| Implementing SASE and Zero Trust ensures unified security, identity verification and continuous monitoring, enhancing network protection for remote and hybrid workforces. |
SASE Zero Trust: Implementing the Model for Enhanced Network Security Embracing SASE and Zero Trust: A Strategic Roadmap for IT Decision Makers
SASE and Zero Trust are key security concepts for modern systems. SASE defines a singular cohesive security approach across an organisations system and Zero Trust ensures that continuous verification is being conducted in order to best protect it.
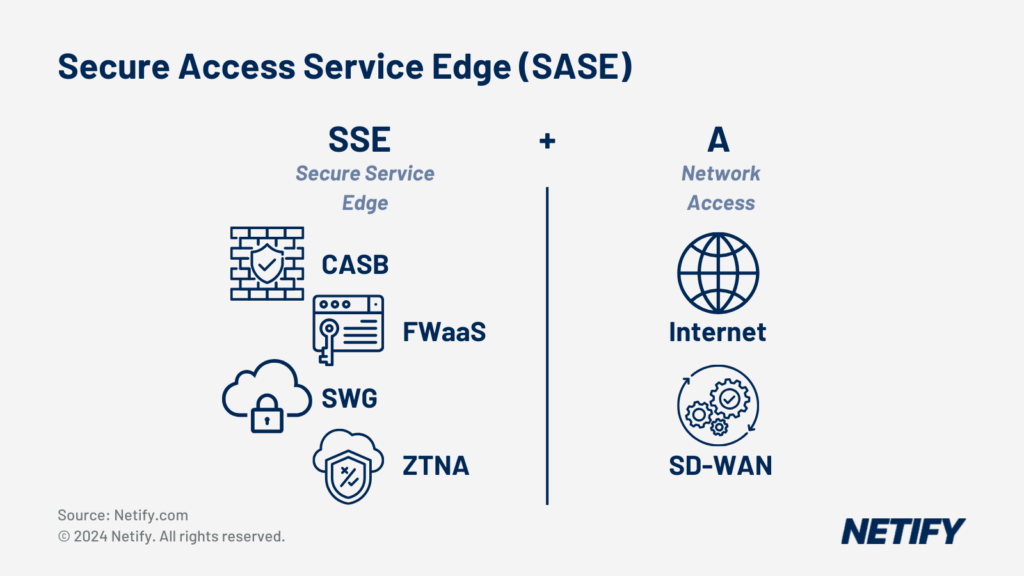
Secure Access Service Edge (SASE) is SSE + SD-WAN (Access)
Understanding SASE and Zero Trust
SASE: The Convergence of Network and Security Services
Secure Access Service Edge (SASE), coined by Gartner, is a cloud-based system architecture that converges Security-as-a-Service (SaaS) & Networking-as-a-Service (NaaS) for organisations. This means that SASE provides secure network services at any given access point or application the user connects to.
Traditionally, within an organisation there are multiple different systems that a user may have access to and typically this would mean that, due to each system having their own security policies, the permissions available to the user are misaligned. SASE seeks to rectify this by providing a unified approach to security across the board.
Zero Trust: A Shift in Security Paradigm
In the past, the use of in-house system architectures had helped standardise a perimeter-security model. This implies that any device connecting to the network from within in-house can be assumed to be authenticated and thus the network is designed to primarily prevent threats from outside the network.
Zero Trust Architecture with SD-WAN
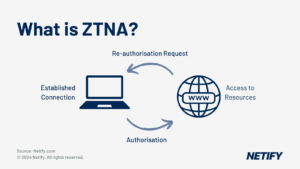
Zero Trust is an identity-centric security strategy designed to provide no trust based access to systems and therefore moves the boundary to be from the system to the connecting device. There are three core principles to Zero Trust:
- “Never trust, always verify”: Access trust is withheld until a full identity check is completed regardless of the device or application attempting to access the system. By undergoing this trust brokering process, this treats each connection as if it were entirely new and ensures there is sufficient authentication and authorisation for the connecting device.
- Least privilege for context: After the verification process is complete, the system must consider the requirements of the application and the range of privileges the user should have access to. This will provide the user with the minimal access required in order to carry out their tasks. The user should therefore have no visibility or access to parts of the system outside their permitted scope.
- Device security: Finally, if all identification and privilege checks complete successfully, the system must validate that the user’s device is secure. This validation test may differ depending on the system use case, however common checks include: compliance tests, checking if the antivirus is running as expected and meeting additional conditional criteria.
Following access being granted, the system must continuously monitor and validate the system. If there are any changes to any of the three principles the connection must be re-evaluated and should they no longer be deemed valid, the system must assume it has been compromised and revoke access.
The Strategic Importance of SASE and Zero Trust for Organisations
As per a survey by Gartner, 74% of CFOs intend to shift employees to work remotely on a permanent basis. This emphasises the importance of system availability from a range of geographical locations. To ensure systems are not compromised, robust security must be put in place. SASE cloud enables this remote access in a secure manner and Zero Trust architecture compliments this to protect against unauthorised remote access.
Zero Trust: Enhanced Security Posture
When considering a perimeter model used by older systems with remote workers this means that, for the modern organisation, the perimeter would be extended to user’s home networks. As other devices on the home networks would be within the perimeter, these devices increase the level of risk posed to the organisation’s system. Due to this, attackers may find it easier to gain access into the network.
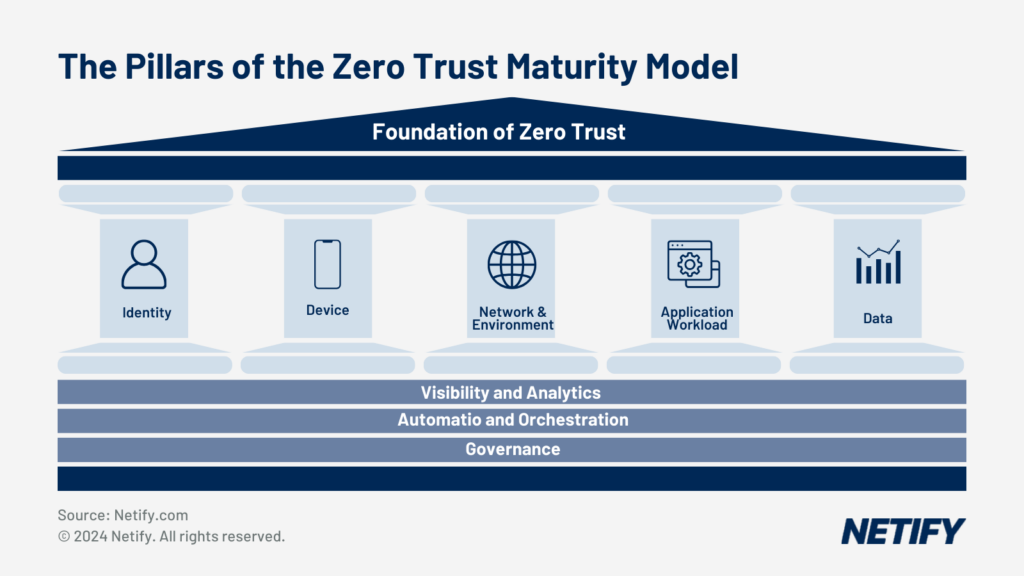
The five pillars of the Zero Trust Maturity Model include: Identify, Device, Network & Environment, Application Workload and Data.
The identity-centric Zero Trust model assists with mitigating this threat by the three step protocol: authenticate user, provide least access privileges and monitor device security by providing additional security for every connection and does not assume that a connection is valid.
By enhancing the security posture, this helps:
- Reduce the risk of insider threat
- Secure the remote workforce
- Preserve customer privacy
- Protect the system and its data
SASE and Zero Trust: Optimised Performance and User Experience
The average organisation uses 80 SaaS applications as part of their workflow, each potentially with their own security policies and differing levels of privileges required for internal resources. By providing a consistent security policy in the form of SASE and Zero Trust, this benefits the user experience due to familiarity in policies, the expectations they can have for any given component of the system and the same level of availability regardless of whether they are accessing the system within the office or from home.
When comparing the use of SASE cloud connections to the traditionally-used VPN system to access the network, performance is increased. Previously the VPN connection would need to undergo server-side inspection which causes a bottleneck about the inspection device and thus overall latency when accessing the system. By utilising SASE in the cloud, the verification process is handled by distributed inspection engines equipped from Secure Web Gateway (SWG) & Firewall-as-a-Service (FWaaS) vendors. This means that the distributed nature of the inspection engines spreads load and can therefore outperform inspection devices used with VPN connections.
SASE and Zero Trust: Simplified IT Complexity
By removing the need for inspection devices, SASE cloud solutions also reduce system complexity as additional circuitry to accommodate these devices on the network is no longer required, this reduces the overall cost of system circuitry.
Within a SASE Zero Trust solution, there is a consistent security policy across the system. This means that IT decision makers should only need to make any given policy change once and the updated policy remains consistent throughout the system. By keeping consistency, this reduces the IT complexity of the system as there is no need to consider misaligned policies that may pose security risks.
Zero Trust: Implementation Considerations for IT Decision Makers
Prior to integrating SASE & Zero Trust architectures, IT decision makers must consider the potential risks and required access levels for each system component.
Zero Trust: Assessing Organisational Readiness
When assessing organisational readiness, it must be noted that traditional security systems can no longer be deemed adequate, highlighting the need for a consolidated framework from which to structure the organisation’s system.
By evaluating the system, this details how the system may migrate to SASE Zero Trust and prevent unnecessary permissions being given to users whilst also making sure that the change does not hinder expected use.
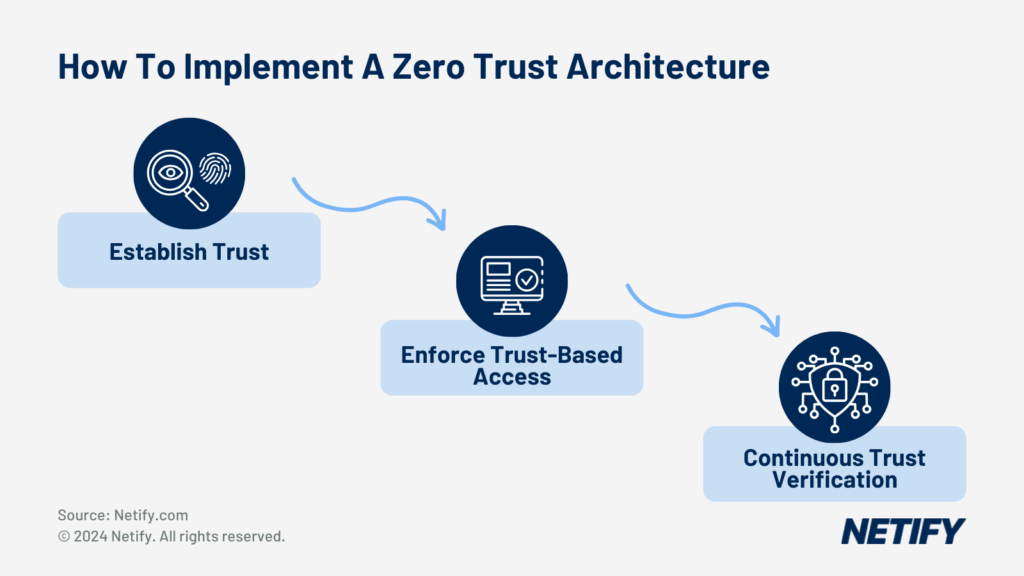
Implementing a Zero Trust Architecture requires establishing trust, enforcing trust-based access and continuous re-verification.
Zero Trust: Developing a Phased Implementation Strategy
It is important to consider the preparation tasks prior to the change from a network-centric model to an identity-centric model, as well as evaluating the existing security components and determining critical systems/data reside. For example, within SASE cloud implementations, the intrusion prevention system (IPS) is all handled in the cloud and thus legacy IPS systems can be phased out.
As Zero Trust assumes that any connection that doesn’t pass all checks is a breach to the system, IT decision makers should consider additional security implementations such as microsegmentation and software defined perimeters (SDPs). These prevent potential attackers from lateral movement across the system and thus helps confine breaches to a singular subsystem.
Should access be required on premises as well as remotely, software-defined wide-area networking (SD-WAN) solutions offer an additional optimisation to the SASE Zero Trust architecture. SD-WAN is capable of service chaining security inspection to the secure web gateway when in-house connections are required, preventing the need for in-house connections to be routed entirely via the cloud (which would add additional latency).
With cloud access security brokers (CASB) visibility, the security policies are centralised to define the access enforcement to cloud applications and quarantine users with suspicious behaviour.
Organisations must constantly monitor systems to ensure that, as the system develops, it remains up-to-date with the latest solutions and is able to cope with new threats.
Zero Trust: Choosing the Right Partners
As there are many different providers for SASE and Zero Trust architecture solutions, IT decision makers are advised to evaluate the needs of their organisation before choosing a provider.
Cato Networks (CatoSASE), Fortinet (FortiSASE), Paloalto (PrismaSASE) and Netskope (Netskope SASE) each provide an integration of SASE services for their cloud networks with Fortinet and Paloalto proving to be prominent in the sector due to their ability to offer Next-Generation Firewalls (NGFW) and Secure Web Gateways (SWG), which assist with fulfilling the Zero Trust model.
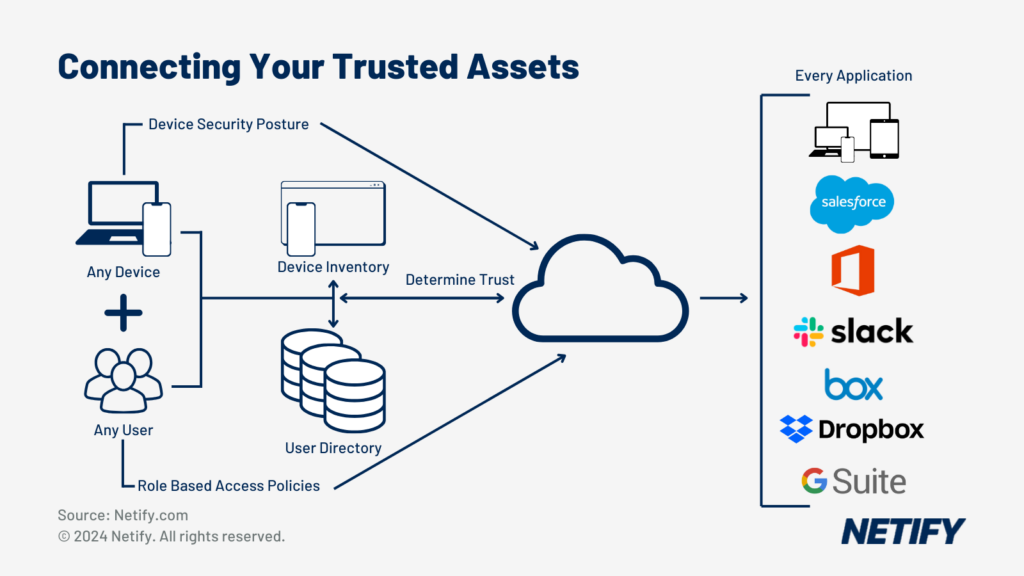
Zero Trust Network Access (ZTNA) within SASE
Fortinet stands out not only for their intuitive user interface, unified network, security visibility and its ease of configurability but also for its microbranch security which is a unique capability. Fortinet access points and extenders intelligently offload traffic to a SASE location for comprehensive security inspection at scale, for all devices. This allows a new approach to cloud-based security by extending enterprise-grade protection to microbranches without additional appliances, agents, or services.