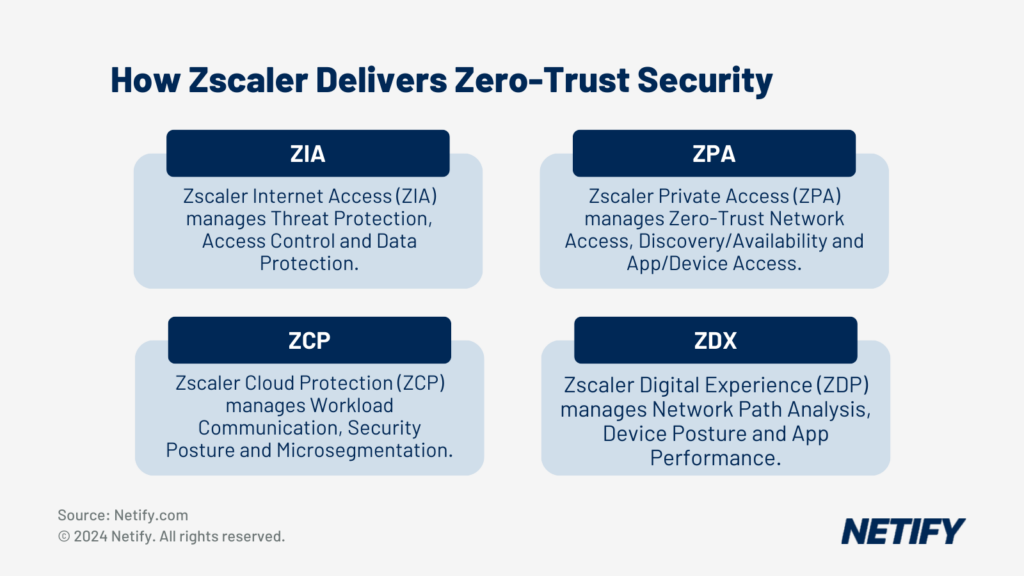
Zscaler
Zscaler has a four-pronged strategy for cloud-based security and monitoring services with SWG provided by its Zscaler Internet Access (ZIA) product. ZIA acts as a cloud-based proxy scanning all traffic (plain and encrypted) that blocks or limits website and DNS access based on user or group identity using both URL specific and categorical filtering rules. Zscaler’s PageRisk technology automatically calculates a risk score for each web page and each page element, allowing filtering rules to adjust to changing conditions dynamically. It can also enforce bandwidth policies to prioritize business traffic for critical applications over less urgent or recreational traffic. Zscaler also includes a cloud sandbox to block zero-day attacks by analysing unknown content for malicious behaviours.
Trends and recommendations
Cloud services are rapidly disrupting the market for security services by collapsing previously distinct categories into SASE suites that are centrally managed with globally distributed enforcement points. Thus, SWG products cannot be evaluated in isolation, but within the broader context of SASE features like NGFW, zero-trust access, CASB, extended incident detection and response and SD WAN. All of the products here cover the SWG basics, so one’s preference will primarily be determined by the feature integration across categories, support for alternative deployment models such as hybrid cloud, the availability of local (low latency) POPs for key company locations, pricing and the ease of other integrated security products such as RBI, log analytics and SIEM.