| The worldwide CrowdStrike Windows issues, caused by a faulty update to their Falcon Sensor software, led to widespread BSOD errors and boot loops, affecting millions of devices globally. |
Widespread outages are being experienced worldwide, affecting a wide range of Windows devices. The source of the issue is a faulty update from the cybersecurity provider CrowdStrike to their Falcon Sensor software, which is widely used to manage the cybersecurity of both Windows PCs and servers. Having started affecting devices as of 19th July 2024, the update is causing Windows PCs to crash and experience the ‘Blue Screen of Death’ (BSOD) error, getting stuck in boot loops and ultimately rendering systems unusable. So far, a reported 8.5 million Windows devices have been affected globally by the issues and has caused significant impact across various sectors, despite this figure representing less than 1% of all Windows machines.
Impact
Having already affected much of Australia’s banks, airlines and TV broadcasters, businesses across Europe have begun their working day and are also now reporting similar issues. The breadth of this issue hasn’t yet been fully recognised with retailers, and even emergency services in various countries such as the United States, United Kingdom, Australia, and India all facing issues due to the downtime.
CrowdStrike’s Response
CrowdStrike has now acknowledged the problem and, after investigating the cause of the outage, have concluded that the issue was related to “Channel Files” within the Falcon sensor’s behavioural protection mechanisms. These updates, although not kernel drivers, influenced systems startup processes, which led to the BSOD issues.
Earlier findings appeared to show that the issue stemmed from the related csagent.sys driver in multiple versions of CrowdStrike’s Falcon sensor software and thus a short-term fix had previously been suggested with regards to this driver.
Short-Term Fix
Businesses experiencing this issue will undoubtedly be looking for any method to regain access to their systems and, as a short-term solution, CrowdStrike has suggested the best workaround currently is to boot affected systems into Safe Mode or the Windows Recovery Environment, locating and deleting the problematic driver file, and then rebooting normally.
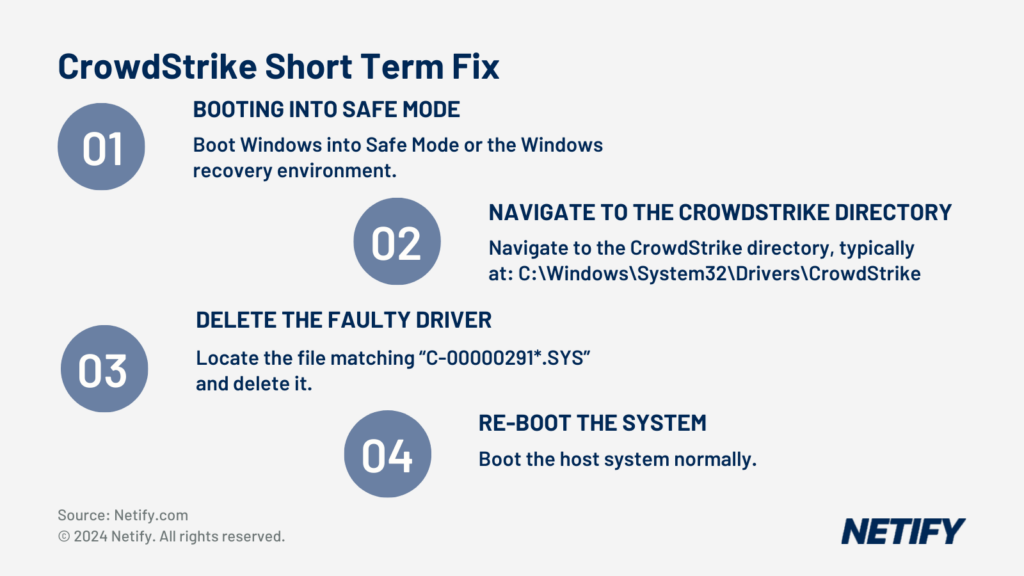
- CrowdStrike Short Term Workaround by Deleting Driver
Long-Term Fix
To aid with recovery, Microsoft has developed a new tool designed to assist affected systems. This tool aims to accelerate the recovery process, especially for critical sectors like healthcare, which have been severely impacted by the outage. Additionally, CrowdStrike and Microsoft are actively working with affected customers to mitigate the issue and restore normal operations, with Microsoft deploying engineers to assist customers resolve issues.
Cautions
Amongst the panic to get systems back online, malicious actors have been reportedly exploiting the situation, providing affected customers with malware disguised as official CrowdStrike fixes. The malware, known as Daolpu has been sent to customers in phishing emails, designed for users to install it onto their computer, allowing Daolpu to steal information. This information includes account credentials, browser histories and authentication cookies, which can cause major damage to affected users and systems. CrowdStrike has warned their customers that they must ensure they are communicating with official representatives and following the provided technical guidance in order to protect their business network.
Implications
Whilst we won’t know the full implications straight away, this incident highlights the risks associated with relying on a single cybersecurity vendor and underscores the fragility of business computer infrastructure.
As organisations work to resolve the issues caused by the CrowdStrike outage, we’ll look to provide you with any updates as new information becomes available.