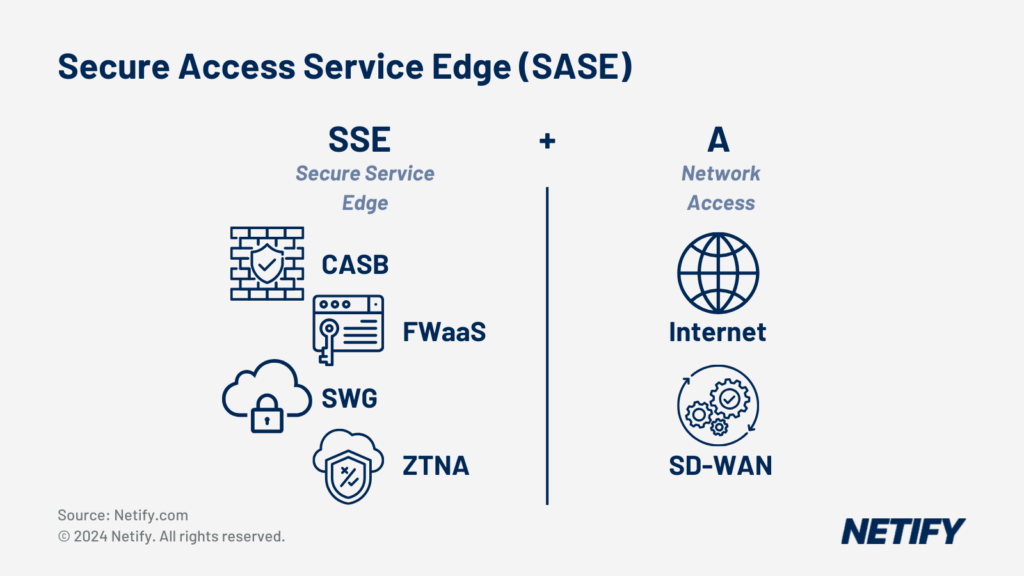
| The Gartner SASE combines SD-WAN with cloud-based security (CASB, SWG, FWaaS and ZTNA). |
SASE is a concept brought to the market by Gartner. It represents the convergence of networking and security by combining CASB, DNS protection, Firewall-as-a-services, SD WAN and ZTNA delivered via cloud service infrastructure.
The SASE framework (Secure Access Service Edge) model became known to the IT community via a report entitled The Future of Network Security in the Cloud, which was written back in August 2019.
The report recognised the shift in how Enterprise business requires a broad set of security technologies to deliver SD WAN access globally from wherever the user is located. The concepts outline the shift to a public cloud-first model where users are demanding access to SaaS and IaaS application resources from any location or device. As users become more mobile, hackers recognise the vulnerabilities which exist when users are no longer mostly based behind the corporate office Firewall. To meet the demands of remote network architecture with public SaaS and IaaS adoption, a comprehensive security stack is required.
In summary, there are four characteristics of public cloud-first organisations:
Inversion of network architecture from the data centre and branch to the remote user identity. The user is the ‘context’ which must be evaluated with individual policies applied.
Cloud-native businesses mean data is located inside virtual cloud resources and not the traditional data centre.
Edge-based computing required a global mesh of both network and security which connect users, offices and hardware wherever they are located.
Globally distributed resources require the connection of an identity rather than a physical device with applied security capabilities.
The change in network behaviour is best outlined when considering the flow of traffic on legacy MPLS WAN services where data is generally sent between physical locations with applications residing at private data centre locations. The core data centre approach dictates a centralised security architecture around these traffic flows.
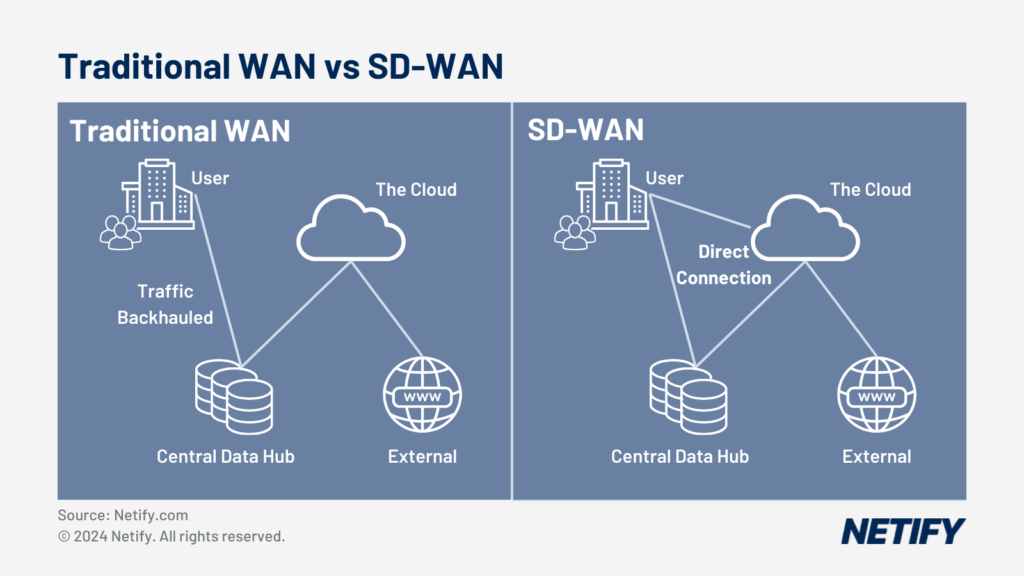
The diagram above details how traffic is sent from site to site via MPLS rather than direct to public cloud resources via the Internet and SD WAN.
“..private VPN topology is no longer fit for purpose as users have de-centralised their network activity..”
Public cloud adoption means MPLS VPN is becoming less popular.
While MPLS remains a component of good hybrid architecture, private VPN topology is no longer fit for purpose as users have de-centralized their network activity. In the main, reasons include:
- Network device intelligence is downloaded from pubic cloud security gateways in line with SDN concepts (Software Defined Networks).
- IT teams are being asked to save costs by replacing MPLS with DIA.
- Traffic no longer resides within private data centres with almost all organisations adopting some form of public Cloud from Office 365 to multiple bespoke SaaS and IaaS applications which reside in Azure, AWS or Google Cloud.
- BYOD (Bring your own device) and remote working mean there is no longer a network permitter as access is practically everywhere.
- Maintaining application performance requires comprehensive reporting insights and features such as QoS (Quality of Service) and FEC (Forward Error Correction).
- Support of SD WAN is more straightforward but requires extensive conceptual knowledge.
- SD WAN works best with DIA (Direct Internet Access) requiring comprehensive and advanced security.
At Netify, we are witnessing fundamental changes across initial vendor comparison conversations due to the complete inversion of the legacy WAN architecture. IT teams are now faced with the challenge of how to deal with security threats on a realtime basis while maintaining consistent and reliable network access. The further challenge is to not only understand SASE concepts but also to evaluate implementation across each vendor. Reporting on false security positives are one example of how the Enterprise is challenged to maintain network uptime based on risks.
As businesses continue to adopt SASE, the market will mature into SDP (Software Defined Perimeter) from SD WAN. The concepts behind SDP are based around remote WAN connectivity which may originate from multiple user types across any connection from 4G/5G to Broadband and Ethernet DIA circuits.
SASE adoption is now not an optional feature-set for any business with SaaS (Software as a Service) and IaaS (Infrastructure an a Service) public cloud and remote working. Gartner state that 40% of Enterprise business will consider adoption of SASE WAN technologies by 2024 to meet the needs of cybersecurity. The rise in interest is polarising when compared to 2018 where less than 1% of businesses were actively investigating SASE.
The shift to SD WAN from MPLS clearly shows how traffic is now routed to the Internet which requires a full security stack.
What does a SASE security service consist of and how can the concept help your business?
The typical first step organizations move through when adopting SD WAN is to combine cloud-native delivered services which include:
- DNS Security – Domain Name Security is required when any user connects to websites on the Internet. Application of DNS layer security is an effective method of stopping most attacks.
- Secure Web Gateway (SWG) – SWG is a Cloud-based web proxy with multiple features such as malware detection, file sandboxing, dynamic threat intelligence, SSL (Secure Socket Layer) decryption, application and content filtering and finally DLP (Data Loss Protection).
- NGFW (Next-Generation Firewall) Firewall as a Service – Cloud delivery of Firewall functionality including protection of non-web Internet traffic (i.e. IP, port and protocol protection) with layer 7 application control.
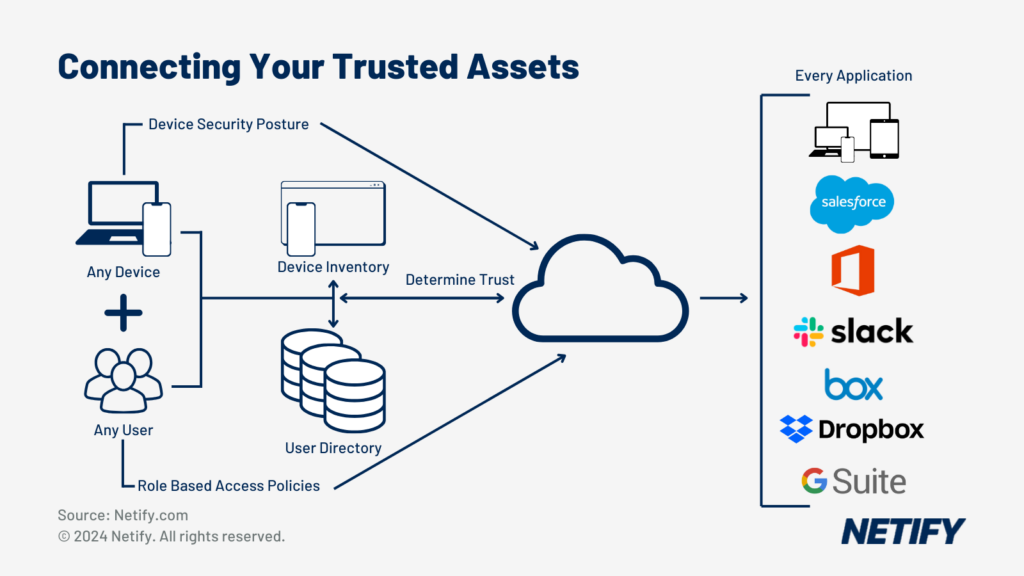
- CASB (Cloud Access Security Broker) – CASB is needed to uphold security policies across SaaS application access. Unauthorised applications or users outside of your organisation are quickly identified and blocked, CASB is capable of using AI (Artificial Intelligence) to help detect abnormal user activity.
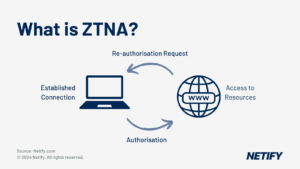
- ZTNA (Zero Trust Network Access) – “Never trust and always verify” via multi-factor authentication before any device is able to connect.
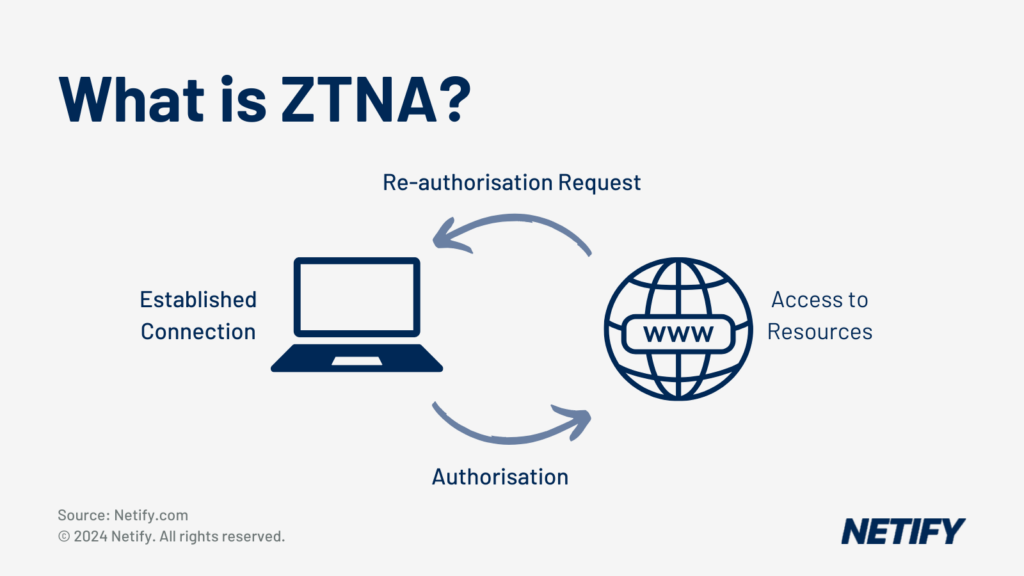
Dynamic Edge Protection is needed to secure traffic from branch, Wi-Fi and remote worker directed to the Internet.
In the past, organisations have experienced issues and problems while trying to develop a complete technology stack to meet their security requirements. IT teams added elements continuously to the security stack, which created complexity and expense. This siloed approach to security created major issues as each product generated huge amounts of data across threats which required manual evaluation. SASE technologies are not brand new, but the concept represents the aggregation of functionality. In other words, SASE represents the required stack of technology which is Cloud-based and designed to evolve with ever-increasing threats.
The following represents statistics surrounding Cloud and network evolution based on the continued decentralisation of networks and public cloud applications:
- 80% of businesses and organisations are moving to DIA.
- 76% are using or considering some form of SD WAN.
- 42% of branch office security deployments take over 30 days.
- 68% of users are remote and connecting from multiple locations representing the source of network security compromise and attacks.
75% of Enterprise traffic is directed to SaaS, IaaS and Internet addresses. The SASE model is required to secure all traffic.
Source: Cisco Umbrella.
What are the business benefits of SASE architecture?
Globally distributed resources require the connection of an identity rather than a physical device with applied security capabilities.
SASE is a concept which surrounds the consolidation of network and security. We discussed how the traditional security stack was complex and difficult to manage and required IT teams to review reports consistently.
With the above in mind, SASE business benefits include:
- Reduced cost and complexity – consolidation of the WAN and security in one device is now possible.
- Support for remote and mobile users.
- SD WAN will optimize application access with policy-based routing with security integration.
- Consistent, secure SD WAN policies.
- Cloud threat updates without the need to refresh hardware.
Cato Networks

Cato Networks are recognised as the first SD WAN SASE platform with private-backbone convergence, complete security stack and support across Cloud and remote user devices. The Cato solution follows the CNaC (Cloud Native Architecture), which means they own the entire technology stack end to end for effective support. Their private backbone is great for global businesses which benefit from end to end traffic delivery and a 99.999% uptime guarantee.
Versa Networks

Versa Titan is a recently launched re-purpose of their full SD WAN product which was designed for large complex network needs. With SASE security and a cost-effective price point, Versa secure SD WAN represents a good option for businesses looking to adopt a pure Internet model (rather than leveraging a private backbone or public gateways).
Open Systems

Open Systems have a strong history of security capability from their inception as a security integrator in 1990. With deployments and operations in over 180 countries, Open Systems represent a good option for businesses looking to deploy their WAN based on security fundamentals.
Fortinet

Fortinet are well known for their history within the security sector via their own ASIC developed hardware platform. Netify recommends engaging with an accredited Fortinet integrator in order to make the most of their platform, which offers a granular approach to SASE security. One key differentiator is their support for endpoint security (not often found within the SD WAN space) together with both the WAN and LAN.
Palo Alto

Alongside Fortinet, Palo Alto are a well-known security provider and Gartner NGFW (Next-Generation Firewall) leader. To improve its SD WAN offering, Palo Alto recently acquired Cloud Genix. Although the two products are not yet fully integrated, Cloud Genix offers some interesting features such as layer 7 packet measurement to help improve application performance.
“Some of us believe the true cloud-native way to buy SASE is via a single vendor platform for both SD WAN and SASE security.”
Vendor either offer end to end SASE or integrate other solutions.
Should you buy from a SASE vendor or from a vendor and SASE partner?
The team at Netify are often asked about whether to buy SASE security capability from a single vendor or a vendor with SASE partnership. Some of us believe the true cloud-native way to buy SASE is via a single vendor platform for both SD WAN and SASE security. And others believe the Enterprise should build their technology stack based on best of breed solutions and services.
The follow represent the available procurement options:
- SD WAN vendor with SASE – buying an SD WAN solution with SASE built-in is perhaps to the truest representation of the Gartner cloud-native SASE architecture. The clear benefit is across the end to end ownership of the technology stack by one support team (i.e. the vendor).
- SD WAN vendor with SASE partnership – there are a number of SD WAN vendors offering SASE security via partnerships with companies such as Zscaler or Check Point. While there is an integration of the SASE security elements into the SD WAN management interface, the technology stack is not managed entirely by one vendor.
- IT services integrator – specialist company with security accreditations enabling their team to offer bespoke services across SD WAN and SASE. Using an integrator can often be a good idea if they add value to other areas within your organization.
- Service Provider – the traditional telcos (think Verizon, AT&T, British Telecom) offer SD WAN partnerships which may include SD WAN vendors with built-in SASE. One of the main criticism of service provider solutions is levelled at poor processes which essentially remove some of the agility associated with Software WAN services.
What else is there to consider when buying SASE solutions?
While the SASE network security architecture model is fundamentally applied to any vendor supporting the technologies we have mentioned in this article (ZTNA, SWG, CASB, FWaaS), there are differences in their approach to management and delivery.
False positives remain one of the most frustrating aspects of security logs and statistics. These flags require IT teams to identify whether the threat (intrusion) is valid or has been created by an unknown aspect of a SaaS application. As with all aspects of complex telecoms, there are vendors leading the way with AI to and integration with 3rd party databases to combat this issue. The question is, how do you know if the vendors you are selecting are leading the field within the area of false positives.
The above issue represents one single aspect and challenge of procuring SASE; there will be others which are out of scope for this article. Netify recommends booking demos of capability to help you evaluate the strengths and weaknesses of each SASE solution which can be easily organised via the Netify market network or quick assessment.