SSE focuses solely on cloud-based security features, such as CASB, FWaaS, SWG and ZTNA. However, SASE builds on this by coupling SSE’s security capabilities with the access of SD-WAN. |
Over 38% (20 million people) of the British population are now working from home at least once a week. There are many benefits to this but one main concern is the need to access the corporate network from anywhere in a secure way. This is where Secure Access Service Edge (SASE) comes into play.
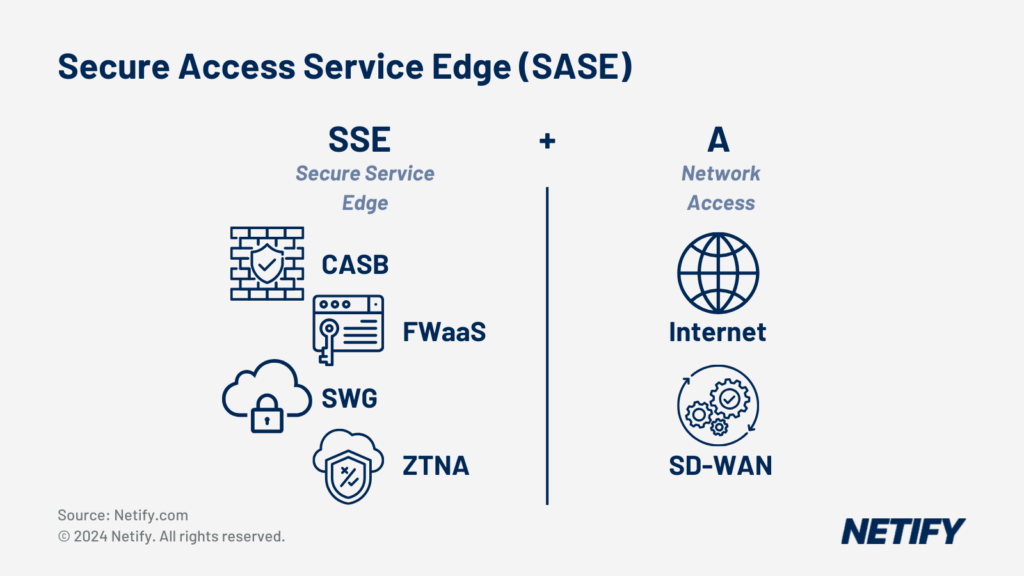
- Secure Access Service Edge (SASE) is SSE + SD-WAN (Access)
Instead of relying solely on Virtual Private Networks (VPNs) to access work resources, the rise in demand for Software-as-a-Service applications has called for a safer and more direct approach.
A recent report from Netskope has indicated the average workplace uses almost one thousand SaaS applications. Long gone are the days of redirecting all user traffic back to a centralised point. Applications like the Office 365 suite are designed for direct access by users regardless of geographic location. Doing so saves on latency and cost whilst offering a better user experience.
SASE fixes these issues by combining networking and security services across globally scattered Points of Presence (PoPs) locations. There are many SASE vendors to choose from who offer services globally. All top providers have PoP locations across each continent and partner up with ISPs to ensure a premium user experience anywhere. User experience is enhanced by SASE through the enforcement of security policies while accessing SaaS applications from any location. SASE architecture is made up various technologies but the main four are:
- Secure Web Gateway: Protects and connects users to cloud services, encompassing URL filtering, the detection and blocking of harmful code with the inclusion of firewall services in most instances.
- Cloud Access Security Brokers (CASB): Affords meticulous access control and safeguards for SaaS platforms such as Office 365 and Salesforce.
- Zero Trust Network Access (ZTNA): Facilitates connections to private resources situated in a corporate network or data centre.
- SD-WAN: Assists branch locations and headquarters in intelligently routing traffic across various network paths.
- Zero Trust Architecture with SD-WAN
It is important to note that SASE is not a single technology but a collection of services, commonly offered in a unified platform, which oversees access and policies. With predictions from Gartner that most companies will migrate towards a SASE solution by 2025, this is something that all businesses should be consulting. Unsurprisingly, merging security and networking into one service has proven difficult and resulted in a few options for those seeking the best of both worlds.
Fundamentals of SASE
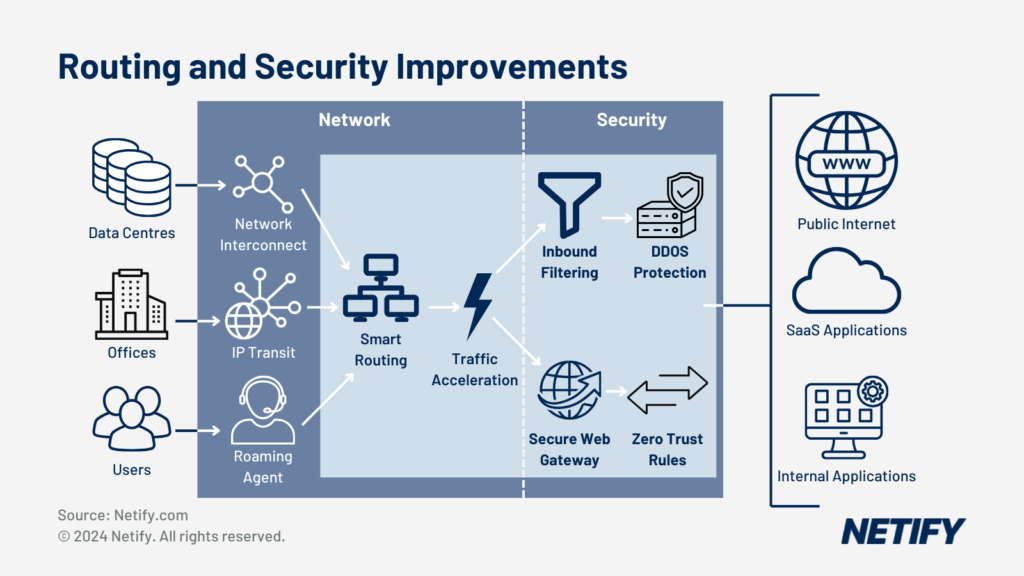
- SASE Routing and Security Improvements
SASE is composed of both security and networking services which are bundled into a unified, cloud-native service. This results in customers benefiting from reduced efforts and costs required to maintain their complex systems. Below are some of the core components:
Secure Web Gateways: A Secure Web Gateway (SWG) is a security solution which acts as a barrier between the user’s and the internet. A secure bridge is provided to user’s trying to remotely access cloud-based services. Essential features include web address filtering, blocking of harmful content and the monitoring and controlling of web traffic. SWGs safeguard user’s against web-based threats.
Cloud Access Security Brokers: CASB is a security solution which is designed to provide detailed access management and protection for SaaS platforms such as Office 365 and Salesforce. It enables visibility of user behaviour and the safeguarding of data as it leaves the private network and moves to the cloud.
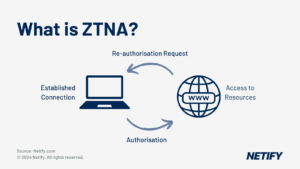
Zero Trust Network Access: ZTNA is basically the act of not trusting anyone, until they have verified themselves. Until verification is achieved they won’t be able to access any resources. In the past user’s would be “trusted but verified” now it’s “never trust, always verify”. Access is limited to only what is completely necessary for a specific task.
SD-WAN is a modern concept for a simplified management of traditional WANs. Business sites are connected using multiple transport mediums such as MPLS, broadband and LTE using intelligent routing based on the best available path. Partnerships with security providers enable this tech to delegate inspection duties to nearby SASE PoPs for safer connections.
Market Forecast for Secure Access Service Edge
As more businesses use cloud-based tools, the SASE model is constantly evolving. A Netskope study showed how popular and essential cloud services have become. With this comes a rise in threats and the vital need for powerful security solutions. The biggest influence on the cybersecurity market is the current trend of hybrid and remote working, which doubtfully will be changing anytime soon. The global SASE market is projected to be worth over $10 billion by 2026 as companies are allocating more budget to upgrade their network security. With any billion dollar industry the competition is tight and mostly dominated by large vendors with major market shares. This results in plenty of acquisitions and merges with the smaller players.
Overcoming Obstacles in SASE Adoption
While SASE offers many benefits, it’s unsurprising that organisations face obstacles when attempting to adopt this new model. There are potential challenges to face but with careful research and planning a smooth transition is possible.
Integration can be an issue as trying to blend network and security from multiple vendors can be difficult. It’s a good idea to identify what services you require and set out looking for a vendor which can provide as many of these as possible. Look out for partnerships between vendors and ISPs. The best case scenario is having a singular SASE solution from one provider.
Another obstacle in adopting SASE is the complexity in management. Orchestrating all SASE components requires a centralised management platform. This will come with a learning curve so evaluating vendors and selecting one which has a powerful platform for management is crucial. It’s worthwhile considering if you pay extra for a managed service as opposed to self managing.
What is SSE?
Secure Service Edge (SSE) Features
Recognising the challenges in seamlessly uniting SASE components, in 2021 Gartner introduced Security Service Edge (SSE). SSE focuses on purely the security elements of SASE, mainly Secure Web Gateway (SWG), Cloud Access Security Broker (CASB) and Zero Trust Network Access (ZTNA). Concentrating on just the security services is ideal for organisations that might not require networking services like SD-WAN. It also allows customers to pick and choose networking and security vendors individually to better suit their requirements. The fundamental services that make up SSE are the security aspects of SASE. SWG, ZTNA and CASB to name a few. Below are a few more components:
Firewall-as-a-Service: FWaaS is a cloud approach to traditional firewalls which provides protection both inbound and outbound within a network. The use of this eliminates the need for physical on premises hardware at each location. It isn’t feasible for remote workers to each have a firewall installed in their homes. FWaaS offers the same layer of protection through enforced security policies across the entire network. A benefit of this is the ease of scalability making it a cost-effective solution for safeguarding your network.
Sandboxing: In terms of SSE, sandboxing is a security mechanism used to isolate and analyse potentially malicious files within a controlled environment. Suspicious items can be examined without causing a threat to the broader network.
Data Loss Prevention: DLP is a security measure aimed to safeguard sensitive information. This is done via policies to control, monitor, detect and prevent any unauthorised transmission or exposure of sensitive data. For example, files that are flagged as highly confidential won’t be able to be sent via email or transferred to a USB stick.
Advancements in Secure Service Edge: As mentioned earlier, Secure Service Edge is similar to SASE just without the network component. Services within SSE include SWG, CASB, ZTNA and additional security features such as Data Loss Prevention (DLP), Network Access Control (NAC) and sandboxing. Companies that no longer have physical sites have no need for SD-WAN and are best suited for a SSE solution.
As with other industries, the incorporation of machine learning (ML) and artificial intelligence (AI) has made its way to SSE. ML and AI are utilised within the monitoring and detection of anomalies and threads. This helps prevent both known and unknown malware, ransomware and other attacks.
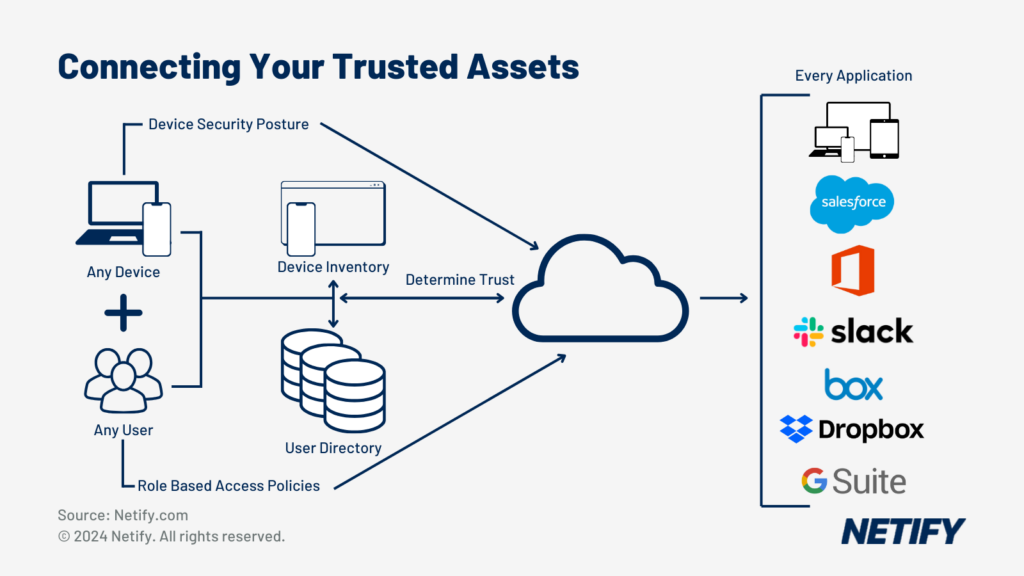
Zero Trust Network Access (ZTNA) within SASE
Differentiating SASE from SSE
As workplaces now offer hybrid working models, SASE helps enforce the same level of protection no matter the location or device. SASE takes a wider approach to securing and optimising access. Meanwhile, SSE suits companies that are entirely remote or don’t require SD-WAN. When deciding between SASE and SSE specific needs for on-site connectivity should be assessed. Basically, SSE is the security aspect of SASE.
In summary, both SASE and SSE aim to deliver powerful yet simplified security models for today’s hybrid workplaces. The dynamic shift towards remote working has accelerated the critical importance of having a secure yet efficient access into the network. As companies increasingly rely on cloud-based tools and applications, the need for robust and scalable solutions are rising. SASE takes a holistic approach of integrating both networking and security services for a unified user experience. Engineers benefit from a singular platform for configuration and management. SSE focuses solely on the security components, allowing flexibility in choosing the best vendors for each networking and security individually. The right choice is dependent on each organisation’s unique IT infrastructure, budget and long term goals.
For both it is vital to consider the implementation and transition in phases to ensure a smooth deployment. This is something that all vendors should offer to help with. Careful planning and execution for both SASE and SSE will result in a secure network allowing for access from anywhere.
Most importantly, we should understand why it makes sense to move toward SASE or SSE. Today, most organisations are going to reach a point where similar driving factors like cloud adoption and remote workforce enablement will justify the business and architecture changes necessary to move from traditional network security solutions toward SASE and SSE solutions. Any organisation looking to embrace the cloud should be looking at SASE and SSE solutions, as they provide a way to deliver anything to or from the cloud securely. Finally, keep in mind that SSE solutions are there for organisations looking to incrementally make the move to the cloud or toward a full SASE solution, while SASE is more of a global end-state solution where an organistions networks and security management are truly unified.