| Security Service Edge (SSE) architecture combines security tools to protect users, applications, and data across any location, making it essential for hybrid and remote workforces, as well as mobile infrastructures.” |
As new technologies and services are developed, the way that we secure our increasing digital infrastructure mustn’t be overlooked. With hybrid and flexible work becoming the norm, a dependency on applications and data being accessed from anywhere is vital and legacy security solutions are simply not enough.
Secure Service Edge (SSE) Features
Table of Contents
This is where SSE (Secure Service Edge) comes in. As quoted by Gartner, SSE is “a collection of integrated, cloud-centric security capabilities that facilitates safe access to websites, Software-as-a-Service (SaaS) applications and private applications.”
At its core, SSE combines security tools seamlessly together. Features include:
- Secure Web Gateways (SWG)
- Cloud Access Security Brokers (CASB)
- Zero Trust Network Access (ZTNA)
- Firewall as a Service (FWaaS)
SSE ensures the right security policy is applied to users regardless of location.
WAN Edge Services
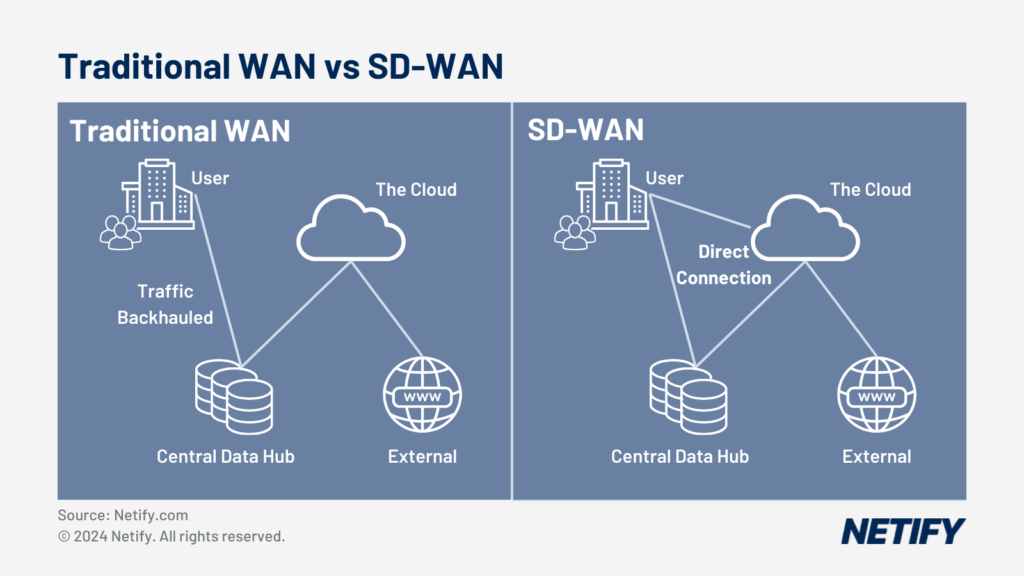
Wide Area Networks (WAN) are an essential business component for many organisations who have dispersed locations which need connecting.
The complex connections need protection, especially when crossing the boundary of their internal network to public clouds. This is where WAN Edge Services such as SD-WAN, QoS and SaaS acceleration come into play. SSE solutions integrate with these edge tools to act as the first line of defence, sitting right where the private infrastructure meets the wider internet.
- Traditional WAN vs SD-WAN
Security Service Edge for Hybrid Workforce
The transition towards a hybrid workforce necessitates an adaptive and responsive approach to cybersecurity. SSE rises to this challenge by delivering a single system for security regardless of location or device used. So whether a worker access data from the office or their home, SSE enforces the same level of protection and provides a consistent experience for all.
Selecting an SSE Vendor
When deciding which SSE vendor to utilise, you must identify your requirements as many options exist. You should evaluate your network infrastructure, understanding the importance of redundancy and distributed fabrics. It is suggested to map your current setup and consider future growth possibilities. Luckily, many vendors offer support and onboarding teams to make the migration as painless as possible.

- SD-WAN Technical Evaluation Criteria
Assessing Network Infrastructure
Identifying your local and web connectivity acts as a good starting point. Assess network endpoints and the path(s) this traffic takes. Consider compatibility across existing equipment when planning for SSE. You want to integrate these new tools seamlessly and avoid wasting money on incompatible services. Thorough analysis helps to determine the suitability of a potential vendor(s) solution with your infrastructure.
- Current Setup: Assess the compatibility of existing network components with SSE solutions.
- Growth Planning: Evaluate if the vendor can accommodate future network expansion to avoid outgrowing their proposed solutions.
Redundancy and Distributed Fabric Importance
The importance of Redundancy and Distributed Fabric
Regardless if a company’s network is isolated within the same country or spans across the globe, network outages are not acceptable. With greater reach comes greater risk. The network must be designed in a redundant and distributed way. A well built SSE platform replicates services across data centers, allowing for automatic failover if one region was to become disconnected. Any selected vendor should provide solutions that enhance fault tolerance and ensure continuous operation, with some offering 100% uptime.
- Service Continuity: Solutions must maintain operations even in the event of component failures.
- Distributed Nature: Emphasise vendors who offer a widespread, distributed architecture that guarantees consistent security policy enforcement across all network entry points.
Critical Considerations for Transition
Above all considerations, a seamless transition ranks among top priorities. Transitioning to an SSE architecture requires careful planning and strategic execution. You should select a partner who clearly understands your requirements and strives for your success. The choice of an SSE vendor is a vital one and shouldn’t be rushed.
- Change Management: Investigate the vendor’s approach towards managing the transition without disrupting existing workflows.
- Vendor Transition Support: Ensure the vendor offers comprehensive support during the transition, including training and resources to facilitate a smooth migration.
Example SSE Provider: Atmos
Atmos by Axis Security is an SSE platform that integrates typical security features into a singular system. The Atmos service provides simplified access to businesses resources while providing comprehensive security.
Unified SSE Platform Features
The Atmos platform offers ZTNA, SWG, CASB and Digital Experience to provide a solid foundation for securing user connectivity between various public clouds and private applications.
- Atmos offers direct connectivity to applications without compromising security.
- ZTNA: Secure access to private apps.
- SWG: Monitors and controls online traffic for secure web access.
- CASB: Identify, manage and control cloud application use with enhanced security.
- Digital Experience: Improves user experience through performance insights and monitoring.
Atmos Direct Application Connectivity
Atmos supports direct application connectivity which provides an efficient and, most importantly, safe access to necessary business applications. Having a direct path avoids the convolutions of traditional VPN solutions where security risks often are overlooked.
Atmos enables granular identity-based access to minimise the attack surface against potential security breaches.
Single Pane of Glass Visibility
Consolidating visibility into a single pane is guaranteed to lead to streamlined security operations. Security/System/Network administrators gain full visibility into security events, network traffic and users application activity.
One interface to manage policies, monitoring and reporting erases the need to juggle multiple tools simultaneously, allowing greater focus on threat prevention. Platform Resilience and Redundancy It is essential that services stay running to ensure operational continuity during unforeseen disruptions. SSE platforms are built from the ground up with this in mind and allow for systems to withstand various cyber incidents yet continue to function with minimal impact to end users.
Cloud Giant Partnerships
The majority of vendors offer support for the major cloud service providers (AWS, Azure, GCP) some have relationships with one in particular. Partnerships with major cloud providers enhance platform resilience by enabling access to their extensive global infrastructure. This allows for capabilities such as disaster recovery via their global spread of data centres. Adopting a multi cloud approach should be considered.
Doing so reduces the dependency on a singular provider for critical services and the risk of vendor lock in. Network Acceleration and Reach Proactive acceleration and optimization is needed for achieving and maintaining a high quality network. Implementing techniques such as content delivery networks (CDNs) help maximise transportation throughput of data whilst reducing latency and potential bottlenecks. This leads to overall stability and keeping connections running smoothly.
Implementation Strategies for SSE
A proper implementation strategy for an SSE in any business consists of the following:
Assess Needs and Requirements: A major success factor is first assessing the need for the SSE. The organisation should conduct a risk assessment and formalise the security risks they plan to mitigate by implementing the SSE platform. Skipping this step can result in the entire requirement of the SSE being challenged later down the road.
Choose the Right SSE Solution: Not all SSE solutions are created equal. Organisations should carefully assess different vendors and solutions that are present to see which one is the right fit for the existing technology environment. Key factors include compatibility, platform reputation, level of training provided, support services. We recommend conducting demos of the platform before making any decision.
Implementing the SSE: Implementing the SSE consists of several steps such as:
- Training of IT staff
- Environment readiness
- Installation and configuration of the platform
- Pilot testing of the SSE components
- Reviewing Test results and resolving any issues
- Wider rollout to the entire organisation
- Training of the End users
- Fine-tuning and ongoing refinement of the SSE Policies
Monitoring: Post-implementation, the SSE and any configured alerts/policies must be refined. This allows the SSE to mature over time and become more in sync with the business environment.
