| SASE combines SD-WAN and cybersecurity, providing flexible, cloud-based security for decentralised networks, with a focus on Zero Trust and real-time threat detection. |
Secure Access Service Edge (SASE) brings significant change to how companies build network safety, mixing classic boundary methods with modern identity-centred structures. SASE merges cybersecurity solutions with Wide Area Network (WAN) capabilities to support the flexible yet safe needs of organisations. SASE offers comprehensive security coverage for all (users, devices, applications) irrespective of their location. By combining these functions, SASE facilitates a centralised and policy-driven approach to cybersecurity.
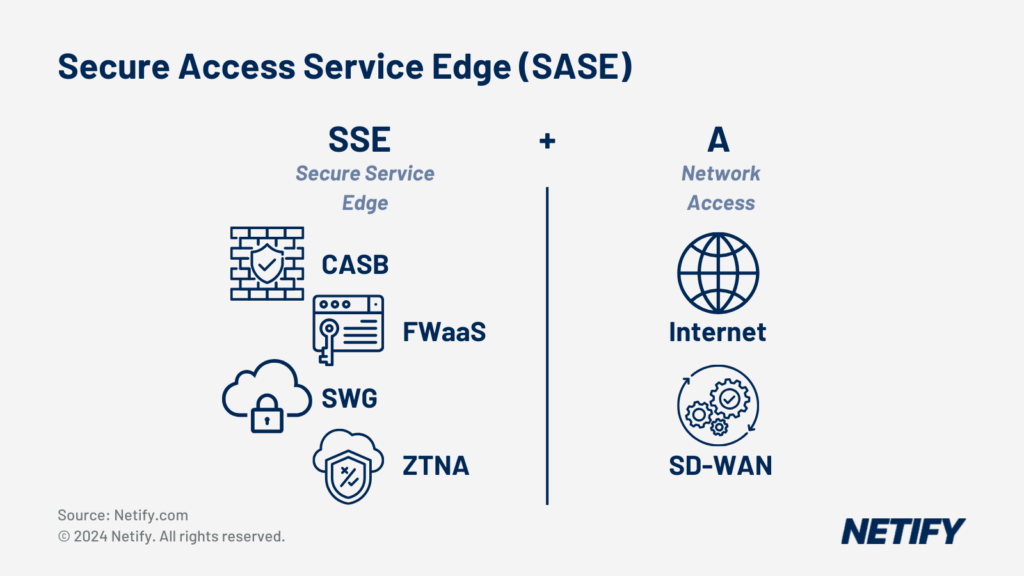
- Secure Access Service Edge (SASE) is SSE + SD-WAN (Access).
The Role of Software-Defined Networking in SASE
Software-defined Networking (SDN), specifically SD-WAN, is an integral component of SASE architecture – perhaps the biggest difference is noted here between SASE vs SSE. The integration of SASE enables the agility that is needed for a well optimised network. SDN allows engineers to manage all aspects of the network through a centralised control console. Central cloud management results in organisations having an enhanced ability to adapt to changing requirements of their network users and provide a greater experience.
Cloud Computing and SASE Integration
Cloud Computing with SASE integrations
As operations increasingly shift to the cloud, the role of SASE is critical in terms of security and availability for these platforms. SASE leverages the scalability of the cloud and allows for consistent security services to be enforced globally. Effectively implementing SASE architecture can strengthen network safety, versatility across networks and a strategic consolidation of security services to match changing cyber demands.
When initiating digital change, companies are met by various protection concerns. As an example, Chief Information Offices (CIOs) are central to the strategic implementation and adoption of the SASE model. This coherent approach integrates network connectivity and robust security functions.
The journey to utilising SASE starts by understanding that traditional/legacy security models are no longer sufficient. As organisations are increasingly reliant on cloud services, they should be aware of the need for a security framework which supports this.
It is heavily suggested that you take a strategic and phased approach when it comes to implementing SASE. Security officers must carefully evaluate their network architecture and current security policies. For this reason, there is no one-size-fits-all solution – instead the package should be tailored to specific requirements.
Security Principle:
- Zero Trust: Do not assume trust; verify all.
Operational Benefits:
- Cloud and On-Premise: Maintain operational consistency across environments.
- Endpoint Security: Ensure devices are secured regardless of location.
- Connectivity: Enhance access while ensuring security is not compromised.
Smooth execution balances enhanced security without obstructing pre-existing connectivity, organisations should select only necessary tools which won’t hinder user access or efficiency. As businesses evolve, constant monitoring of new trends should be examined to ensure the business is kept aware of the latest threats/solutions. Having a more unified, strategic and synchronised policy which aligns with the dynamic needs of a modern business is always needed.
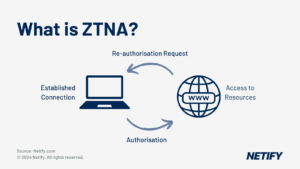
Zero Trust Network Access (ZTNA) within SASE
Cybersecurity Solutions and Vendor Landscape
The cybersecurity solutions market has witnessed significant transformation over the past 5 years. With vendors responding to organisational needs for more integrated and comprehensive approaches.
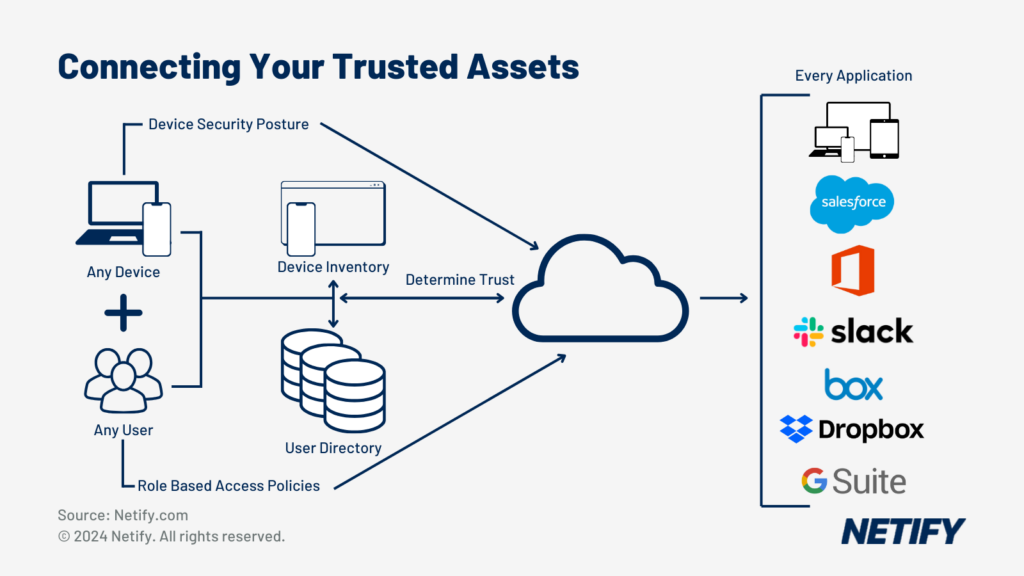
Within the past two years, the approach towards cybersecurity has shifted from basic services, such as Private Networks (VPNs) to more sophisticated frameworks which surround the Zero Trust Network Access. This change stems from the need to adjust to decentralised networks and cloud services, almost all applications are hosted within the public cloud. Zero Trust ensures strict access controls stay in place and protection isn’t broken by any user or device.
Fortinet and Netskope are prominent providers in this sector and offer Next-Generation Firewalls (NGFW) and Secure Web Gateways (SWG) that embody the Zero Trust model. Meanwhile, Cato Networks and Versa Networks have implemented SASE services directly into their networks.
Managed services have become vital for companies wanting to lighten their cybersecurity workloads. Fortinet stands out from the rest with its Security Fabric which combines various security components into a unified platform. This provides a holistic defence across each customer’s entire digital infrastructure.
The sudden introduction of Firewalls-as-a-Service (FWaaS) and Cloud Access Security Brokers (CASB) displays innovation inside solutions too. CASB acts as a policy enforcement centre, combining and interjecting enterprise security policies as the cloud-based assets are accessed.
SASE Cybersecurity Steps
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Step | Description |
|---|---|---|---|---|---|---|
| 1 | hyelland | 29/10/2024 10:15 AM | hyelland | 29/10/2024 10:15 AM | Initial Assessment | Evaluate current network and security infrastructure. Identify areas needing improvement or upgrade. |
| 2 | hyelland | 29/10/2024 10:15 AM | hyelland | 29/10/2024 10:15 AM | Strategic Planning | Define objectives for SASE implementation. Develop a phased approach for integration. |
| 3 | hyelland | 29/10/2024 10:15 AM | hyelland | 29/10/2024 10:15 AM | Selecting SASE Components | Choose appropriate SASE solutions (e.g., SD-WAN, Zero Trust Network Access). Consider vendor options and their offerings. |
| 4 | hyelland | 29/10/2024 10:15 AM | hyelland | 29/10/2024 10:15 AM | Implementation Phase | Gradually integrate SASE components into the existing network. Ensure minimal disruption to ongoing operations. |
| 5 | hyelland | 29/10/2024 10:15 AM | hyelland | 29/10/2024 10:15 AM | Training and Adaptation | Train staff on new systems and protocols. Adapt policies and procedures to align with SASE architecture. |
| 6 | hyelland | 29/10/2024 10:15 AM | hyelland | 29/10/2024 10:15 AM | Continuous Monitoring | Regularly monitor network performance and security. Adjust and optimise SASE components as needed. |
| 7 | hyelland | 29/10/2024 10:15 AM | hyelland | 29/10/2024 10:15 AM | Feedback and Improvement | Gather feedback from users and IT staff. Continuously improve and update the SASE framework. |
| Step | Description |
Market Dynamics and M&A Activity
SASE Vendor Mergers and Acquisitions
Vendors acquiring and merging into one another is something that happens quite often in the technical vendor space. For example, in November of this year Colt acquired Lumen EMEA for $1.8Billion. Consolidation is a key defining factor in today’s provider market. Research from the firm Futuriom, suggests mergers and acquisitions (M&A) stems from customers wanting integrated protection covering varied threats.
Vendors are constantly looking to expand their service portfolios or enter new markets and be presented to new potential customers. This is evident in the case of Fortinet’s strategic acquisitions, which have broadened its product offering beyond core firewalls to a more diverse set of cloud-based security solutions.
Netskope similarly flourished through strategic acquisitions, enhancing their data and threat protection offerings. Something that is vital to stay competitive in this market. This is vital as enterprises migrate to the cloud and require additional visibility and control over their data.
In the end, vendor consolidation aims to provide a more comprehensive suite of security products and services. They have realised that the customers’ requirements come first and if they can’t satisfy them, they will take their business to a competitor who can. Providers such as Fortinet, Netskope, Cato and Versa all strive to provide customers with comprehensive security solutions that meet all demands (and more).
Maximising Network Security and Operational Efficacy
In today’s market, organisations face significant challenges in keeping networks resilient and secure whilst ensuring operational efficiency. This can be a hard task to tackle. With the ever increasing rise in cloud usage, having clear control and visibility is strictly necessary.
Network Security: Fundamentally safeguarding data and users involves numerous layers of protection. Having these multiple layers of defence enables effective management of the various components. This results in a complete protection against even the most sophisticated attacks.
Challenges and Integration: One of the biggest issue for security teams is trying to make multiple independent systems work together in harmony. This leads to gaps in defence and puts the organisation at risk of an attack. Having a singular SASE solution eradicates this issue.
- Cloud Environments:
- Challenge: Gaining visibility and control within cloud infrastructures.
- Requirement: Incorporate endpoint security protection that extends to cloud-based assets.
Visibility into the IT Environment: Having a comprehensive overview of the digital infrastructure is essential if you have any hope of responding to threats. Detailed metrics empower security engineers to make informed decisions about their security posture.
Endpoint Security Protections: The most common entry point for security threats are through remote devices. For this reason, endpoint security must be stringent. Protecting these endpoints regardless of type and location is paramount. Enforced policies such as regular firmware updates and antivirus software are vital.
- Managed Services Provider (MSP):
- Role: Offer expertise and resources for managing security.
- Benefit: Partnerships with MSPs often come with service level agreements that guarantee a certain level of security and operational performance.
This approach unifies network security efforts with the goal of bolstering protections and optimising operations. Organisations that successfully integrate their security architecture can safeguard their digital assets more effectively while achieving greater operational productivity.
Emerging Trends and Future Outlook
The cybersecurity market has witnessed major alterations, primarily driven by the shift to hybrid working and the rise of cloud computing. These transformations outline SASE bases and trajectories. As systems and services become more capable, the cybersecurity vendors are constantly playing catchup to ensure their customers are protected.
A large percentage of companies who have in the past few years allowed employees to be flexible/hybrid with their work have had to quickly assess their network security. Around the same time, Zero Trust security has come into the spotlight. Long gone are the days of “trust but verify”, now it is “never trust, always verify”. Adopting a Zero Trust policy ensures that every access request, regardless of its user or origin, is thoroughly checked and verified. The lowest level of privileges are granted and users need to request anything higher.
As with every industry, the advancements in Artificial Intelligence (AI) has had a great impact on the SASE market. AI elevates SASE solutions by optimising the detection and response to threats in real-time. AI powered analytics and monitoring are capable of spotting trends and identifying potential threats before they arise. It aids the overall delivery of digital services with greater efficiency, shifting from reactive to proactive security strategies.
The Future of Network and Security Convergence
It’s looking more and more likely that in the foreseeable future, network and security will converge into a unified platform. SASE represents an intersection where networks (both private and public) meet and drive towards a singular solution. This integrated approach will simplify management and operations while vastly improving defences.