SASE combines SD-WAN with security features such as NGFW, SWG, CSAB and ZTNA. |
Introduction: SASE features and evaluation criteria
The 2020 stampede to remote work has finally reversed into a slow migration of employees back to the office. However, IT’s reaction to the sudden dispersal of colleagues across hundreds of broadband connections and insecure home wireless networks fuelled two technologies that will long outlast the pandemic. First, SD-WAN proved indispensable at delivering enterprise network performance and reliability to users on various edge connections. As we detailed in this article on WFH networking.
In 2021, SASE is the number one discussed topic when we meet to talk about vendors over Zoom.
Having established a stable network foundation for remote employees, IT organizations next focused on security, as they realized that a distributed workforce on a shared LAN in an environment full of distractions was susceptible to phishing attacks, drive-by downloads and other advanced threats that could escalate into ransomware or similar breaches that jeopardize an entire organization. The preferred solution to lax remote security is a collection of technologies known as SASE, Secure Access Secure Edge (coined by Gartner and what Forrester calls Zero Trust Edge or ZTE).
As we wrote in this article covering the basics of SASE, including the market, features and deployment models, “SASE, namely secure access service edge, is a suite of capabilities designed for remote users, offices and devices that rides atop an SD-WAN substrate.” SASE can be delivered as part of a hardware appliance, installed software (virtual appliance) or a cloud service and includes five features.
- SD-WAN connectivity via a virtual overlay to various broadband, wireless and enterprise WAN circuits.
- Next-generation firewall (NGFW) services that can be inserted anywhere in a SD-WAN fabric.
- Secure Web gateway
- Cloud access security broker (CASB) content filtering, monitoring and sandboxing services.
- Zero-trust network access (ZTNA) that supplements VPNs and application passwords with token-based access controls for individual transactions and application connections.
The individual technologies long predate any SASE implementations, but when bundled as a product or cloud service they significantly increase remote network security and auditability. As our earlier article pointed out, SASE is still new enough that it lacks established market metrics or product definitions — for example, note the differences in how Forrester and Gartner characterise the technology and product features — however, most analysts see robust market, predicting triple-digit growth over the next few years. That said, because SD-WAN is central to the other SASE features, all the products come from an established SD-WAN or network-as-a-service (NaaS) vendor. Our goal here is to review the SASE features 10 significant SD-WAN vendors have added to their product portfolio.
Vendor and product profiles
SD-WAN has become an expected part of every network company’s lineup and since there aren’t accepted public metrics for ranking SD-WAN or SASE vendors, any list will necessarily omit many fine products. However, the following 10 are popular with both large and small enterprises and make a representative sample of the state of SASE in mid-2021.
Aryaka
Aryaka was perhaps the first global NaaS vendor when it launched a SaaS-based WAN optimisation service using a private WAN with global PoPs. Over time, Aryaka has augmented traffic optimisation with many other features, including firewall capabilities that fit within the SASE definition. Aryaka’s SD-WAN components are divided across three services:
- SmartConnect and SmartOptimise. The former is a traditional remote client NaaS providing secure connections using Aryaka’s global PoP and private network, while SmartConnect adds protocol optimisation and application-specific acceleration. Together they are used to provide reliable, high-performance links for edge clients and sites to central data centres.
- SmartCloud supplements SmartOptimise with connectivity to popular IaaS and SaaS infrastructure using both Internet gateways and private interconnects like AWS Direct Connect, Microsoft ExpressRoute and Oracle FastConnect.
Aryaka’s SmartSecure service uses NFV (network function virtualisation) to add security features Aryaka’s Network Access Point (ANAP) remote security appliance including an edge (access) firewall with optional NGFW features. The firewall offers advanced features like application-based microsegmentation and works with third-party cloud-based firewalls from Check Point, Palo Alto Networks and Zscaler to extend controls to cloud infrastructure and applications. To augment its SASE features, Aryaka recently acquired Secucloud, which offers a cloud-based firewall-as-a-service, secure web gateway with advanced threat protection capabilities, although the company hasn’t indicated how it plans to incorporate Secucloud into its existing products.
Cato Networks
Cato describes itself as the world’s first cloud-native SASE platform and indeed, it has one of the most complete SASE feature sets in our round-up. Like Aryaka, Cato is a NaaS built atop a global private backbone that includes more than 60 PoPs connected by multiple enterprise-grade circuits from several data carriers. Cato’s backbone network uses end-to-end route-optimisation to improve performance and reliability between edge SD-WAN nodes. Its SD-WAN features protocol optimisation, dynamic path selection (picking the best path from multiple active links based on real-time performance measures), packet-level data deduplication and application- or user-based QoS.
Cato’s security features span the gamut of SASE capabilities including NGFW, secure Web gateway (SWG) providing URL and malware filtering, IPS and a managed threat response service that alerts Cato’s security operations centre (SOC). Although Cato doesn’t provide ZTNA, it does work with popular SSO services from Office365 and AzureAD, from which users can define role-based access controls (RBAC) and can use whatever MFA protocol supported by the authentication system.
Cisco Meraki
As we discussed in our SASE overview, Cisco has a bifurcated product line inheriting SASE features from its Meraki and Viptela acquisitions. Meraki focuses on edge networking and security with a central management plane and has a range of wired and wireless hardware products for small and medium branches, along with hardware and virtual appliances for large campuses. Meraki products include core SD-WAN features like automatic link encryption (IPsec VPN), dynamic path selection and QoS to prioritise real-time traffic like VoIP. Hardware devices also support automatic failover for high availability.
Meraki products also include a plethora of security features commonly found in UTM appliances, but which can be rebranded as SASE, including NGFW, IPS, content filtering (including support for user- or group-based policies) and malware scanning and quarantining (called ThreatGrid). Meraki supports username-password, SAML and Cisco SecureX authentication. Although it doesn’t provide ZTNA, Meraki’s auto-VPN feature, which configures IPsec between edge nodes acts as a rudimentary zero trust system by using unique security credentials on each device to establish VPN tunnels and propagate routing information automatically.
Cisco SD-WAN and Umbrella
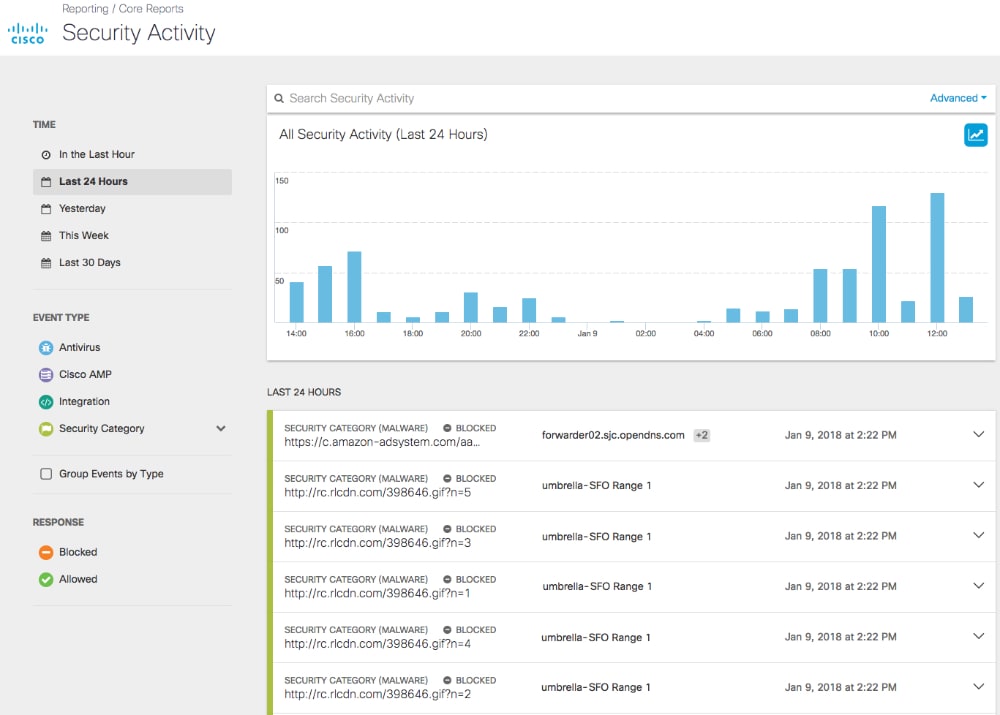
Cisco’s SD-WAN and SASE portfolio results from a mix of home-grown and acquired technologies that the company makes available as discrete SD-WAN and security products and a cloud service called Umbrella. Individual products are designed for enterprises and service providers that want to build custom SASE services. In contrast, Umbrella is a unified SASE product that Cisco will soon offer as a subscription service.
Cisco Umbrella initially targeted DNS security derived from OpenDNS, which Cisco acquired in 2015 and extended into a secure Internet gateway. Over time, Cisco added other security features to Umbrella and has recently repositioned the service as its cloud-based SASE offering. Umbrella features include DLP, SWG and remote browser isolation, cloud malware detection, L7 FWaaS, CASB including automatic app discovery and threat reporting, global threat intelligence (via the Talos acquisition), integration between Umbrella, SD-WAN and Cisco SecureX security operations console and ZTNA via Duo technology (which Cisco acquired in 2018). Cisco delivers Umbrella from one of its 30 globally distributed data centres and promises near continuous uptime.

Citrix
Like Cisco, Citrix sells a mix of cloud services and installable hardware and software for self-managed SD-WAN and SASE implementations. Its enterprise SD-WAN products, formerly known as NetScaler, come in both physical and virtual appliances and consist of SD-WAN Orchestrator or Center (central service and configuration management), WANOP (traffic and protocol optimisation) and Platform (software and hardware appliances acting as edge endpoints). Citrix’s SASE features include NGFW, SWG, CASB, malware scanning and quarantine (sandboxing), DLP, remote browser isolation and ZTNA.
Citrix Secure Internet Access (SIA) is a SaaS product that delivers its SASE features as a managed service that works with any SD-WAN and cloud direct Internet access (DIA) connections. Those using Citrix SD-WAN can manage both products from the same UI and configure secure tunnels from edge locations to SIA. SIA also works with Citrix Virtual App and Desktop environments using a Cloud Connector agent that redirects traffic to SIA.
Open Systems
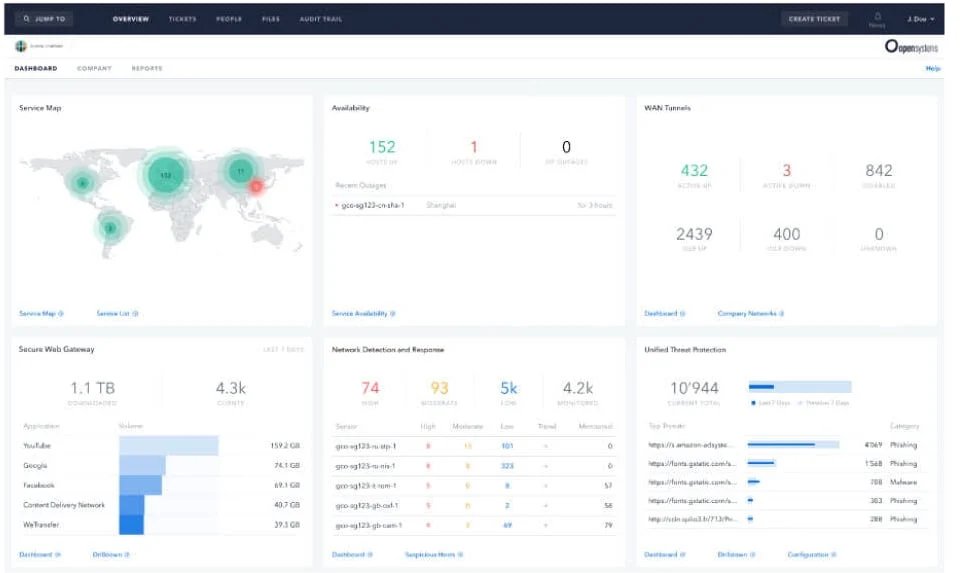
Open Systems is another NaaS provider that combines SD-WAN and security features into a SASE product. It includes core SD-WAN features like dynamic path selection, QoS bandwidth controls, packet, protocol and application optimisations and central management of configuration, encryption and security settings. Security features added in an Enterprise edition include NGFW, CASB, IDS/IPS, SWG and secure email gateway, remote (cloud) browser sandboxing and managed threat detection and response (Enterprise+ plans). Its management console provides a numerous metrics and reports and uses machine learning to provide early warning to security incidents, network bottlenecks and other potential anomalies.
Oracle
Oracle offers a range of SD-WAN products for both data centre and edge installations that include hardware appliances from its Talari acquisition, virtual appliances, on-premises management software and a cloud-based orchestrator. Both on-premises (SD-WAN Aware) and cloud (SD-WAN Orchestration Cloud) management provide central control over device, application and security policies, zero-touch provisioning, configuring and updating of edge devices and network monitoring. Edge locations can use Talari hardware or VM appliances that run on either VMware vSphere or Microsoft Hyper-V that supports the standard list of SD-WAN features.
While its SD-WAN stack provides basic firewall functionality, Oracle relies on partners including Check Point, Palo Alto Networks and Zscaler to deliver SASE features. Furthermore, for a local NGFW, the Talari E100 SD-WAN device may load the Check Point Quantum Edge Firewall and provide telemetry to Check Point’s Harmony Connect system.
Palo Alto Networks
Palo Alto Networks is another company with a bifurcated SASE implementation composed of SD-WAN services from the CloudGenix acquisition, now called Prisma SD-WAN, and its primarily home-grown Prisma Access cloud security services. Like all SD-WANs, Prisma features a central controller that manages routing policies, device configurations and VPN settings and remote devices from Palo Alto’s ION line of branch and data center appliances. Prisma SD-WAN includes a stateful L7 zone-based firewall (ZBFW) that secures the network edge and segments traffic within a branch.
Prisma Access is Palo Alto’s cloud security platform that onboards traffic from more than 100 PoPs in 76 countries. Access augments the SD-WAN’s firewall and VPN with several security features, namely:
- SWG to proxy websites and block malicious content with DNS security to stop cache poisoning and similar attacks.
- Known and zero-day threat protection using a central database and real-time data analysis and application sandboxes to quarantine potential malware.
- CASB and DLP to enforce data sharing policies and block unauthorised data movement and provide additional threat protection
- IoT device monitoring, policy enforcement and threat prevention.
- ZTNA to provide service- and application-specific access controls.
Versa Networks
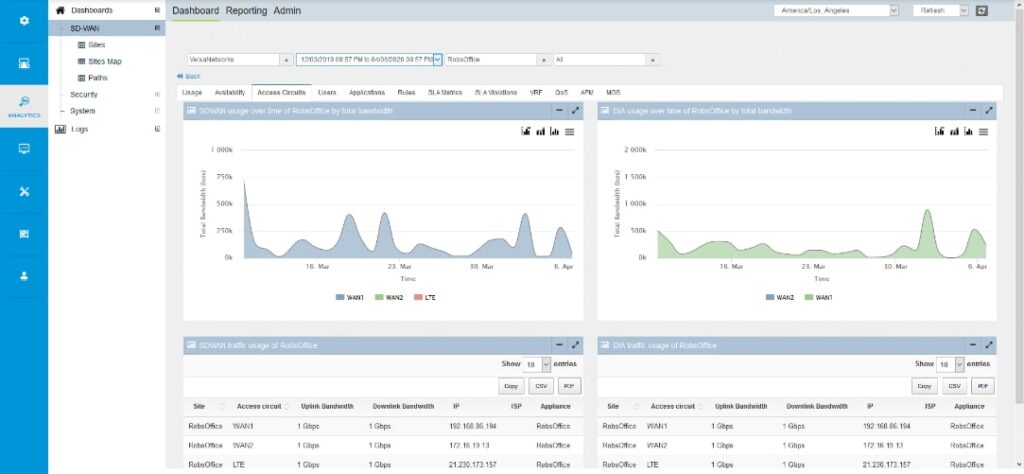
Versa SASE builds on its SD-WAN product by incorporating security features into its Versa Operating System (VOS). The company claims that its patented single-pass scanning technology is more efficient than NFV service chains that cascade connections between an SD-WAN gateway and one or more cloud services, some of which might be delivered by different providers. Versa provides the full gamut of SASE features including SD-WAN routing and packet optimisation, NGFWaaS, remote browser isolation, SWG, CASB, ZTNA and central network management and analytics.
Versa Secure Access (VSA) and Secure Private Access provide ZTNA with several distinctive features, including application-based microsegmentation, SSO using AD, LDAP, SAML and OKTA, MFA via SMS or email codes, Duo, Google or Microsoft Authenticator apps, RBAC and network obfuscation that hides server IPs from the client and client IPs from the server to prevent port scanning and lateral network movement.
VMware – VeloCloud
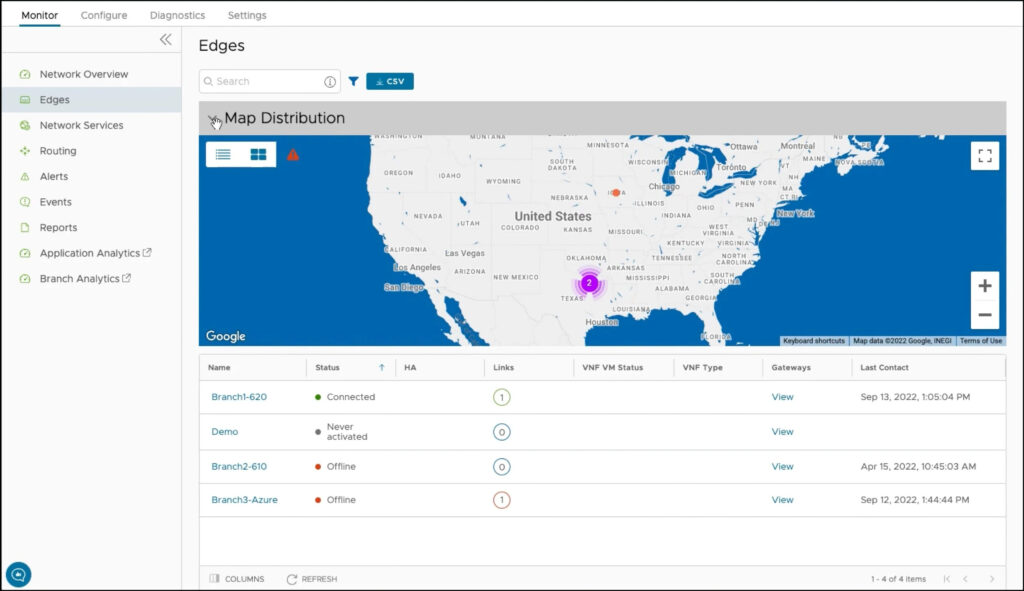
VMware offers a complete cloud-based SASE suite using VeloCloud (acquired in 2017) SD-WAN as the foundation and a global network of more than 100 gateway PoPs and backend connections to all major cloud services. Aside from the usual set of SASE features, VMware adds several unique capabilities, including integration with its NSX firewall and the Workspace ONE Remote Desktop and endpoint management system. Workspace ONE policies automatically set up VPNs and direct users to the closest available SD-WAN PoP and enforce ZTNA policies regardless of which device or local network they happen to be on.
VMware SD-WAN includes AIOps features that analyse link metrics and events to isolate problems and suggest fixes. It also adds application-specific QoS policies to prioritise traffic and guarantee minimum network service levels for critical workloads.
Summary and recommendations
The following table summarises the SASE features of the ten vendors we discussed and it shows that SD-WAN, firewall and basic content filtering (SWG, DLP) are table stakes in this category. Unfortunately, ZTNA is arguably the most critical security feature after a basic firewall and is only supported by half of the vendors surveyed. Indeed, as our year-plus WFH experience demonstrated, simplifying and bolstering the capabilities of basic IPsec VPNs is critically important to delivering transparent, convenient and granular security for employees on remote networks. Thus, when evaluating vendors that don’t embed ZTNA into their service, carefully consider how advanced authentication features including zero-trust, SSO and MFA can be integrated into their service.
SASE Features Vendor Comparison
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | SASE features table | SD-WAN | NGFW | SWG | CASB | DLP | ZTNA |
|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | hyelland | 02/11/2024 05:35 PM | hyelland | 02/11/2024 05:35 PM | Aryaka | ✓ | ✓ | ||||
| 2 | hyelland | 02/11/2024 05:35 PM | hyelland | 02/11/2024 05:35 PM | Cato | ✓ | ✓ | ✓ | ✓ | ✓ | |
| 3 | hyelland | 02/11/2024 05:35 PM | hyelland | 02/11/2024 05:35 PM | Cisco Meraki | ✓ | ✓ | ✓ | ✓ | ||
| 4 | hyelland | 02/11/2024 05:35 PM | hyelland | 02/11/2024 05:35 PM | Cisco SD-WAN | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| 5 | hyelland | 02/11/2024 05:35 PM | hyelland | 02/11/2024 05:35 PM | Citrix | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| 6 | hyelland | 02/11/2024 05:35 PM | hyelland | 02/11/2024 05:35 PM | Open Systems | ✓ | ✓ | ✓ | ✓ | ✓ | |
| 7 | hyelland | 02/11/2024 05:35 PM | hyelland | 02/11/2024 05:35 PM | Oracle | ✓ | ✓ | ||||
| 8 | hyelland | 02/11/2024 05:35 PM | hyelland | 02/11/2024 05:35 PM | Palo Alto | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| 9 | hyelland | 02/11/2024 05:35 PM | hyelland | 02/11/2024 05:35 PM | Versa | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| 10 | hyelland | 02/11/2024 05:35 PM | hyelland | 02/11/2024 05:35 PM | VMware | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| SASE features table | SD-WAN | NGFW | SWG | CASB | DLP | ZTNA |
Limiting our overview to ten vendors required omitting many worthy SASE contenders from companies like Fortinet, Netskope, Watchguard, Zscaler and others. Organisations that don’t already have a strong vendor preference due to current usage and product deployments, should add these to their evaluation list. A thorough process requires weighting the features according to your needs and incorporating non-technical factors like customer support, partnership arrangements and pricing models.