The 20 top EDR vendors are:
|
In this article, you’ll find The Netify top/best 20 EDR vendors and service providers which fit the needs of most mid-market and Enterprise businesses.
Top 20 EDR Vendors
Table of Contents
A single attack from an advanced threat actor can cost millions of dollars and possibly even lives. The importance of security solutions for protecting companies, their data, and their users’ or customers’ data is becoming increasingly recognisable, even by organisations who aren’t the most security-conscious. As the enterprise technology landscape changes and evolves, so must the security products, services and tools that we use to provide an effective defence. As technology, device counts, digital information and operations in the enterprise grow, so too does the attack surface, which translates to a need for more coverage than ever before to keep everything safe.
Not too long ago, signature-based antivirus applications were considered a ‘silver bullet’ for protecting most of the endpoint attack surface. While this was never really true, antivirus applications were relatively effective against malicious files which often served as the delivery mechanism for common attacks ranging from simple to sophisticated. Fast forward to today, and you’ll find that this technology is only a small piece of what you need to have a chance in defending endpoints against modern threats. This is the problem which Endpoint Detection and Response (EDR) solutions aim to solve.
Many people consider EDR tools to be an evolution of antivirus applications. They are deployed in a similar manner, and some EDR vendors position themselves this way in the market with some even calling their solutions next-generation antivirus. Almost all EDR solutions incorporate some form of signature-based malware detection, but they are a far cry from your grandfather’s antivirus application.
Security teams are looking for solutions that they hope will prevent breaches, or at least enable them to mount an effective response and minimise the chaos which follows. Vendors across the cybersecurity industry are providing new and innovative approaches to meet this challenge. It is important to find the right solution for any individual organisation based on their needs and business processes – especially when you’re dealing with endpoints that people use to do their jobs every day. In a marketplace filled with choices for endpoint security products, CISOs will succeed when they’re able to align their business needs with products that offer the most complementary technologies whether it be machine learning artificial intelligence, open architecture, agentless deployment, cloud-native, or on-premises.
Questions to ask your EDR vendor
- Do you deploy a single agent, no agent, or multiple agents?
- Do you have an on-premises, cloud or hybrid solution available?
- Does the solution stand alone as a complete endpoint security solution, or is it highly recommended (or even required) to pair with another security product?.
- Does the solution provide online and offline offerings or is an Internet connection required?
- What type of resource overhead is required on our endpoints to properly implement this solution?
- Is there a path to a single-pane-of-glass security solution beyond the endpoints, or are multiple management interfaces required?
- Does this solution lock me into a single vendor for complementary security solutions or is this solution compatible with the greater security ecosystem through integration?
- Is Managed Detection and Response (MDR) offering available, or is the solution designed for an in-house team of trained Security Operations Centre (SOC) operators and analysts?
- What is the pricing and licensing model, and will I be expected to pay separately for support?
- Do you offer professional services for implementation and upgrade assistance and are these included in subscription fees or additional?
- Are you migrating from a legacy anti-virus solution, or keeping a separate next-generation antivirus solution (NGAV) in place? Consider whether you want to run EDR alongside antivirus, or whether you’re replacing antivirus completely. With this in mind, choose solutions that are known to play-well-with others will be necessary if you want to deploy EDR alongside another antivirus solution, or choose solutions that have built-in NGAV features AND make replacing the existing solution as easy as possible. For instance, McAfee has leading NGAV functionality and offers migration tools, but they likely won’t play well on the same endpoints as the another legacy AV or NGAV solution. In that case, Panda’s lightweight agent could be a good choice to deploy alongside an AV solution.
- Do you have a specific requirement driving the need for EDR but you’re happy with the rest of your security stack? If not, you may want to consider choosing an EDR solution from a vendor like Palo Alto or Cisco who have large complementary security portfolios. In contrast, if you are a small business and are just looking to upgrade your legacy antivirus software, then any EDR solution that has built-in NGAV may be the only solution you need.
- Do we have staff to manage, deploy, maintain and configure the solution as well as analysts to investigate incidents and alerts? If not, consider solutions that offer managed detection and response (MDR).
- What type of environment(s) does the solution we implement need to support? For instance, if your organisation is starting to embrace the cloud you should consider hybrid solutions or if your organisation has been an early adopter and is already fully on the cloud you would want to avoid hybrid and on-premises solutions. Or if your organisation is fully on-premises without a the ability to move to the cloud for regulatory reasons, knowing this will help narrow down the available solution providers and avoid making an oversight.
- What type of endpoints will need to be supported, and are you already standardised on a cloud productivity vendor like Microsoft or Google? If your organisation uses Microsoft products on all endpoints and servers, then you can likely choose from any of the products that match your other needs or even consider Microsoft Defender for the tightest possible EDR/OS integration. While even Microsoft’s Defender (and InTune MDM) can support macOS, Linux, Android, and iOS, if these endpoints make up a large portion of your endpoint population, you may want to consider solutions known to have good support for what you have.
- Does your organisation have in-house security tools or other IT applications that need to be integrated with the EDR solution? If so, are these applications cloud hosted with out-of-the-box integrations? If so, then it is important to look at the APIs and integrations offered by each EDR solution in order to determine if the solution will work within your environment and how difficult or easy will it be to deploy and maintain. If not, you should consider the user interface including dashboards, visualisations, and search capabilities, as these features will be critically important if your EDR solution’s interface will be the primary place to view security information.
- Are you interested in additional endpoint security features, like being able to control DNS or isolate web browsing sessions? Most EDR solutions offered from different manufacturers will all have some sort of web security functionality, even if it is just basic static analysis of scripts running on the endpoint, but some solutions will include unique and targeted approaches to web security and privacy such as web browser control, auto-configuring VPN so web traffic is sent through the organisation’s proxy for inspection, or even integration with email and collaboration tools to detect risky behaviour. In Microsoft environments, Microsoft Defender offers all of this and more. Otherwise, solutions like Sentinel One Singularity or Carbon Black offer great features for more granular control of enpdpoint security configuration.
- When looking at potential security solutions, where do you place more value – innovation or longevity? Some manufacturers will offer bleeding-edge technology to their customers in an effort to provide automated protection against theats that we don’t yet know about which other signature/definition-based solutions wouldn’t be able to find (like SentinelOne, for example). Other manufacturers like McAfee or Symantec may offer the most trusted and proven solutions to known problems and will wait to offer their customers new technologies until they have been proven and gained some trust in the industry.
- Do we need an EDR solution with flexibility for in-house security professionals to perform their own detection engineering, run their own playbooks for responses, deploy their own remediation scripts, or conduct in-depth threat hunting without pivoting to a SIEM? If your organisation is looking for something that can be fully customised and is designed for use by security professionals on a regular basis, avoid solutions that target small businesses or consumers (for example, Malwarebytes, ESET, or Sophos) where their customers don’t need or want the ability to fully manage their deployments, and where they need 100% automated remediation. On the other hand, if you are an organisation with limited or no security staff, consider looking for solutions that offer more automation and are known to mitigate ‘alert fatigue’.
- Does your organisation have requirements for investigation, analysis, and data collection surrounding potential or actual breaches? If so, consider a solution that can be hosted in your environment where you can provide the necessary storage while keeping the data fully under your control.
1. SentinelOne (Singularity)
SentinelOne’s Singularity offers multiple product tiers with Singularity Complete being the all-inclusive tier. Their EDR offering includes top-of-the-line threat hunting capabilities and allows for manual or automated “Active” responses including host isolation. Their storyline feature offers instant visibility into each threat’s life cycle along the kill chain without needing to piece things together using logged events. SentinelOne offers MDR services (called Vigilance), and they also offer an entry-level solution called Singularity Core which they market to organisations of all sizes as a legacy antivirus replacement.
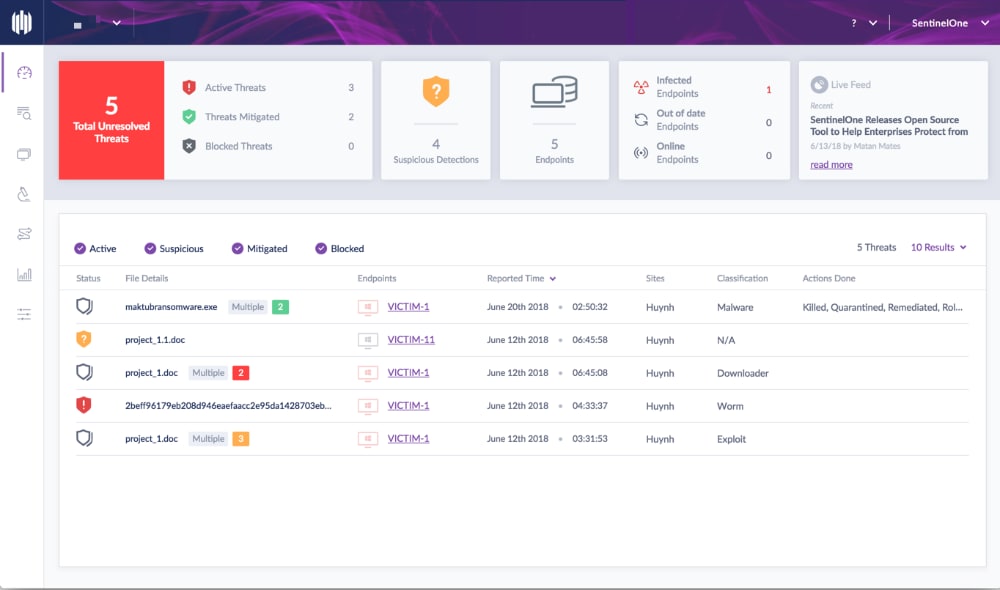
- Singularity EDR Dashboard
MITRE ATT&CK® Evaluations 2021 Visibility: 174/174
SentinelOne Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | SentinelOne Pros | SentinelOne Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 02:13 PM | hyelland | 30/10/2024 02:13 PM | Good for threat hunting | Integrations are still maturing |
| 2 | hyelland | 30/10/2024 02:13 PM | hyelland | 30/10/2024 02:13 PM | Fully-managed MDR available | Reviews indicate occasional bugginess in the UI |
| 3 | hyelland | 30/10/2024 02:13 PM | hyelland | 30/10/2024 02:13 PM | Storyline feature | Can be resource intensive |
| SentinelOne Pros | SentinelOne Cons |
2. CrowdStrike (Falcon)
CrowdStrike Falcon is an industry-leading EDR solution designed to make an organization’s analysts and investigating teams more efficient. They boast a “quick search” feature that returns results from logs, telemetry, threat hunting data and open investigations in less than five seconds. The prioritization and categorization of alerts into incidents keeps end-users from being overwhelmed with alerts that need their attention. Their Insights product also allows for the mapping of alerts to the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™) framework which is very helpful for red/blue/purple team operations. CrowdStrike also offers fully managed services with included threat hunting time focused on catching the most sophisticated Advanced Persistent Threats (APTs).
Their solution is tailored to provide everything an organization would need to identify and stop any threat on endpoints, their network, or in their data. Through recent acquisitions, they are beginning to roll out additional solutions beyond endpoint security including identity protection solutions and Security Orchestration, Automation, and Response (SOAR) solutions which tightly integrate with Falcon.
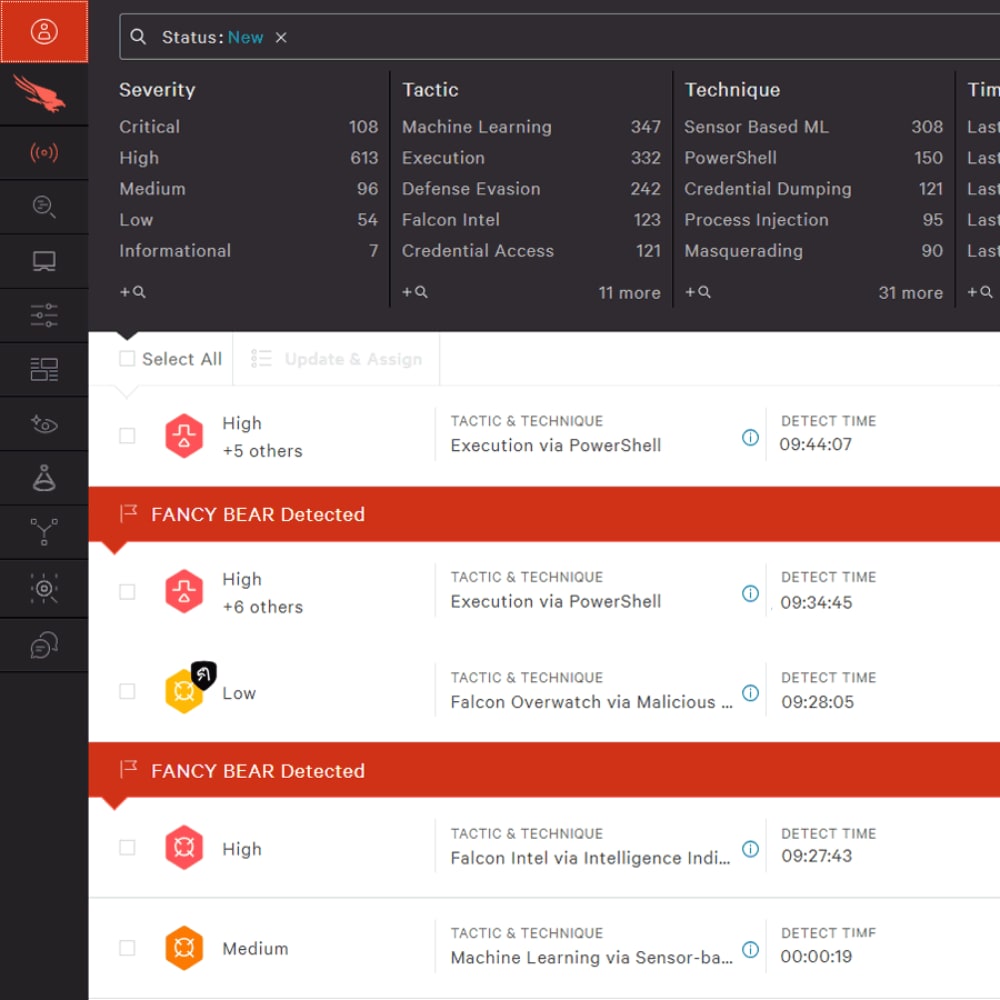
- CrowdStrike Falcon Dashboard
MITRE ATT&CK® Evaluations 2021 Visibility: 152/174
CrowdStrike Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | CrowdStrike Pros | CrowdStrike Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 11:43 AM | hyelland | 30/10/2024 11:43 AM | Good for threat hunting | Product portfolio was once simple, but now it’s so big it’s intimidating |
| 2 | hyelland | 30/10/2024 11:43 AM | hyelland | 30/10/2024 11:43 AM | Fast searches | MDR is expensive |
| 3 | hyelland | 30/10/2024 11:43 AM | hyelland | 30/10/2024 11:43 AM | MDR available | Learning curve |
| CrowdStrike Pros | CrowdStrike Cons |
3. Trend Micro (XDR)
Trend Micro’s solution is marketed as a solution that unifies endpoint defence for past, present, and future cyber threats. Like many other vendors in this market, their EDR solution is a part of a larger portfolio of security products. Trend Micro’s EDR solution is designed to be combined with the rest of their Apex One solutions to bring MDR, EDR, email, web and SaaS application security into a single solution. This product aims to provide a single interface for full root cause analysis to give the deepest insight into any detection including “patient zero” identification. Threat hunting and search capabilities are solid, and their Advanced Indicators of Attack (IOA) and Indicators Of Compromise (IOC) search functionality give analysts and investigating teams an edge with both forensics and proactive defences from advanced threats.

- Trend Micro XDR
MITRE ATT&CK® Evaluations 2021 Visibility: 167/174
TrendMicro Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | TrendMicro Pros | TrendMicro Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 02:19 PM | hyelland | 30/10/2024 02:19 PM | Seamless integration across Trend Micro’s portfolio | Can be resource intensive |
| 2 | hyelland | 30/10/2024 02:19 PM | hyelland | 30/10/2024 02:19 PM | IOA/IOC search | Many features are cloud-only |
| 3 | hyelland | 30/10/2024 02:19 PM | hyelland | 30/10/2024 02:19 PM | Root cause analysis is made simple | Learning curve |
| TrendMicro Pros | TrendMicro Cons |
4. Microsoft (Defender for Endpoint)
Microsoft Defender for Endpoint (MDE) is a central component of the Microsoft 365 Defender suite which includes Microsoft Defender for Office 365, Microsoft Defender for Endpoint, Microsoft Cloud Application Security and Microsoft Defender for Identity. Their solution touts no agents or scans but instead uses sensors built-in to the operating system that detects vulnerabilities and misconfigurations, then prioritizes vulnerabilities based on many contextual factors including analytics available in their business and productivity tools. Defender for Endpoint is no doubt one of the most comprehensive endpoint security solutions with features for threat hunting, vulnerability management, attack surface reduction, cloud-security, augmented proactive antivirus, automated investigation and remediation and an MDR offering that puts Microsoft Threat Hunters at your service. This solution is especially ideal for an organization that uses Microsoft products throughout the rest of the business and wants to implement world class protection for endpoints, given that their product works seamlessly with all the other Microsoft 365 products and services. That said – Apple and Linux endpoints are supported, as well as Android and iOS mobile endpoints that are managed by Intune, Microsoft’s Mobile Device Management (MDM) solution.
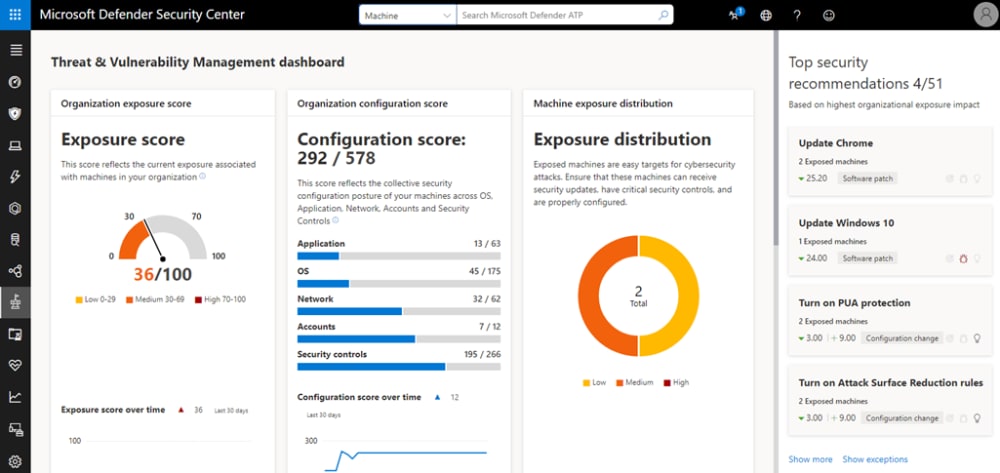
- Microsoft Defender Endpoint Dashboard
MITRE ATT&CK® Evaluations 2021 Visibility: 151/174
Microsoft Defender Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Microsoft Pros | Microsoft Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 12:11 PM | hyelland | 30/10/2024 12:11 PM | Agentless | Some features are Windows-only |
| 2 | hyelland | 30/10/2024 12:11 PM | hyelland | 30/10/2024 12:11 PM | Automated investigations | UI could be improved |
| 3 | hyelland | 30/10/2024 12:11 PM | hyelland | 30/10/2024 12:11 PM | Good threat hunting capabilities | Can’t deploy on-premise |
| Microsoft Pros | Microsoft Cons |
5. VMware (Carbon Black EDR/Cloud)
VMware Carbon Black is targeted at organizations that need an entirely on-premises and self-managed solution for endpoint security without sacrificing capability. It includes features such as threat hunting and incident response designed for online or offline SOCs. Incident responders can quickly access continuously recorded endpoint data from a central location, and they’re able to pull or push files, kill processes and perform memory dumps remotely from an intuitive user interface. There is also a Carbon Black Cloud solution that enables organizations of any size to modernize their endpoint protection with sophisticated cloud-native detection, threat intelligence, automation and a plethora of integrations to most security stacks.
Carbon Black also offers various advanced prevention methods for potential ransomware attacks, claiming to be able to detect and stop future threats based on behavioral analysis and sandboxing techniques. This is both a legacy AV replacement and full-featured EDR solution which is known for reliable detection and solid incident response functionality when it counts.
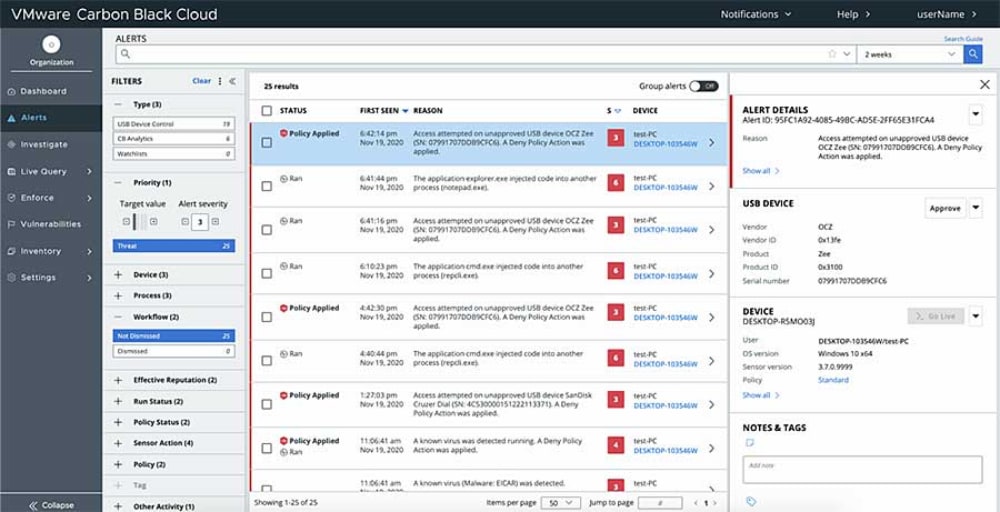
- VMware Carbon Black Cloud EDR Dashboard
MITRE ATT&CK® Evaluations 2021 Visibility: 154/174
VMware Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | VMware Pros | VMware Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 02:20 PM | hyelland | 30/10/2024 02:20 PM | Good threat hunting capabilities | Expensive |
| 2 | hyelland | 30/10/2024 02:20 PM | hyelland | 30/10/2024 02:20 PM | Similar features whether cloud or on-premise | Can be resource intensive |
| 3 | hyelland | 30/10/2024 02:20 PM | hyelland | 30/10/2024 02:20 PM | Tons of integrations | Agent doesn’t play nice with other security tools |
| VMware Pros | VMware Cons |
6. Symantec (Broadcom) Advanced Threat Protection Endpoint
Symantec Advanced Threat Protection (ATP) is a flexible solution that provides combines attack indicators from endpoint, network and e-mail sensors to deliver robust endpoint protection. Customers who use other Symantec products will benefit the most from their EDR offering as it integrates to the industry giant’s suite of security solutions to enable automate response as well as content analysis which provides another layer of protection from APTs and targeted attacks. The solution can be deployed onsite, virtually or in a cloud-hosted environment. This solution is well-suited for organizations looking to take their security to the next level with a single-vendor portfolio of products including secure messaging, analytics, reporting, secure web gateways, and MDR services.
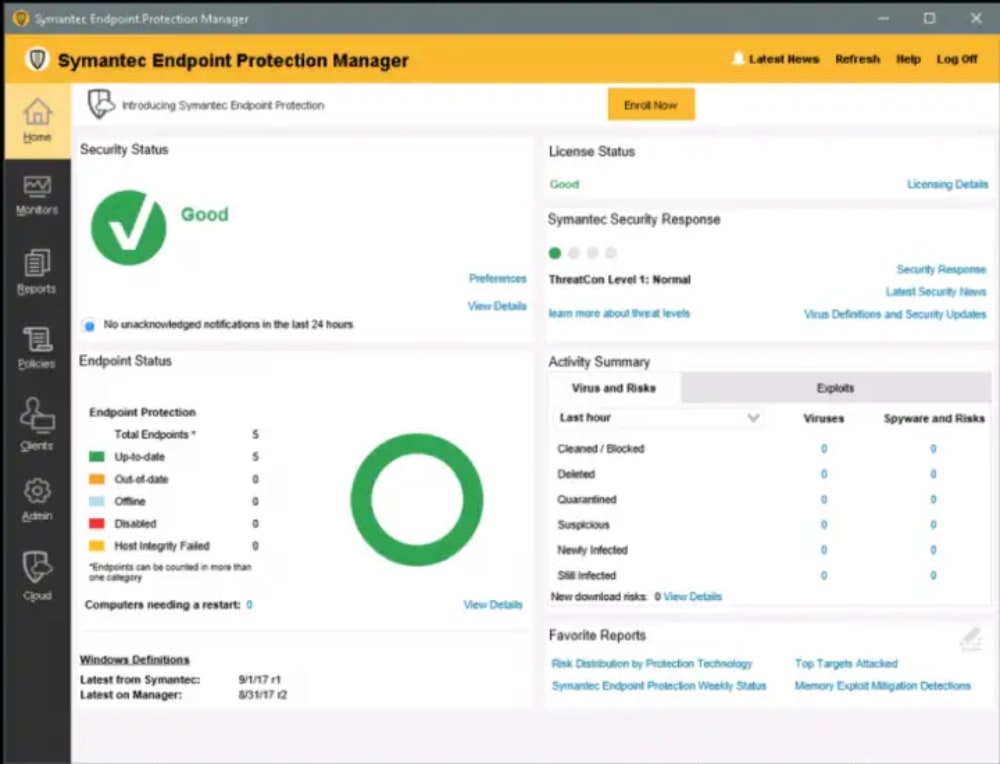
- Symantec Advanced Threat Protection EDR Dashboard
MITRE ATT&CK Evaluations 2021 Visibility: 159/174
Symantec Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Symantec (Broadcom) Pros | Symantec (Broadcom) Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 02:16 PM | hyelland | 30/10/2024 02:16 PM | Seamless integration with other Symantec security products | Licensing and purchasing has become a bit confusing since Broadcom acquisition |
| 2 | hyelland | 30/10/2024 02:16 PM | hyelland | 30/10/2024 02:16 PM | MDR available | Many features aren’t available on-premise |
| 3 | hyelland | 30/10/2024 02:16 PM | hyelland | 30/10/2024 02:16 PM | Automated correlations between endpoints and other sensors | Learning curve |
| Symantec (Broadcom) Pros | Symantec (Broadcom) Cons |
7. Malwarebytes (Endpoint Detection and Response)
Malwarebytes Endpoint Detection and Response for Business is geared toward organizations looking for a simple but effective endpoint security solution that can stand alone or augment an existing solution. Their unique machine learning algorithms are meant to detect zero-day attacks and isolate processes, networks and applications while countering threats such as malicious executables or file changes. Their ransomware protection offering provides 72 hour rollback for Windows workstations which they claim carries little to no performance cost, and a Indicators Of Compromise (IOCs) search functionality to make remediating attacks efficient.
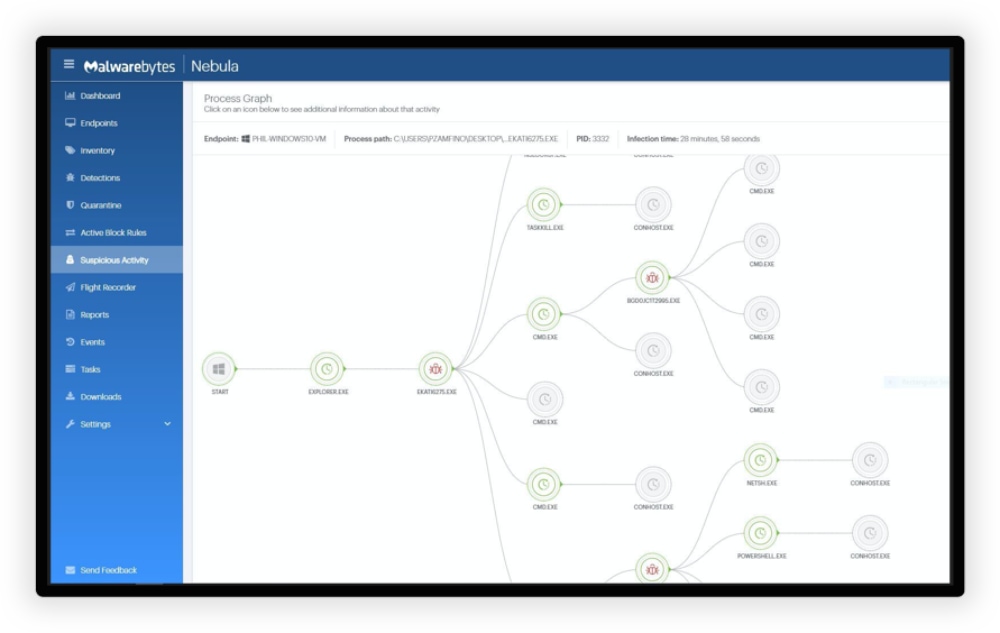
- Malwarebytes EDR Dashboard
MITRE ATT&CK® Evaluations 2021 Visibility: 116/162 (No Linux agent)
Malwarebytes Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Malwarebytes Pros | Malwarebytes Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 12:07 PM | hyelland | 30/10/2024 12:07 PM | Simple | Limited threat hunting capability |
| 2 | hyelland | 30/10/2024 12:07 PM | hyelland | 30/10/2024 12:07 PM | Ransomware roll-back | No Linux agent |
| 3 | hyelland | 30/10/2024 12:07 PM | hyelland | 30/10/2024 12:07 PM | IOC search | Expensive compared to others with more functionality |
| Malwarebytes Pros | Malwarebytes Cons |
8. Panda (Adaptive Defence 360)
Panda Adaptive Defense 360 is a well-rounded EDR solution that claims to enable 100% detection and classification of processes across all endpoints. While Panda also offers traditional antivirus solutions, Panda Adaptive Defense 360 is designed to provide complete visibility into threats that bypass traditional security measures like antivirus, and can be installed alongside them. Alerts are mapped to MITRE ATT&CK™ Framework and monitored continuously with cloud-based machine learning algorithms that detect IOCs and even Living off the Land attacks (LotL). Response features include containment and remediation capabilities that can block applications identified by multiple methods including hash or name. Adaptive Defense 360 is a robust solution that covers a lot of attack surface as their Aether interface combines several security technologies into a unified EDR platform.
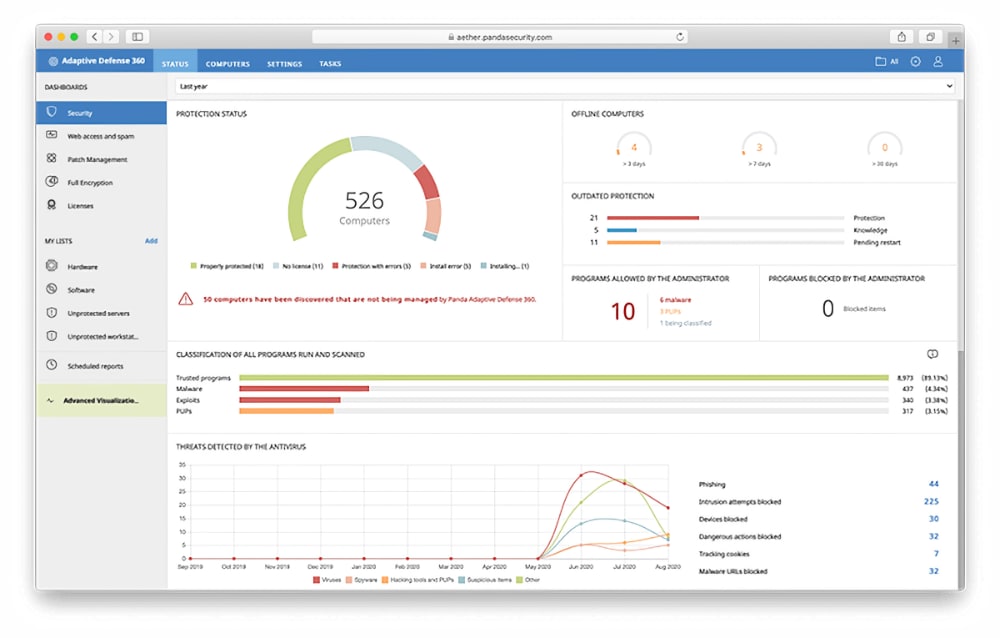
- Panda Adaptive Defence 360 Dashboard
Image Source: WatchGuard Technologies, (2022)
MITRE ATT&CK® Evaluations 2021 Visibility: Did not participate
Panda Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Panda Pros | Panda Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 02:12 PM | hyelland | 30/10/2024 02:12 PM | 100% classification of processes | UI doesn’t surface all available event data – some is only available upon request from support |
| 2 | hyelland | 30/10/2024 02:12 PM | hyelland | 30/10/2024 02:12 PM | Unmanaged endpoint detection | Mixed reviews on customer service |
| 3 | hyelland | 30/10/2024 02:12 PM | hyelland | 30/10/2024 02:12 PM | Agent plays nice with other security tools | Reviews indicate occasional bugginess in UI |
| Panda Pros | Panda Cons |
9. Check Point (Harmony)
Check Point’s EDR solution, Harmony Endpoint, is a complete endpoint protection solution touting the automation of 90% of attack detection, investigation and remediation by automatically containing and remediating the entire chain of events behind the attacks and providing complete recovery. After an incident occurs, they continue automating processes by automating forensic reports which are correlated to the MITRE ATT&CK™ Framework for contextual insights and recommendations for preventive security controls. With Harmony Endpoint’s ability to identify and drill-down into incidents from intuitive dashboards and offer automated remediation options, this solution provides advanced protection for organizations with or without their own SOCs. Harmony Endpoint is available as an on-premises or cloud solution for Windows, macOS and Linux environments. Their unified agent for EDR, VPN, NGAV, DLP and web protection makes this a very powerful endpoint security solution for organizations across verticals and ranging from SMB to Enterprise.
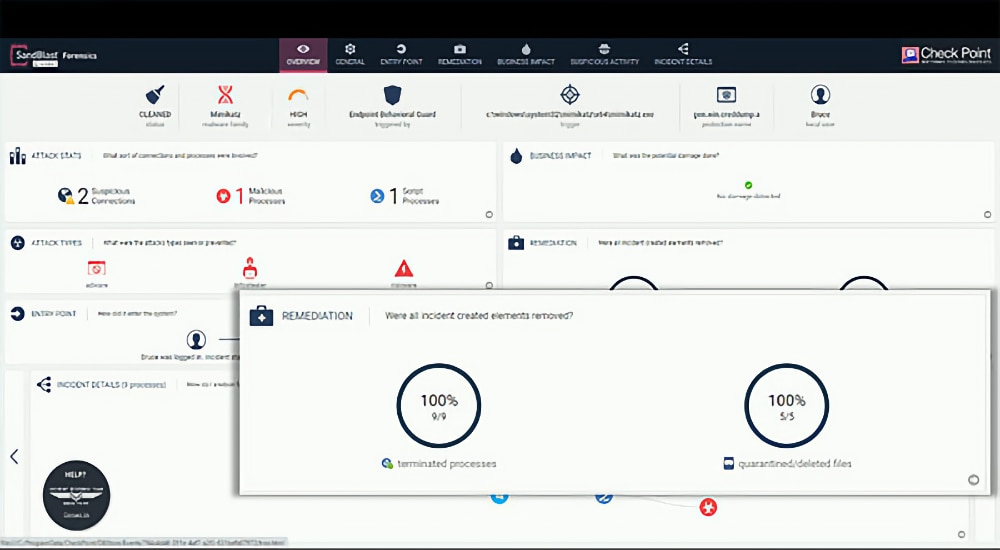
- Check Point Harmony EDR Dashboard
MITRE ATT&CK® Evaluations 2021 Visibility: 162/174
Checkpoint Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Check Point Pros | Check Point Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 11:39 AM | hyelland | 30/10/2024 11:39 AM | Lots of automation | Expensive |
| 2 | hyelland | 30/10/2024 11:39 AM | hyelland | 30/10/2024 11:39 AM | Intuitive UI | Learning curve |
| 3 | hyelland | 30/10/2024 11:39 AM | hyelland | 30/10/2024 11:39 AM | On-premise or cloud | Partner-channel only sales model |
| Check Point Pros | Check Point Cons |
10. Palo Alto Networks (Cortex EDR)
Cortex XDR is Palo Alto’s Extended Detection and Response (XDR) solution and is designed to augment the security team’s capabilities with bleeding-edge approaches to detection and response. The solution offers a single cloud-delivered agent that can stop Zero Day attacks with advanced Artificial Intelligence (AI) and Machine Learning (ML) models. Endpoint security features also include management of USB devices, host firewall configuration and disk encryption for Windows and macOS endpoints. Cortex XDR breaks security silos by integrating data and providing behavioural analytics across endpoint, network, cloud and identity data sources for comprehensive threat detection. This approach minimises the time needed for hunting, investigation and remediation as everything is centralised in one place. Their dashboards are very intuitive and modern with complete command and control capability for endpoint security across an entire organization’s estate. As with other Palo Alto solutions, this product is built for larger organizations with many endpoints, although smaller organizations with limited human capabilities can also benefit from efficiencies gained by its powerful automation capabilities.
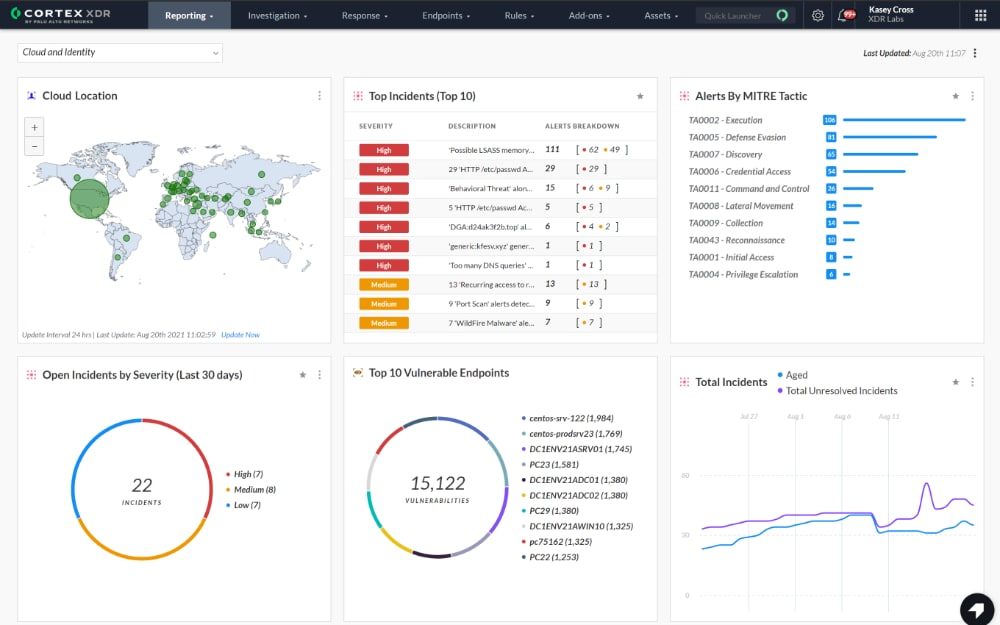
- Palo Alto Cortex EDR Dashboard
MITRE ATT&CK Evaluations 2021 Visibility: 169/174
Palo Alto Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Palo Alto Networks Pros | Palo Alto Networks Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 02:10 PM | hyelland | 30/10/2024 02:10 PM | Lightweight | Expensive |
| 2 | hyelland | 30/10/2024 02:10 PM | hyelland | 30/10/2024 02:10 PM | Good threat hunting capabilities | Learning Curve |
| 3 | hyelland | 30/10/2024 02:10 PM | hyelland | 30/10/2024 02:10 PM | Management of endpoint security controls (USB, encryption, etc.) | Lots of automation, but it takes work to implement |
| Palo Alto Networks Pros | Palo Alto Networks Cons |
11. Cybereason (XDR Platform)
Cybereason’s XDR solution is designed for organizations that need to take proactive defence and investigations to the next level with threat hunting. Although it’s primarily an endpoint security solution, it aims to protect assets across an organization’s entire IT stack, including user data, email and networks. The solution also includes behavioral analytics which correlate events across sensors to provide context. The interface makes it easy to visualize correlations between events and it is definitely designed for teams who spend a lot of time on threat hunting investigation, and remediation activities.
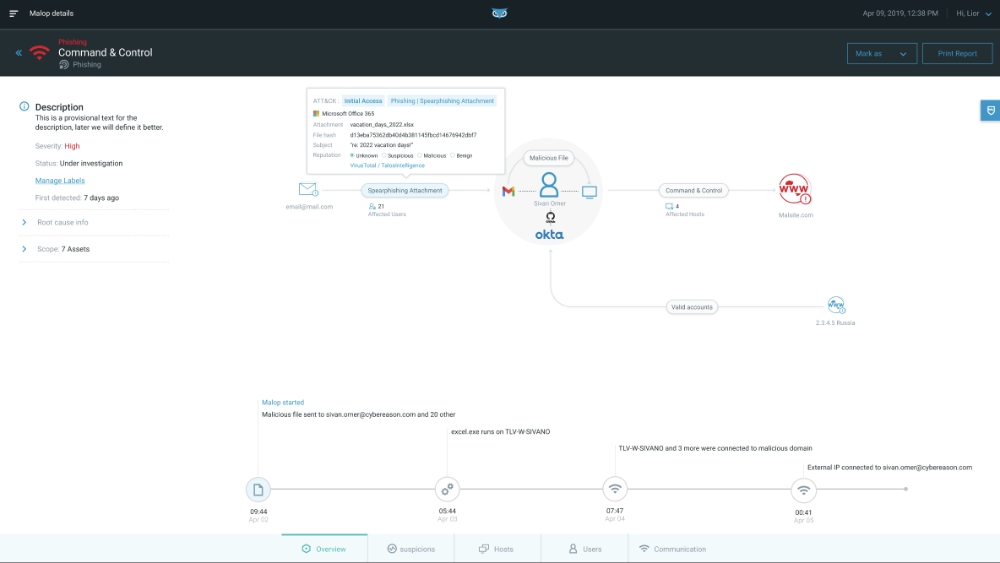
- Cybereason XDR Dashboard
MITRE ATT&CK® Evaluations 2021 Visibility: 169/174
Cybereason Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Cybereason Pros | Cybereason Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 11:55 AM | hyelland | 30/10/2024 11:55 AM | Behavioral analytics | Limited integrations |
| 2 | hyelland | 30/10/2024 11:55 AM | hyelland | 30/10/2024 11:55 AM | Automated correlation | Learning curve |
| 3 | hyelland | 30/10/2024 11:55 AM | hyelland | 30/10/2024 11:55 AM | Good threat hunting capabilities | Can be resource intensive |
| Cybereason Pros | Cybereason Cons |
12. Sophos (Intercept X Advanced with EDR)
Sophos’ Intercept X Advanced with EDR solutions provides exploit prevention and anti-ransomware features with detection of both known and unknown threats enabled by deep learning technology. Cloud-based endpoint protection provided by Intercept X Advanced with EDR allows the synchronization between Sophos firewalls and endpoint security to provide a defence that is strengthened by its ability to communicate real-time insight, intelligence and visibility into all applications on an organization’s network. This solution can be a fit for organizations of any size although it is often found in small-to-medium sized organizations and it offers support for a variety of endpoint types including desktops, laptops, servers, tablets and mobile devices.
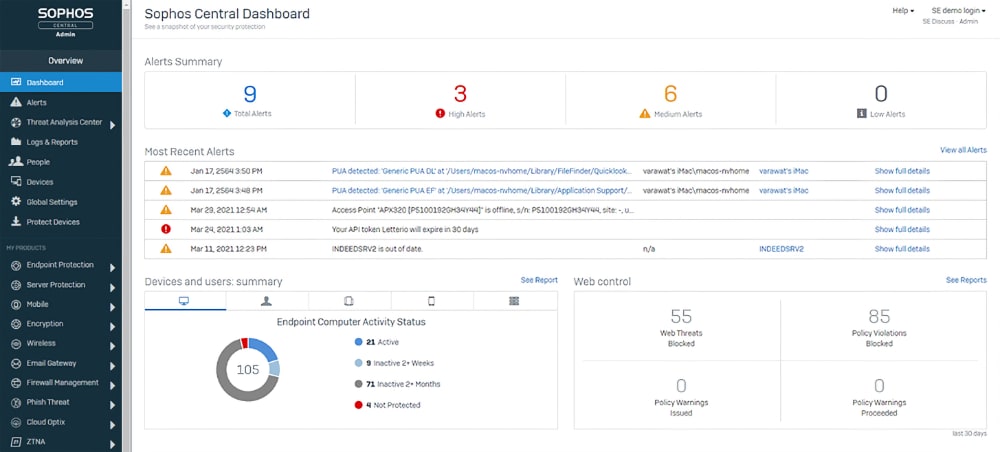
- Sophos EDR Dashboard
MITRE ATT&CK® Evaluations 2021 Visibility: 118/162 (No Linux agent)
Sophos Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Sophos Pros | Sophos Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 02:14 PM | hyelland | 30/10/2024 02:14 PM | Inexpensive | Limited integrations |
| 2 | hyelland | 30/10/2024 02:14 PM | hyelland | 30/10/2024 02:14 PM | Easy to use | Can be resource intensive |
| 3 | hyelland | 30/10/2024 02:14 PM | hyelland | 30/10/2024 02:14 PM | Good mobile protection | Most features are cloud-based |
| Sophos Pros | Sophos Cons |
13. Cisco (Secure Endpoint)
Cisco Secure Endpoint is a cloud-native endpoint detection and response solution that offers protection, detection and response while dramatically reducing time to remediation. This is achieved with integrated risk-based vulnerability management powered by Kenna Security. This solution is great for organizations that are looking for comprehensive coverage of their endpoints with a trusted product that integrates seamlessly into an existing Cisco environment. Cisco offers a fully-managed MDR service as well as co-managed or DIY deployment. Cisco’s SecureX platform comes built into the EDR solution and integrates seamlessly with their XDR solution to provide enhanced protection beyond the endpoints. Cisco Secure Endpoint can be leveraged for endpoint security by any organisation, although enterprises who are already Cisco users can realise massive security benefits considering seamless integrations across other Cisco security products including Duo, Umbrella and Meraki.
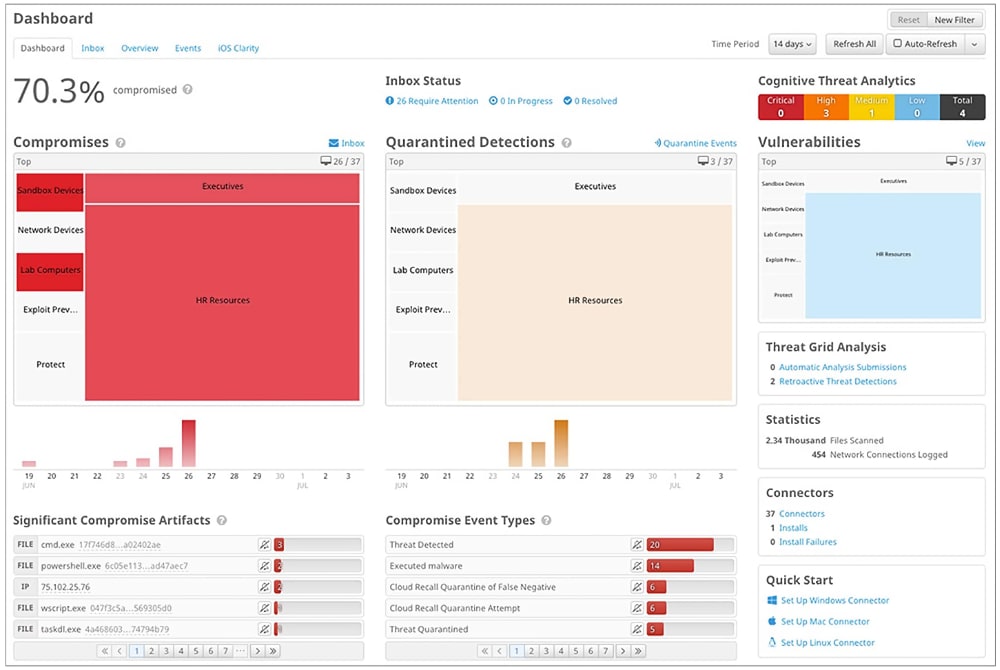
- Cisco Secure Endpoint Dashboard
MITRE ATT&CK® Evaluations 2021 Visibility: 122/174
Cisco Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Cisco Pros | Cisco Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 11:42 AM | hyelland | 30/10/2024 11:42 AM | Vulnerability prioritization (by Kenna Security) | Expensive |
| 2 | hyelland | 30/10/2024 11:42 AM | hyelland | 30/10/2024 11:42 AM | MDR available | Pricing and licensing model is complicated (it’s Cisco afterall) |
| 3 | hyelland | 30/10/2024 11:42 AM | hyelland | 30/10/2024 11:42 AM | Lots of integrations | Can be resource intensive |
| Cisco Pros | Cisco Cons |
14. Kaspersky Endpoint Detection and Response (KEDR)
The Kaspersky EDR solution is meant to be an enhancement to their award winning Endpoint Protection Platform (EPP). This is a single agent solution for automated protection against common and advanced threats alike. Their solution claims to collect full endpoint telemetry for analysis and further enhancement when combined with their Anti Targeted Attack Platform for advanced network-level threat discovery, investigation and remediation. A single user interface provides visibility into the threat and alerts with views for monitoring, incident response and investigation. The interface also includes features to assist with alert management and triage users who may not be experienced security analysts.

- Kaspersky EDR Dashboard
MITRE ATT&CK® Evaluations 2021 Visibility: Did not participate
Kaspersky Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Kaspersky Pros | Kaspersky Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 12:06 PM | hyelland | 30/10/2024 12:06 PM | Simple to use and deploy | Threat hunting features are limited |
| 2 | hyelland | 30/10/2024 12:06 PM | hyelland | 30/10/2024 12:06 PM | Good visualizations and dashboards | Limited integrations |
| 3 | hyelland | 30/10/2024 12:06 PM | hyelland | 30/10/2024 12:06 PM | Inexpensive compared to others | No on-premise option |
| Kaspersky Pros | Kaspersky Cons |
15. FireEye (Endpoint Security)
FireEye’s Endpoint Security solution is deployed using a single agent with a multi-engine approach. It uses a signature-based engine, a machine learning engine, and a behavioral analysis engine. The result is a lightweight but powerful endpoint security solution that can provide reliable real-time detection and deep forensic insights with its Indicator Of Compromise (IOC) engine. The endpoint security solution can be further extended by streaming events to FireEyeHelix XDR, the extended detection and response solution by FireEye. The company is known for introducing cutting edge technology and techniques developed by front line responders. This solution continuously monitors and identifies suspicious behavior and presents it to an organization’s security team for manual action, or it can isolate and deflect attacks automatically. Although the solution is usually integrated with FireEye Helix or another SIEM, the centralized management console can standalone to enable threat hunting, investigations with team collaboration, incident response and reporting.
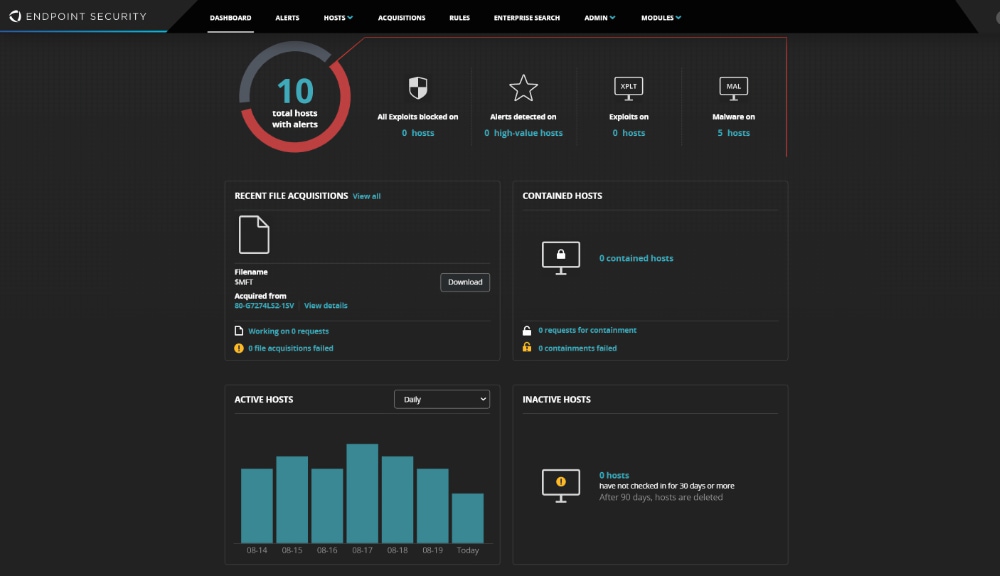
- FireEye Endpoint Security Dashboard
Image Source: Cybersecurity-excellence-awards, (2021)
MITRE ATT&CK® Evaluations 2021 Visibility: 136/174
FireEye Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | FireEye Pros | FireEye Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 11:59 AM | hyelland | 30/10/2024 11:59 AM | Lightweight | Expensive |
| 2 | hyelland | 30/10/2024 11:59 AM | hyelland | 30/10/2024 11:59 AM | Forensics enablement is second to none, thanks to FireEye / Mandiant collaboration | Learning curve |
| 3 | hyelland | 30/10/2024 11:59 AM | hyelland | 30/10/2024 11:59 AM | Great reporting and analytics | |
| FireEye Pros | FireEye Cons |
16. BlackBerry (Optics)
BlackBerry Optics provides millisecond threat detection and remediation with on-device security. The focus of BlackBerry’s solution is to speed the response time up in order to prevent minor incidents from turning into breaches. BlackBerry’s inclusion of Cylance AI uses next generation continuous machine learning for threat analysis and prevention. One of the key differentiators for BlackBerry’s solution is their online and offline capabilities. The IOC search capabilities through the lightweight InstaQuery (IQ) tool provided with this product makes an efficient solution for those organizations with an online or offline need for a data driven approach to threat detection, hunting, investigation and remediation. When milliseconds matter, BlackBerry is a solution to consider.
- BlackBerry Optics Dashboard
MITRE ATT&CK® Evaluations 2021 Visibility: 141/174
BlackBerry Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | BlackBerry Pros | BlackBerry Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 11:38 AM | hyelland | 30/10/2024 11:38 AM | Rapid detection | Expensive |
| 2 | hyelland | 30/10/2024 11:38 AM | hyelland | 30/10/2024 11:38 AM | Most features work regardless of cloud or on-premise | Channel partner only sales model |
| 3 | hyelland | 30/10/2024 11:38 AM | hyelland | 30/10/2024 11:38 AM | Good threat hunting capabilities | Learning curve, especially for on-premise deployment and maintenance |
| BlackBerry Pros | BlackBerry Cons |
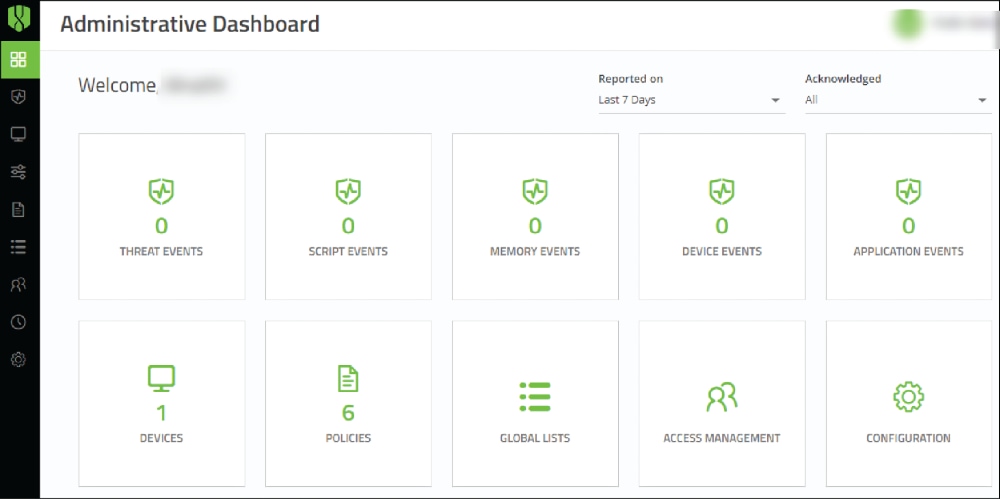
17. Cynet (360 Autonomous Breach Protection Platform)
Cynet’s solution aims to be the one stop shop for endpoint protection by providing a platform that natively integrates NGAV, EDR, network security, user behavior analysis and advanced threat detection. The advanced threat detection uses deception to detect and isolate advanced threats that generally bypass traditional endpoint security solutions. Their contextual view of endpoint, network and user data organizes alerts and data into incidents in a format that visualizes well, making it easier for security teams to quickly detect and respond to attacks. The solution provides automated responses which can enable immediate remediation when predefined alerts are triggered. Cynet also offers MDR services which provide 24×7 threat hunting, investigation and remediation from a dedicated SOC with experienced analysts.
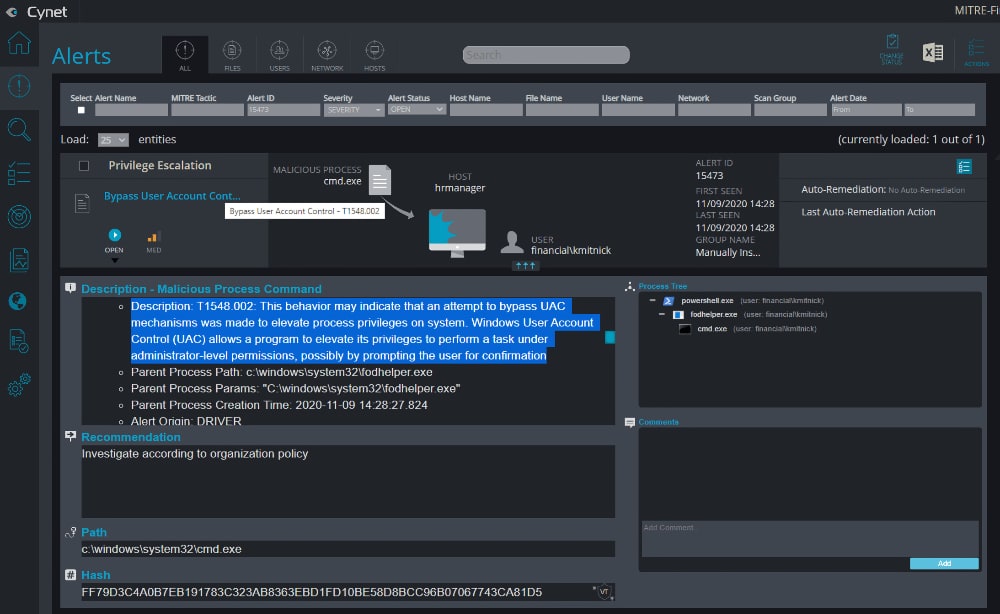
- Cynet 360 Dashboard
MITRE ATT&CK® Evaluations 2021 Visibility: 153/174
Cynet Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Cynet Pros | Cynet Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 11:56 AM | hyelland | 30/10/2024 11:56 AM | Intuitive UI | Can be resource intensive |
| 2 | hyelland | 30/10/2024 11:56 AM | hyelland | 30/10/2024 11:56 AM | MDR available | Limited integrations |
| 3 | hyelland | 30/10/2024 11:56 AM | hyelland | 30/10/2024 11:56 AM | Advanced threat detection using deception | Relatively new to the industry (less than 10 years in business) |
| Cynet Pros | Cynet Cons |
18. McAfee (Endpoint Threat Defence and Response)
McAfee’s EDR solution contains tools for real-time analysis using machine learning techniques to do both pre-execution analysis and dynamic behavioral analysis for sophisticated threat detection without relying on signatures.. It also dynamically contains application processes at the endpoint allowing users to still be productive while offering security tools and teams to perform in-depth investigations into potential threats. Even though McAfee is well-known as one of the leaders in the early days of antivirus, they’ve made a complete 180 degree turn by delivering an EDR solution with high detection rates for sophisticated attacks that doesn’t need signature-based detection.
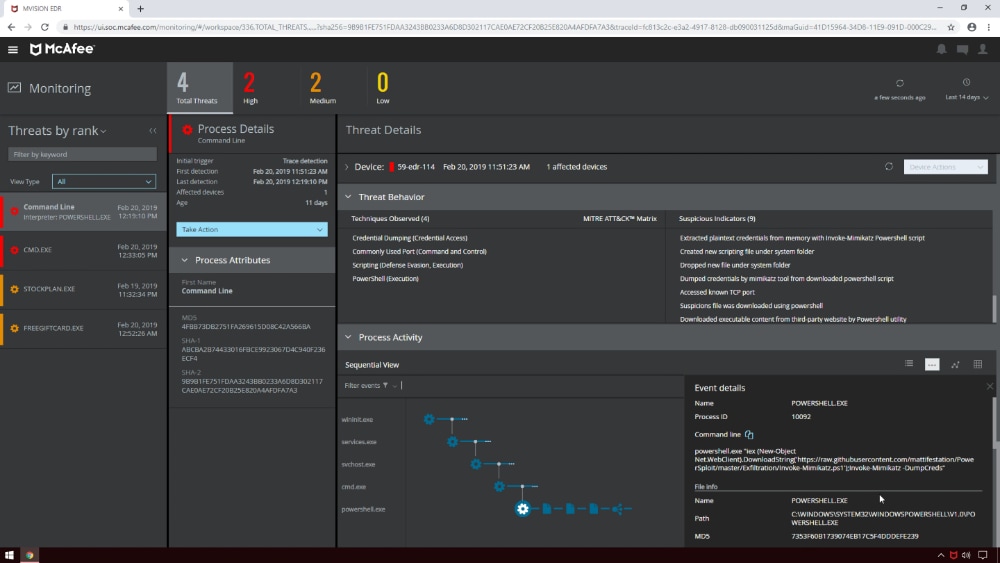
- McAfee EDR Dashboard
MITRE ATT&CK® Evaluations 2021 Visibility: 151/174
McAfee Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | McAfee Pros | McAfee Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 12:10 PM | hyelland | 30/10/2024 12:10 PM | Doesn’t rely on signature-based detection | Expensive |
| 2 | hyelland | 30/10/2024 12:10 PM | hyelland | 30/10/2024 12:10 PM | Good threat hunting capabilities | Learning curve |
| 3 | hyelland | 30/10/2024 12:10 PM | hyelland | 30/10/2024 12:10 PM | Lots of integrations | Can be resource intensive |
| McAfee Pros | McAfee Cons |
19. ESET (Enterprise Inspector)
ESET Enterprise Inspector is ESET’s EDR solution and it’s designed to be paired with ESET Endpoint Protection Platform to provide a complete prevention, detection and remediation solution for detecting APTs, stopping fileless attacks, stopping zero-day attacks and ransomware, as well as preventing organisational policy violations. They have an open architecture that promotes integration into other security products like SIEM, or IT issue trackers. ESET’s solution can be deployed as a do-it-yourself solution, but they also offer MDR services for those organizations without security teams. ESET is another solution that is most often found in small-to-midsize organizations.
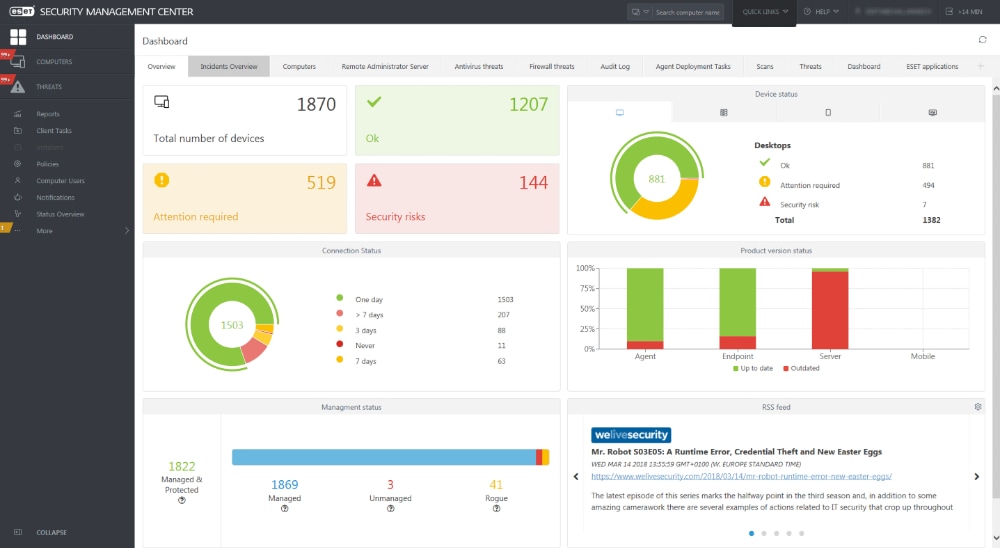
- ESET Dashboard
MITRE ATT&CK® Evaluations 2021 Visibility: 147/162 (No Linux agent)
ESET Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | ESET Pros | ESET Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 11:58 AM | hyelland | 30/10/2024 11:58 AM | Simple UI for policy enforcement | Open architecture allows for DIY integrations, but not a lot of integrations available out-of-the-box |
| 2 | hyelland | 30/10/2024 11:58 AM | hyelland | 30/10/2024 11:58 AM | MDR available | Limited threat hunting capabilities |
| 3 | hyelland | 30/10/2024 11:58 AM | hyelland | 30/10/2024 11:58 AM | Easy to use | No Linux agent |
| ESET Pros | ESET Cons |
20. WatchGuard (Cytomic Platform)
The Cytomic Platform is WatchGuard’s EDR solution. The solution can be self-managed or fully-managed with options for MDR. The Cytomic Platform uses a single agent to proactively stop attacks, malware and exploits with behavioral analysis at the endpoint. Additionally, their Zero-Trust Application Service allows organizations to leverage the EDR agent for implementing application whitelisting. Their API first architecture allows them to easily integrate into the rest of the security stack and for automated response capabilities. Finally, while their user interface may be a bit bland for experienced SOC analysts or seasoned threat hunters, its simplicity lends itself to less-experienced users who may not perform security duties as a full-time job.
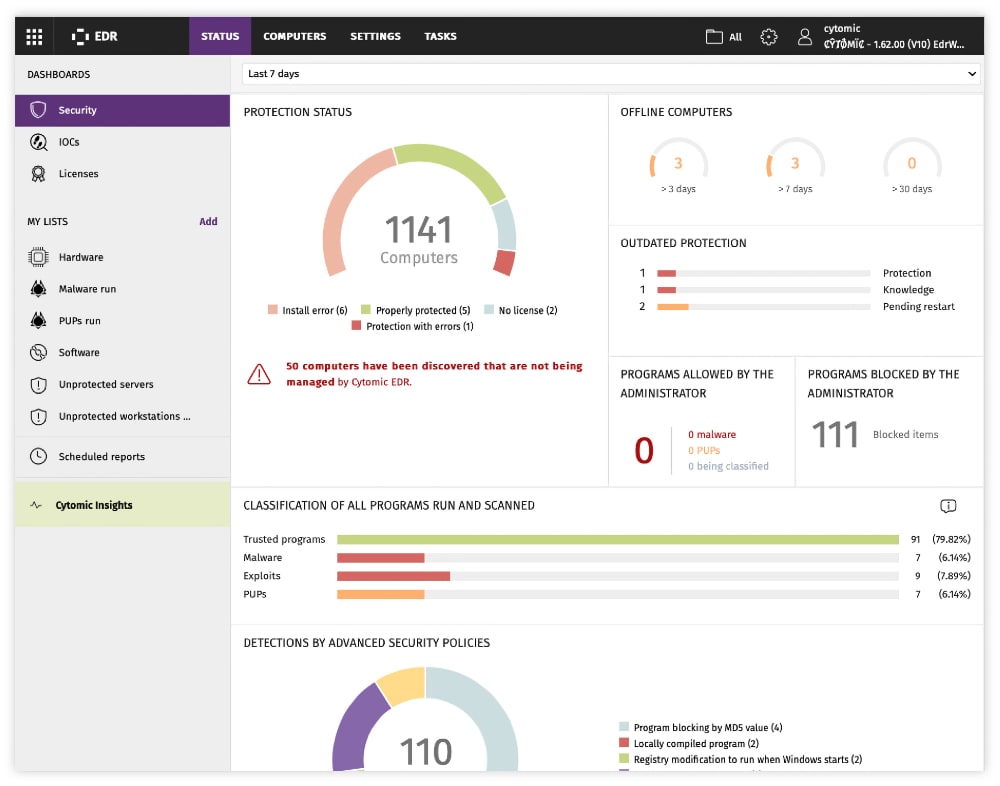
- Cytomic EDR Dashboard
MITRE ATT&CK Evaluations 2021 Visibility: Did not participate
WatchGuard Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | WatchGuard Pros | WatchGuard Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 02:20 PM | hyelland | 30/10/2024 02:20 PM | Simple UI | Limited integrations |
| 2 | hyelland | 30/10/2024 02:20 PM | hyelland | 30/10/2024 02:20 PM | Zero Trust Application Service (app whitelisting) | Limited threat hunting capabilities |
| 3 | hyelland | 30/10/2024 02:20 PM | hyelland | 30/10/2024 02:20 PM | MDR available | Can be resource intensive |
| WatchGuard Pros | WatchGuard Cons |
Conclusion
The importance of EDR in the current IT landscape is becoming more obvious with further increases of ransomware attacks and Advanced Persistent Threats. Detecting modern threats isn’t as simple as matching malware signatures anymore. These advanced threats gain access through user error, misconfigurations and advanced infiltration techniques such as chained zero-day attacks. In order to detect and try to prevent never-before-seen attacks, modern endpoint security tools are a necessity for any organisation.
EDR Vendor Comparison Matrix
EDR Vendor Comparison Matrix
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | EDR Vendor | Standard EDR Features | Unique EDR Features | Specific Needs/Use Cases it Fits and Why |
|---|---|---|---|---|---|---|---|---|
| 1 | hyelland | 30/10/2024 11:57 AM | hyelland | 30/10/2024 11:57 AM | SentinelOne – Singularity | Extended data retention, SentinelOne Cloud and Binary Vault store executables for future analysis, SentinelOne Cloud Funnel enables secure and near-real-time streaming of EDR telemetry from SentinelOne, Deep Visibility to your data lake via a Kafka subscr | SentinelOne Storyline Active Response (STAR) actions are assigned a TrueContextID and built into “stories” and managed, on the device without cloud connectivity and sent to analysts with easy to digest “storylines”, Deep Visibility (SentinelOne’s data col | With this solution an organization can leverage proven AI to mitigate new and emerging zero-day threats and provide high confidence data and telemetry to existing solutions (SIEM) all with an intuitive interface that makes deployment and rollout easy acro |
| 2 | hyelland | 30/10/2024 11:57 AM | hyelland | 30/10/2024 11:57 AM | CrowdStrike – Falcon Insight | Automated event prioritization, Real-time forensics and comprehensive visualizations, Alignment to MITRE ATT&CK framework, AI & behavioral analytics and human threat hunters combine to stop the most advanced threats as they appear, APIs, blocks or alerts | The CrowdStrike Security Cloud uses Threat Graph to find potential threats based on trillions of security events per day, Zero Trust Assessment (ZTA) provides real-time assessment and visualization of endpoint security health, Provides a unified cloud-bas | CrowdStrike’s Falcon Insight EDR product can provide the basis for a much larger and comprehensive security solution for organizations with maturing security operations that are looking to level up their security posture. It is also a good platform for SO |
| 3 | hyelland | 30/10/2024 11:57 AM | hyelland | 30/10/2024 11:57 AM | Trend Micro – Vision One EDR | Machine learning (ML), behavioral analysis, Application control, NGAM (Next-gen anti-malware), Endpoint encryption, Mobile security, Email and collaboration security, Gateway security, Windows, macOS, Cloud, On-premises, Hybrid. | Pre-execution and run-time machine learning protection, XGen security offers layered and multi method analysis of real-time data to reduce false positives and prevent all malicious activity, Single agent, Ransomware rollback capabilities, can be used with | TrendMicro offers a comprehensive solution that encompasses all data and communications on an endpoint so it is good for those with the strictest policies for their use cases. This solution will be great for organizations looking to get the most data and |
| 4 | hyelland | 30/10/2024 11:57 AM | hyelland | 30/10/2024 11:57 AM | Microsoft – Defender for Endpoint | Windows, macOS, Linux, Android, iOS, Agentless, Cloud based, Automation, Centralized configuration and management, APIs, Integrations, Automated investigation and remediation, (NGAV) Next-gen anti-virus, Machine learning (ML). | Widest threat optics available (especially for Windows OS), Stops fileless and file-based zero-day threats with AMSI (Antimalware Scan Interface) integration, Memory scanning, Built by the OS manufacturer this product gains deeper insights on Windows mach | Microsoft Defender for Endpoint is great for organisations that are standardised on a Microsoft tech stack as they will benefit the most from the deepest available integration between EDR and the Windows OS, Defender for Endpoint provides the most granula |
| 5 | hyelland | 30/10/2024 11:57 AM | hyelland | 30/10/2024 11:57 AM | VMware – Carbon Black | Attack chain visualization, APIs,Iintegrations, Continuous endpoint visibility, MSSP, On-premise, Cloud, SaaS solution availability, Customisable behavioural analysis and detection, Live response, Windows, Linux, macOS, host isolations, hash banning, exec | Live response, Secure remote access to remediate and investigate detections, Unlimited retention and scale, Automated watchlists for query analysis, Ransomware mitigation through behavioral detection and “traps”, File-less attack mitigation, This solution | Large organizations who require centralized recording of endpoint data within their own environment should consider Carbon Black. Its constant recordings of telemetry from endpoints gives Carbon Black the ability to conduct deep investigations during or |
| 6 | hyelland | 30/10/2024 11:57 AM | hyelland | 30/10/2024 11:57 AM | Broadcom (Symantec) Endpoint Security | Endpoint isolation,Remote secure shell for live remediation, Incident prioritization, Continuous recording, Threat hunter with machine learning (ML) and human analysis, behavioral analysis, integrations, APIs, Application control, Alignment and augmentati | Antimalware Scan Interface (AMSI), Full system dump capability, Process dump capability, Largest civilian intelligence network, Active Directory security by obfuscation, AI-assisted policy management and guidance, Automated sandboxing, Lures and baits, Se | The Symantec (Broadcom) solution is a great option for those that need an intuitive and familiar solution that checks all the boxes (especially if they’ve used Symantec Endpoint Protection in the past). This solution is suitable for organizations of all s |
| 7 | hyelland | 30/10/2024 11:57 AM | hyelland | 30/10/2024 11:57 AM | Malwarebytes EDR | Windows, macOS, integrations, SSO with SAML 2.0, RBAC, Automated reports, Cloud-based, Continuous monitoring, Integrated cloud sandbox, Machine learning (ML) for behavioral analysis. | Ransomware Rollback, Flight Recorder Search, Detects fingerprinting attempts, Web protection, Real time file-less attack detection, Forensics tool for Windows, Automated discovery and agent deployment. | This solution is suitable for organizations on a budget with an immediate need for solid next-generation antivirus (NGAV) coupled with bare-bones EDR features that is easy to install and manage. Not suitable for environments with full-time SOCs where th |
| 8 | hyelland | 30/10/2024 11:57 AM | hyelland | 30/10/2024 11:57 AM | Panda Adaptive Defense | Sandboxing, Continuous recording, Threat hunting, Aligned and mapped with MITRE ATT&CK Framework, Cloud-based machine learning, Attack chain visualization, Windows, macOS, Linux. | Automatically detect and respond to targeted attacks and in-memory exploits, Prevent unknown processes from executing, Pre-execution analysis, Running and post-execution analysis, Zero-Trust Application Service, Zero-Trust with 100% classification through | Panda’s Adaptive Defense 360 solution is great for organizations that have an immediate need to centrally-manage or augment legacy anti-virus solutions, as it can install directly on top of existing AV solutions. It can also help with asset management by |
| 9 | hyelland | 30/10/2024 11:57 AM | hyelland | 30/10/2024 11:57 AM | Check Point – Harmony Endpoint | Remediation recommendations, Maps to MITRE ATT&CK framework, Malware and file-less attack protection with Endpoint Behavioral Guard, Ransomware detection and rollback, Threat cloud provides aggregated threat intelligence, Threat hunting, Attack chain visu | MITRE based Machine Learning Sandboxing, Threat emulation and extraction, Credential theft prevention in real-time, Zero-Phishing technology blocks malicious websites, Leverages more than 60 threat prevention engines to prevent attacks, Automated report | CheckPoint’s solution fits into their comprehensive security portfolio so it’s a great fit for organizations that already have CheckPoint in their security stack. Harmony Endpoint provides sophisticated threat prevention and detection by supporting their |
| 10 | hyelland | 30/10/2024 11:57 AM | hyelland | 30/10/2024 11:57 AM | Palo Alto Networks – Cortex XDR | AI based behavioral analysis, Cloud-based analysis, Technique-based protection from threats, (NGAV) Next-gen anti-virus, Host firewall, Deep forensics even if endpoints are not connected to the network, Maps to MITRE ATT&CK framework, Attack chaining. | Pre-execution analysis, Cloud-execution analysis, Post-execution analysis, Fingerprinting prevention and detection, Kernel protection, USB device control, Disk encryption, Single-agent solution. | Palo Alto’s Cortex evolved from their Traps endpoint security solution, making it the first (or one of the first) XDR (Extended Detection and Response) solutions in the industry. Cortex is highly configurable, built for automation, and provides enhanced |
| EDR Vendor | Standard EDR Features | Unique EDR Features | Specific Needs/Use Cases it Fits and Why |