| This guide reviews the top-rated SASE vendors, helping businesses find the best solutions for network security. Vendors like Cato Networks, Zscaler, and Palo Alto are highlighted for their advanced capabilities in securing remote users and devices. The guide provides insights into SASE’s growing market, its features, and the benefits of cloud-based services. |
Our team tested, reviewed, and compared leading SASE network security vendors and managed service providers, which meet the requirements of most UK, North American and global businesses. Netify researchers have assessed SASE solutions across security features together with overall capabilities. Only the best SASE vendors and providers that fit the needs of most businesses have been included in this guide, with ratings assigned across each key area.
In 2024, there is numerous choices across SASE network security solutions – capabilities are stronger and evolving faster than ever, with significant advancements in AI, managed services, and security.
However, finding the right SASE solution for your business can be a difficult and protracted process. To assist with this, we’ve put together a comprehensive guide to the best SASE vendors and providers available in 2024. This guide includes our top recommendations for almost every sector and business size.
Readers looking to shortlist SD-WAN and network security vendors can now submit your requirements to receive quotes and solution capabilities from over 150 vendors. We vet each submission and only allow responses from solutions that are fit for your specific needs.
Tested by: Harry Yelland
Fact checked by: Robert Sturt
Updated: Monday 19th August 2024
We compare 10 leading SASE security vendors with an overview of the market.
2020-22 was a boon to vendors providing the technology that enabled society’s sudden transition to a remote, online lifestyle. Chief among them was SD-WAN, which became critical for organisations needing to maintain robust connectivity for Work-From-Home (WFH) employees tethered to video conferences for much of the day.
However, organisations soon realised that once they delivered reliable baseline communications, user and data security was the next layer of their hierarchy of needs. As we mentioned in our article on domestic SD-WAN vendors, “Security is the hottest sub-segment of the SD WAN market, with the emerging SASE market, which adds security features to an SD WAN solution, expected to more than double annually over the next several years, reaching 60 percent of SD WAN deployments by 2024 according to Gartner.”
SASE interest is so intense that Gartner’s latest Hype Cycle rankings put it at the Peak of Inflated Expectations, poised for the excitement to crater as buyers realise that SASE isn’t a silver bullet for all their security problems. Nonetheless, SASE solutions will be a critical addition to the security portfolio of the vast majority of enterprises that are permanently transformed into a work-from-anywhere organisation with remote, geographically dispersed employees. Indeed, Gartner sees the number of organisations adopting SASE quadrupling to 20 percent by 2023.
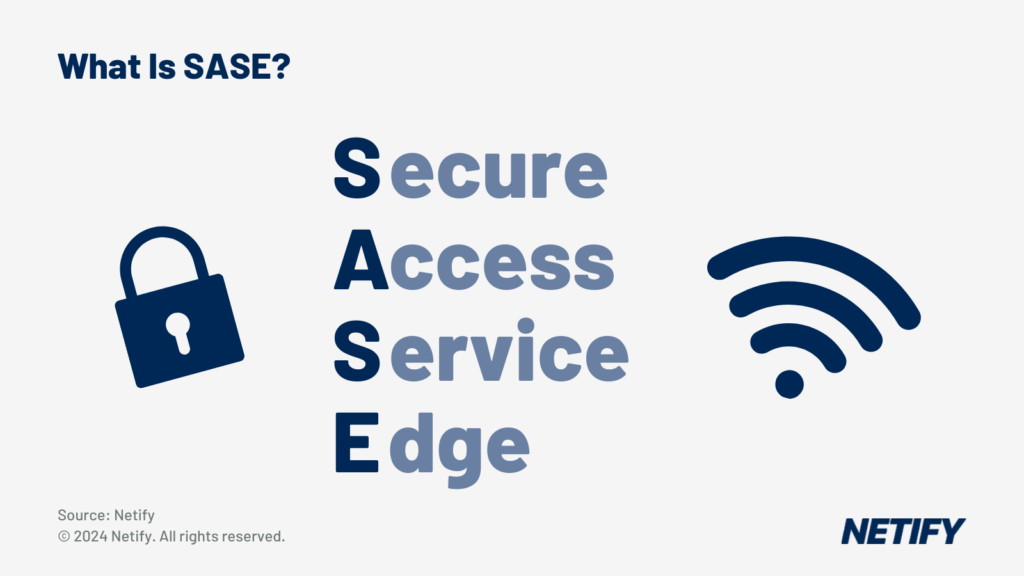
What Is SASE? SASE stands for Secure Access Service Edge - SASE stands for Secure Access Service Edge
SASE, namely Secure Access Service Edge, is a suite of capabilities designed for remote users, offices and devices that rides atop an SD-WAN substrate. In recent years, lower SASE pricing made potential deployments more affordable. While the concept is new, its components are not, contributing to rapid advances in the technology, product offerings and customer acceptance. It’s hard to quantify a SASE market because the terminology and means of implementing the technology are sufficiently malleable that some vendors are SASE-washing legacy network management or security products. Nonetheless, most analysts see a robust market, predicting triple-digit growth over the next few years. For example:
- Dell’Oro expects the SASE market to grow at 116 percent annually over the next five years, resulting in more than a 20-fold increase in revenues from 2020. Sales will start out primarily as SASE software bundled with hardware appliances, but will transition to a combination of software and cloud services managed by a carrier, ISP or SASE vendor.
- 650 Group is less bullish, but still predicts SASE revenue to quintuple by 2025 for a CAGR of 38 percent.
- Revenue at Zscaler, one of the few public pure-plays on cloud-based SASE products, is increasing 55 percent annually with billings up 71 percent year-over-year, numbers will make it a billion dollar company by mid-2022. Zscaler illustrates the potential for rapid expansion of SASE usage, with 5,000 customers, including 500 in Forbes’ Global 2000, and more than 20 million seats licensed accessing Zscaler’s services from one of 150 data centres worldwide.
SASE is a collection of network, user and application security technologies tailored for remote, edge locations like a branch office, retail store, warehouse or employee home. SASE can be implemented as a set of software and hardware appliances on private infrastructure, however, with organisations coping with pandemic uncertainty and lockdowns by significantly increasing the use of cloud infrastructure and applications, SASE is better consumed as a cloud-based service.
With WFH employees and remote contractors reliant on cloud services, it makes little sense tunneling their network traffic to privately-operated SASE infrastructure only to route it back out to the Internet. Far better to direct employee traffic to a globally distributed SASE service that is often hosted in the same hyperscale data centres used by the major SaaS applications. Thus, as we detail below, most SASE vendors are either an ‘arms dealer’ selling technology to a service provider or a combination of product developer and cloud service provider.
What are the primary features of SASE?
SASE is a Gartner neologism that has evolved into both a marketing buzzword and nascent product category. Despite differences in implementation, vendors invariably agree with Gartner’s canonical definition as comprising five elements.
- SD-WAN virtual network overlay that aggregates one or more physical networks, such as home broadband cable and DSL or branch office carrier Ethernet and 5G, into a logical connection. As we detail in our earlier report, SD-WAN uses a software control plane to improve link reliability, performance and predictability and that also allows inserting network services like those provided by SASE.
- Next-Generation Firewall-as-a-Service (NGFWaaS) that duplicates the features of a next-gen hardware firewall. Using software firewalls on a software-defined network like an SD-WAN allows for NFV (Network Function Virtualisation) service insertion at any point on the network, including edge locations like a branch office or employee’s virtual desktop environment.
- Secure Web Gateway (SWG) is an L7 Web content filter that supplements L3-L7 firewalls to block malicious traffic, enforce content and data access policies and monitor web traffic to identify potentially harmful anomalies or capacity bottlenecks. Unlike NGFWs, which are ‘bumps on the wire’, SWGs proxy servers that terminate traffic, which allows them to detect exploits that firewalls might miss.
- Cloud Access Security Broker (CASB) extends SWG, which focuses on Web content, to any Web- or cloud-based application, notably the many SaaS products WFH employees regularly use. CASB traditionally provides four features — traffic and application visibility, policy compliance, data security such as anomaly detection, sandboxing of suspicious code and enforcing TLS and threat protection for SaaS applications.
- Zero-Trust Network Access (ZTNA) is a granular replacement for point-to-point (or client-to-gateway) VPNs to improve network and application security. While VPNs protect network traffic from unauthorised snooping, without carefully designing subnets and gateway termination points, they don’t limit user access once authenticated on the VPN. In contrast, ZTNA treats every network connection attempt — for example, accessing a file share or collaboration system — as a separate transaction that requires authentication and authorisation before establishing a temporary encrypted TLS connection. ZTNA security policies are defined by three factors:
- The initiating device
- The initiating user
- The target application or service
ZTNA implementations typically include five elements: a. A Single Sign-On (SSO) service and associated user directory b. A device inventory with associated credentials c. A Certificate Authority (CA) d. A policy database and engine for security enforcement e. A device access proxy to terminate incoming requests
ZTNA eliminates vulnerabilities from a compromised VPN credential by enforcing granular access control over individual services and applications. ZTNA is often paired with Two-Factor Authentication (2FA) using a hardware security key or application-generated one-time passcodes. ZTNA was first popularized by Google’s 2014 BeyondCorp paper, which the company used as the model for a newly-released BeyondCorp Enterprise service.
When combined, SASE services provide comprehensive security for today’s distributed, cloud-first enterprise.
How to evaluate and compare SASE vendors?
Every significant network vendor has a SASE strategy and most have a product to sell, however modest, even if it involves linking multiple partners into a virtual network fabric. Since SASE is primarily an umbrella term for capabilities already widely available, it’s easy for vendors to craft a marketing message and slideware to woo prospective customers without investing in much product development. Thus, caveat emptor for feature washing.
Unfortunately, slides, web pages and a management interface linking in some network service partners might be the extent of the implementation for most vendors. Thus, any SASE product and vendor evaluation should start with detailed system architecture and service implementation. We say “service” because SASE is ideally delivered as a cloud service, not as installable, user-managed software. We agree with Aryaka product director Paul Liesenberg when he says that delivering the SASE vision requires “a seamlessly orchestrated, cloud-first network and full-security stack.”
After using the architecture and cloud implementation to filter the SASE trailblazers from the pretenders, next consider how your organisation’s priorities map to network optimisation, content filtering and security features. Rank and weight the following factors:
- Network performance (throughput, latency, jitter, availability)
- SaaS application coverage
- Integration with existing security systems and enterprise directories
- Global or regional coverage (Points of Presence – PoPs)
- Client support and limitations (if any).
Understand that given the immaturity and rapidly evolving nature of SASE products, buyers are unlikely to find any products excelling at every requirement, thus, prioritization is critical.
Finally, assess the vendor’s business and service model since there are three primary avenues for procuring SASE services:
- Directly from a SASE developer operating a cloud Network-as-a-Service (NaaS), typically by renting IaaS resources from one of the hyperscale cloud providers (AWS, Azure, Google Cloud, Alibaba Cloud), which provides broad international coverage and high availability.
- From a national or regional carrier like AT&T, Verizon, CenturyLink or Comcast.
- From a regional or national Managed Service Provider (MSP).
Carriers and MSPs usually don’t develop SD-WAN and SASE software. Instead, they buy from or partner with one of the companies we profile below, often large infrastructure vendors like Cisco, Palo Alto or VMware from whom they already buy network equipment and software.
We’ve narrowed down the list to a couple of finalists that meet most requirements and prefer those with integrated, self-contained systems over those that use virtual services provided by external partners.

Who are the best SASE vendors? - Who are the best SASE vendors?
Vendors
SASE Vendor Comparison
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Vendor | Overall Score | Key Features | Pros | Cons |
|---|---|---|---|---|---|---|---|---|---|
| 1 | hyelland | 23/10/2024 11:18 AM | hyelland | 23/10/2024 11:18 AM | Cato Networks | 91 | Global private backbone, Single-pass cloud engine, Built-in WAN optimisation, Full security stack, SD-WAN, ZTNA, CASB, DLP, Global PoPs | Highly integrated solution, Easy deployment, Comprehensive security features | Limited third-party integration, Higher cost for smaller businesses |
| 2 | hyelland | 23/10/2024 11:18 AM | hyelland | 23/10/2024 11:18 AM | Zscaler | 92 | Zero Trust architecture, SWG, Cloud-delivered security, CASB, DLP, Sandbox, Global PoPs, ZTNA, SD-WAN integration, AI/ML-powered threat intelligence | Scalable cloud-native architecture, Advanced threat protection, High-performance PoPs | Complex configuration, Premium pricing |
| 3 | hyelland | 23/10/2024 11:18 AM | hyelland | 23/10/2024 11:18 AM | Cisco Umbrella | 89 | DNS-layer security, SWG, CASB, SecureX integration, SD-WAN integration, Cloud access security, Malware protection, DLP, Cloud-native platform, Global PoPs | Extensive integrations, Strong DNS security, Unified security management | Steep learning curve, Requires Cisco ecosystem for full benefits |
| 4 | hyelland | 23/10/2024 11:18 AM | hyelland | 23/10/2024 11:18 AM | Palo Alto Networks Prisma Access | 87 | NGFW, Cloud-delivered security, SD-WAN, ZTNA, CASB, DLP, IoT security, Global PoPs, Advanced threat protection, AI-driven security, Autonomous digital experience management | Comprehensive security features, Integrated SD-WAN, High-performance cloud architecture | Complex deployment, Expensive licensing |
| 5 | hyelland | 23/10/2024 11:18 AM | hyelland | 23/10/2024 11:18 AM | Perimeter 81 | 82 | Global private backbone, Cloud-based architecture, SWG, ZTNA, CASB, DLP, Unified network security, Real-time monitoring, Multi-tenant management | Easy to deploy, User-friendly interface, Affordable pricing | Limited advanced features, Less suitable for large enterprises |
| 6 | hyelland | 23/10/2024 11:18 AM | hyelland | 23/10/2024 11:18 AM | Fortinet FortiSASE | 88 | Integrated NGFW, SWG, CASB, ZTNA, SD-WAN, Advanced threat protection, Global PoPs, Secure remote access, AI-powered threat intelligence, SSL inspection | Strong security capabilities, Unified threat management, Cost-effective solution | Complex management, Smaller PoP presence compared to competitors |
| 7 | hyelland | 23/10/2024 11:18 AM | hyelland | 23/10/2024 11:18 AM | Versa Networks | 90 | Integrated SD-WAN, NGFW, SWG, CASB, ZTNA, Cloud security, AI/ML-driven analytics, Unified management, Multi-cloud support, Global PoPs | Highly customisable, Strong SD-WAN capabilities, Real-time threat intelligence | Steep learning curve, Requires dedicated administration |
| 8 | hyelland | 23/10/2024 11:18 AM | hyelland | 23/10/2024 11:18 AM | Open Systems | 86 | Fully managed service, Integrated NGFW, SWG, ZTNA, SD-WAN, CASB, Global PoPs, Advanced threat protection, 24/7 support, Real-time analytics | Simplified deployment, Continuous monitoring, Strong customer support | Limited customisation, Higher cost for fully managed service |
| 9 | hyelland | 23/10/2024 11:18 AM | hyelland | 23/10/2024 11:18 AM | Aryaka | 87 | Global private backbone, Fully managed service, SD-WAN, NGFW, SWG, ZTNA, CASB, DLP, Real-time threat detection, Global PoPs | Optimised global performance, Fully managed service, Strong security integration | Limited customisation, Requires third-party last-mile management |
| Vendor | Overall Score | Key Features | Pros | Cons |
SASE Vendor Feature Comparison
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Security Feature | Cato Networks | Zscaler | Cisco Umbrella | Palo Alto Networks | Perimeter 81 | Fortinet FortiSASE | Versa Networks | Open Systems | Aryaka |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | hyelland | 23/10/2024 11:19 AM | hyelland | 23/10/2024 11:19 AM | Next-Generation Firewall (NGFW) | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| 2 | hyelland | 23/10/2024 11:19 AM | hyelland | 23/10/2024 11:19 AM | Secure Web Gateway (SWG) | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| 3 | hyelland | 23/10/2024 11:19 AM | hyelland | 23/10/2024 11:19 AM | Anti-malware/Anti-virus | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| 4 | hyelland | 23/10/2024 11:19 AM | hyelland | 23/10/2024 11:19 AM | Intrusion Prevention System (IPS/IDS) | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| 5 | hyelland | 23/10/2024 11:19 AM | hyelland | 23/10/2024 11:19 AM | Zero Trust Network Access (ZTNA) | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| 6 | hyelland | 23/10/2024 11:19 AM | hyelland | 23/10/2024 11:19 AM | URL Filtering | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| 7 | hyelland | 23/10/2024 11:19 AM | hyelland | 23/10/2024 11:19 AM | Encryption/SSL Inspection | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| 8 | hyelland | 23/10/2024 11:19 AM | hyelland | 23/10/2024 11:19 AM | Cloud Access Security Broker (CASB) | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| 9 | hyelland | 23/10/2024 11:19 AM | hyelland | 23/10/2024 11:19 AM | Data Loss Prevention (DLP) | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| 10 | hyelland | 23/10/2024 11:19 AM | hyelland | 23/10/2024 11:19 AM | Managed Security Services | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Security Feature | Cato Networks | Zscaler | Cisco Umbrella | Palo Alto Networks | Perimeter 81 | Fortinet FortiSASE | Versa Networks | Open Systems | Aryaka |
Cato SASE
We start our list with the first SASE platform developed from scratch, Cato Networks. Cato are well known for offering their own global private backbone which enables customers to use their connectivity across more than 75 Points of Presence (PoPs). Cato’s private backbone optimises and secures long distance connections, enabling organisations with sites spread around the world to improve and protect their connections.
To begin testing, we deployed Cato SASE via Cato Management and followed the automated configuration process to create a new site. Through automation, Cato made the deployment process very easy and reduced the manual workload that we experienced significantly.
The integrated features in Cato SASE form its full network security stack offering with Next Generation Firewall (NGFW), Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), Data Loss Prevention (DLP) and Zero Trust Network Access (ZTNA). After deploying, we decided to test out some of the security functions that Cato SASE provided, with the NGFW capabilities first.
Configuring the Next Generation Firewall settings was a straightforward process, all contained inside Cato Management. Once setup, we began testing by attempting to access blocked websites from within the network. We noted that Cato prevented access to the websites, identifying them as being part of the configured blacklist. Through testing, this proved to us that the NGFW capabilities of Cato could adequately prevent access to potentially malicious sites in a real-world scenario.
Following the firewall, we wanted to test the antimalware capabilities in order to determine if the network security could still prevent breaches, should access to a malicious website still occur. By placing a controlled piece of malware onto the network, we were able to monitor how Cato dealt with it. The anti-malware feature quickly identified the threat and placed it in quarantine to prevent further spread of the breach.
Why Consider Cato SASE?
We would recommend Cato’s SASE solution for large enterprises with globally spread branch offices. The offering of Cato’s private backbone also makes this solution ideal for global co-managed service requirements.
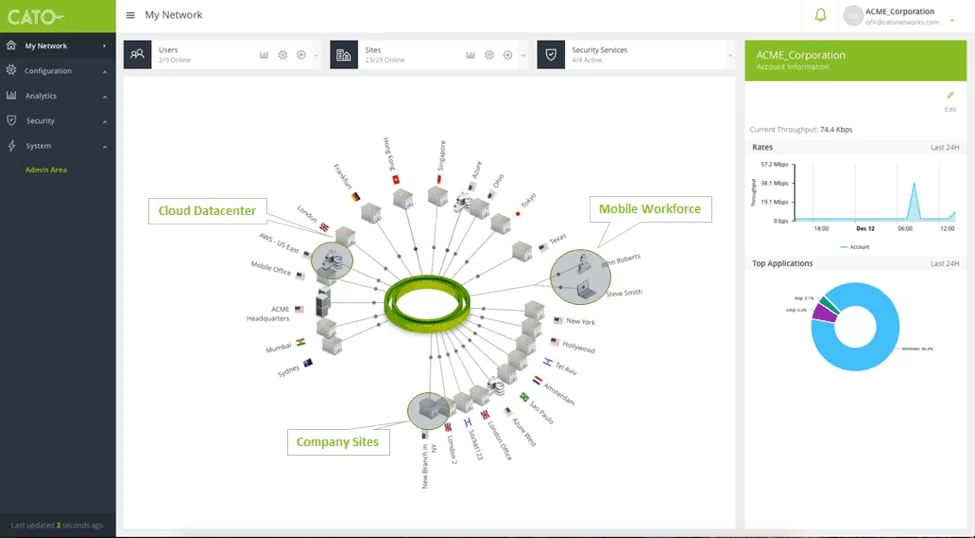
Screenshot of the Cato Dashboard - Screenshot of the Cato Dashboard
OVERALL SCORE: 90
SASE Features: 9.0
Overall SASE Capability: 9.0
Threat Detection and Response: 8.0
User and Entity Behaviour Analytics (UEBA): 9.0
Data Protection and Privacy: 8.0
Management and Orchestration: 9.0
Scalability and Cloud Integration: 9.0
Cost and Return on Investment (ROI): 8.0
Features: Global Private Backbone, NGFW, SWG, CASB, DLP
Editors Note: Best for Global Co-Managed Requirements
Cato SASE Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 23/10/2024 11:11 AM | hyelland | 23/10/2024 11:11 AM | ✓ Simplified Deployment: Easy and quick to deploy. | ❌ Lacks Granular Control: Does not offer detailed configuration options for advanced users. |
| 2 | hyelland | 23/10/2024 11:11 AM | hyelland | 23/10/2024 11:11 AM | ✓ Simplified Management: Easy to set up and manage. | ❌ Limited Third-Party Integrations: Integration options with third-party tools are limited. |
| 3 | hyelland | 23/10/2024 11:11 AM | hyelland | 23/10/2024 11:11 AM | ✓ Optimised Routing: Provides optimised routing for better network performance. | |
| Pros | Cons |
Cisco Umbrella
Cisco has a dual-track SASE strategy based on its Viptela (data centre, carrier) and Meraki (client) SD-WAN products, Umbrella cloud security service and Secure Access by Duo zero-trust 2FA and endpoint visibility products. Cisco is a prime example of a company with the SASE technology pieces already in place, understands the vision, but is still working through the product and service integration and customer education and migration plans.
Whilst Zscaler had potential issues with the flexibility and scalability of their SASE solution, Cisco offers one of the more flexible SASE solutions in this list. Falling under the wide range of products that Cisco has to offer, Cisco Umbrellaintegrates with other Cisco services, such as Cisco Catalyst SD-WAN and SecureX.
To deploy Cisco Umbrella, we started by configuring settings such as the internal networks and public IP ranges, DNS-layer security snd firewall. This process was much more complex than that of Cato and Zscaler, highlighting the complexity of the workload for network administrators.
Given Cisco Umbrella can offer a wide range of security features through its modular Cisco integration architecture, we decided to focus on already integrated security features when testing. The first of these features being Cisco Umbrella’s DNS security capabilities, which should filter out blacklisted websites. On testing we found that Cisco Umbrella was capable of effectively prevent access to all blacklisted sites, which would prevent access to potentially malicious sites in a real-world scenario.
In the event that a networked user does gain access to a malicious site, Cisco Umbrella offers remote browser isolation functionality to help prevent session hijacking or data loss. We noted that the browser isolation provided with Cisco Umbrella was effective at shielding against threats, potentially stopping zero-day exploits and malware threats.
Why Consider Cisco Umbrella SASE?
Whilst Cisco Umbrella offered us with an extensive SASE solution, we did notice even when deploying the step-up in complexity for management when compared to the previous two entries on this list. We’d therefore recommend Cisco Umbrella to organisations to large scale organisations that are already leveraging other Cisco products, with expert network administrators.
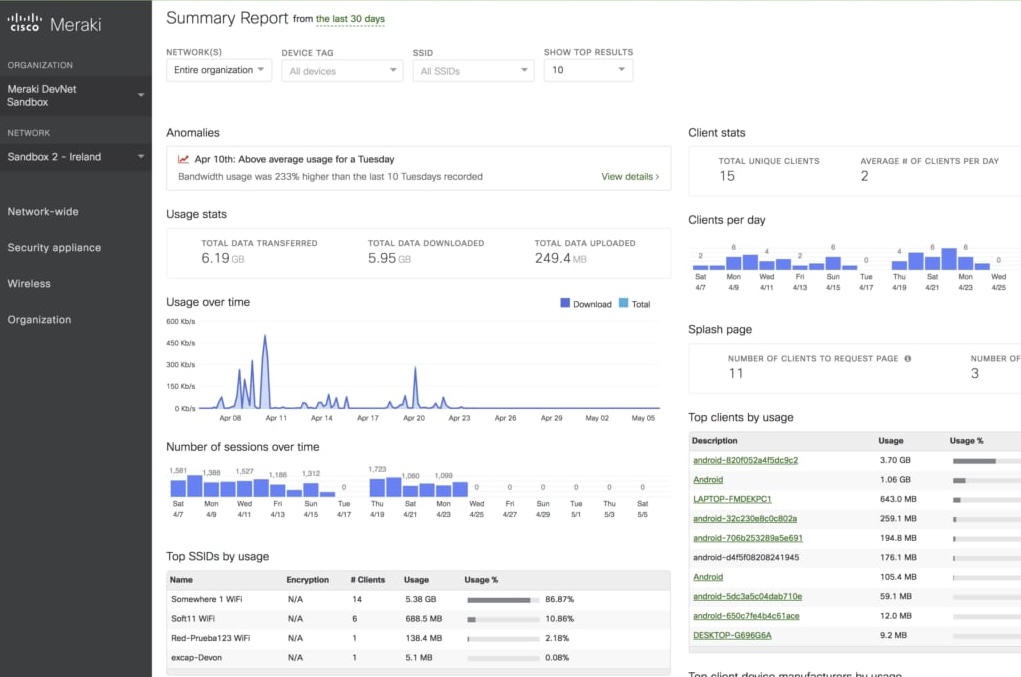
The Meraki security portal provides continuous updates of the threat telemetry for known attack vectors affecting Meraki products and the networks they protect.
These include exploits, malware signatures and malicious URLs used in phishing attacks. If a threat is detected on a customer’s network it can be isolated within seconds through an automated process within the cloud infrastructure before entering their network.
Cisco Umbrella cybersecurity services were effective at stopping malware attacks after researchers discovered a new way to steal data.
After finding a technique called domain shadowing, security researcher Kevin Beaumont decided to test if Cisco Umbrella would stop the attack, which was carried out by infecting local servers. He found that the service blocked 91 percent of phishing URLs from landing on his machine even before they were redirected to their final destination. According to Beaumont, another anti-virus defense system had only stopped about 80 percent of the attacks.
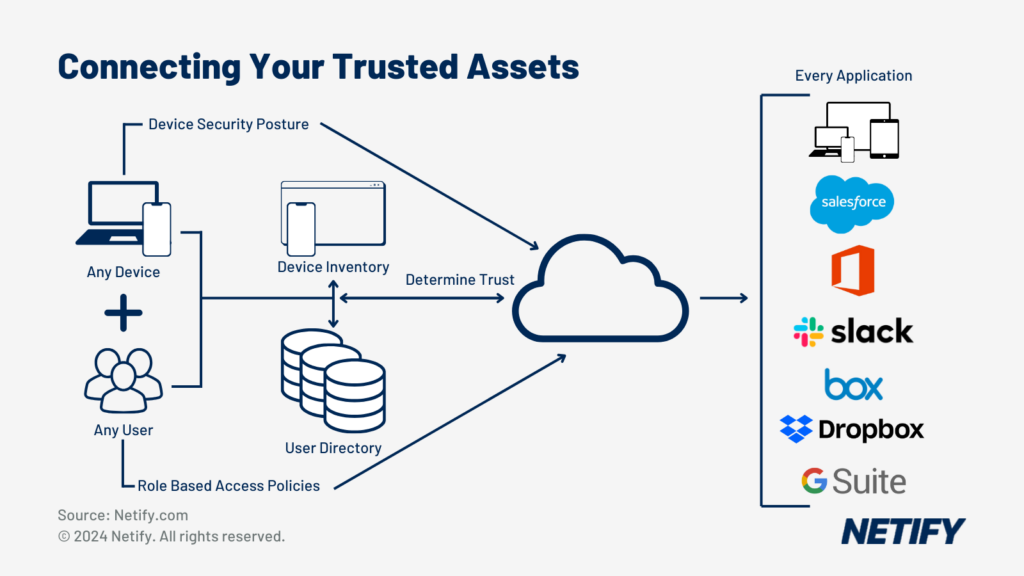
- Zero Trust Network Access (ZTNA) within SASE
OVERALL SCORE: 88
SASE Features: 8.0
Overall SASE Capability: 8.0
Threat Detection and Response: 9.0
User and Entity Behaviour Analytics (UEBA): 8.0
Data Protection and Privacy: 8.0
Management and Orchestration: 8.0
Scalability and Cloud Integration: 9.0
Cost and Return on Investment (ROI): 7.0
Features: Advanced Threat Detection
Editors Note: Best for Granular Security Requirements
Cisco SASE Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 23/10/2024 11:11 AM | hyelland | 23/10/2024 11:11 AM | ✓ Optimised Routing: Provides optimised routing for better network performance. | ❌ Lacks Advanced Sandboxing: Does not include advanced sandboxing capabilities. |
| 2 | hyelland | 23/10/2024 11:11 AM | hyelland | 23/10/2024 11:11 AM | ✓ Granular Security Control: Offers detailed security controls. | ❌ Lacks Behavioural Analysis: Does not provide in-depth behavioural analysis features. |
| 3 | hyelland | 23/10/2024 11:11 AM | hyelland | 23/10/2024 11:11 AM | ❌ Advanced performance and security capabilities: Advanced features may be challenging for some users. | |
| Pros | Cons |
Fortinet
Fortinet, well known for their security capabilities, offers FortiSASE, a solution that integrates Fortinet’s threat intelligence from FortiGuard Labs. FortiSASE differentiates itself by integrating Artificial Intelligence to provide analysis of analytics and offer proactive security measures across its SASE solution. With over 30 Points of Presence globally, Fortinet doesn’t have the largest backbone in this list, however does show that connectivity is also important to Fortinet, as well as security.
Deployment of FortiSASE was slightly more involved than with other solutions, requiring segments, tunnels and policies all to be setup within the FortiSASE management console.
Once deployed, we began testing of the security features that FortiSASE had to offer. Our testing focused on two key features, endpoint protection and deep SSLinspection.
The first of these tests was focused on FortiSASE’s endpoint protection. Placing a controlled virus onto the network, we noted that FortiSASE quickly identified and mitigated these threats, ensuring breaches could not spread or cause impact. The effectiveness of Forti-SASE’s AI-driven threat intelligence was evident in its ability to adapt and respond to new threats, which included zero-day threats.
Whilst the endpoint protection can protect against breaches from occurring, FortiSASE offers Secure Socket Layer (SSL) inspection capabilities to detect breaches within encrypted traffic on the network. Fortinet’s SSL inspection capabilities were highly effective, revealing and mitigating threats concealed within encrypted communications without significant degradation of connection speeds. This is a common challenge with SSL inspection technologies and we were surprised by its effectiveness.
Why Consider Fortinet FortiSASE?
We would strongly recommend Fortinet FortiSASE for large enterprises with a focus on security or for businesses that have many branch offices all connecting to networked resources.
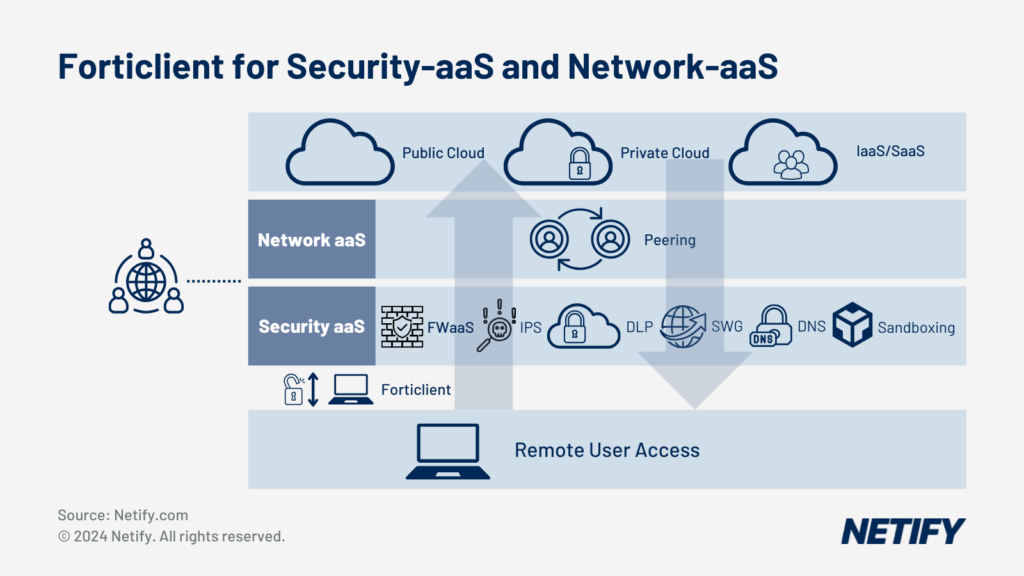
Forticlient For Security-as-a-Service and Network-as-a-Service - Forticlient For Security-as-a-Service and Network-as-a-Service
OVERALL SCORE: 87
SASE Features: 8.0
Overall SASE Capability: 8.0
Threat Detection and Response: 8.0
User and Entity Behaviour Analytics (UEBA): 8.0
Data Protection and Privacy: 8.0
Management and Orchestration: 8.0
Scalability and Cloud Integration: 8.0
Cost and Return on Investment (ROI): 7.0
Features: Global Private Backbone, AI-Threat Detection
Editors Note: Best for Highly Secure Branch Office and Remote Users
Fortinet SASE Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 23/10/2024 11:12 AM | hyelland | 23/10/2024 11:12 AM | ✓ Simplified Deployment: Easy and quick to deploy. | ❌ Limited Legacy Application Support: Limited support for legacy applications. |
| 2 | hyelland | 23/10/2024 11:12 AM | hyelland | 23/10/2024 11:12 AM | ✓ Advanced Security: Provides advanced security features. | ❌ Highly Secure Branch Office and Remote Users: Advanced security features may be challenging for branch offices and remote users. |
| Pros | Cons |
Open Systems
An ideal solution for businesses requiring a managed SASE solution, Open Systems SASE is backed by their mission control support team, which provides business with simplified network management.
When deploying Open Systems SASE, we leaned on the managed services to help us to quickly configure the location, service connections and user authorisation integrations.
Once deployed, our testing began with Open System’s cloud sandboxingcapabilities. We introduced malware samples across the network in order to see how effectively Open Systems could deal with threats within its contained environment. Open Systems SASE quickly isolated all threats and ensured they could not spread to other network segments.
Whilst the sandboxing capabilities analyses potential threats, Open Systems also offers URL filtering to prevent initial access to potentially malicious sources. By configuring a list of blacklisted sites, we tested Open System’s URL filtering by attempting to connect to blocked sites. By rejecting each of our connection attempts, Open Systems SASE highlighted the ability of its URL filtering capabilities to protect against malicious sites.
Why Consider Open Systems SASE?
It should be noted that Open Systems’ SASE solution does not offer the same level of customisation as the other vendors on this list. We would therefore recommend Open Systems SASE for businesses that require a fully managed SASE solution and 24/7 monitoring, management and support.
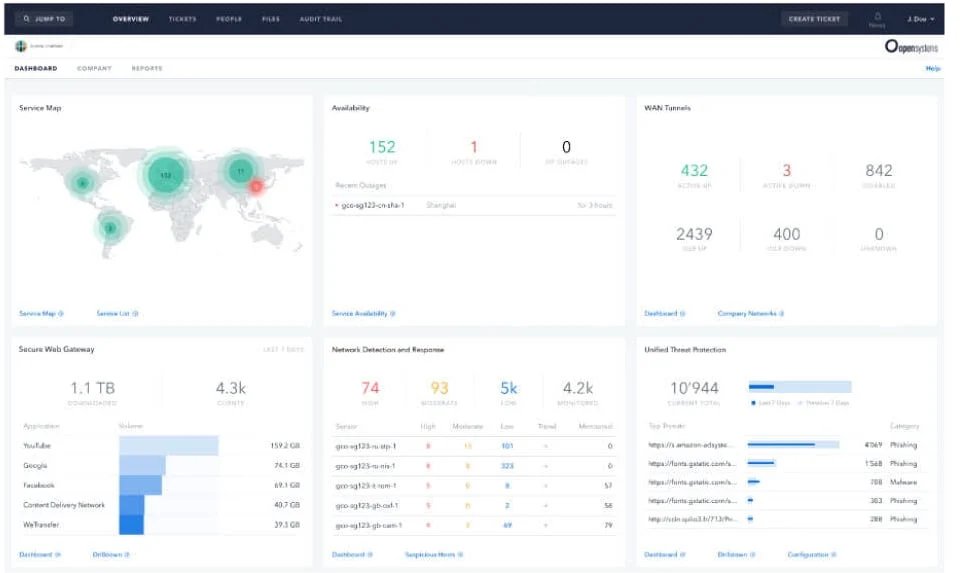
Screenshot of Open Systems Dashboard - Screenshot of Open Systems Dashboard
OVERALL SCORE: 86
SASE Features: 8.0
Overall SASE Capability: 8.0
Threat Detection and Response: 9.0
User and Entity Behaviour Analytics (UEBA): 9.0
Data Protection and Privacy: 8.0
Management and Orchestration: 9.0
Scalability and Cloud Integration: 9.0
Cost and Return on Investment (ROI): 8.0
Features: Managed Solution, Advanced Threat Detection
Editors Note: Best for Fully Managed SASE Solution
OpenSystems SASE Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 23/10/2024 11:14 AM | hyelland | 23/10/2024 11:14 AM | ✓ Advanced Security: Provides advanced security features. | ❌ Limited Customisation: Limited options for customisation. |
| 2 | hyelland | 23/10/2024 11:14 AM | hyelland | 23/10/2024 11:14 AM | ❌ Fully Managed SASE Solution: Being fully managed may limit flexibility for some users. | |
| Pros | Cons |
Palo Alto
Palo Alto Networks’ SASE solution is a combination of CloudGenix SD-WAN, which the company acquired last year and Palo Alto’s Prisma Access security service. CloudGenix is delivered as a physical appliance with various sizes for both data centres and branch offices and includes ML analytics and automation features to improve performance and manageability. Prisma Access is a cloud-based SASE service that includes NGFW-as-a-service, SWG, CASB, DLP content filtering, ZTNA, SSL inspection, sandboxing of suspicious code and DNS security (automatic blacklisting of suspicious domains). Palo Alto has recently improved the integration of CloudGenix with Prisma Access by allowing the two to be deployed and configured with one operation.
Palo Alto Networks provides comprehensive security services including cloud based next generation firewalls with advanced threat protection technologies to detect known threats as well as zero-day exploits in real time for all applications on the network. Other security functionalities include Application layer firewalls, traffic shaping and VLAN management. The company came across a malware sample downloaded from the DarkComet Command and Control (C&C) servers which uses DNS tunnelling to communicate with the C&C server. Palo Alto Threat Intelligence has identified that this malware is in active use by different threat actors targeting victims worldwide since November 2013 with attack campaigns in Turkey in December 2013 and in Malaysia in March 2014.
In recent years there has been an increasing adoption of Internet of Things (IoT) devices for businesses such as for Industry 4.0 manufacturing use cases. With that in mind, no SASE solution is as tailored made for securing IoT environments as Prisma Access by Palo Alto Networks.
The deployment process was of similar difficulty to the previous entry in this list, Cisco Umbrella. Deploying Prisma Access required us to configure the network segmentation, setup IPsec tunnels and route both remote and mobile connections via cloud providers.
The first security feature we tested within Prisma Access was its Secure Web Gateway (SWG) capabilities. SWG is designed to identify and block potentially malicious websites and downloads, Upon testing, Prisma Access quickly blocked us from visiting malicious sites and helped to prevent us from downloading potentially dangerous files.
After testing the SWG, we moved onto the Cloud Access Security Broker (CASB) capabilities. CASB ensures secure connectivity to cloud resources and controls cloud data flows. We found that Prisma Access’ Cloud Access Security Broker capabilities prevented cloud access to unauthorised connections, ensuring cloudresources are protected. To assist with monitoring protection, CASB provided cloud access visibility, which we use to monitor the testing results.
Why Consider Palo Alto Prisma SASE?
Unlike some of the other SASE vendors in this comparison, Prisma Access does not offer its own private backbone. Due to this, Prisma uses a public backbone of Points of Presence (PoPs) utilising cloud services for connectivity. Due to being public, this poses potential scalability limits and restricts businesses from regulatory compliance in some sectors.
We would therefore recommend Prisma Access for large enterprises which require Industry 4.0 or IoT integrations.
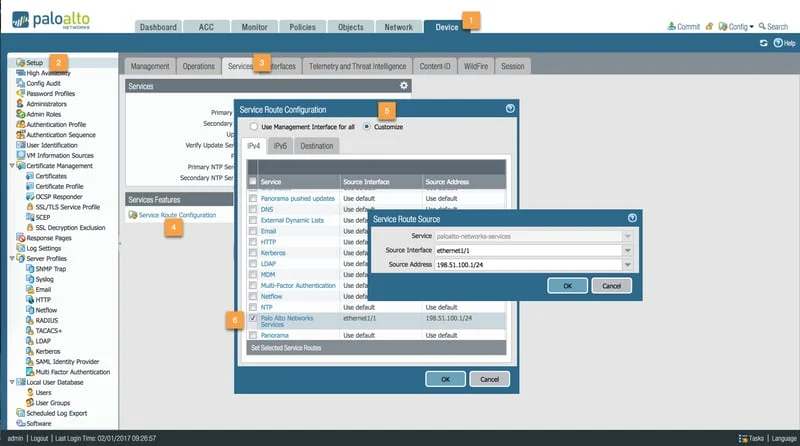
Screenshot of Palo Alto’s Dashboard - Screenshot of Palo Alto’s Dashboard
OVERALL SCORE: 85
SASE Features: 7.0
Overall SASE Capability: 8.0
Threat Detection and Response: 9.0
User and Entity Behaviour Analytics (UEBA): 8.0
Data Protection and Privacy: 9.0
Management and Orchestration: 8.0
Scalability and Cloud Integration: 8.0
Cost and Return on Investment (ROI): 7.0
Features: IoT support
Editors Note: Best for IoT Support Requirements
Palo Alto SASE Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 23/10/2024 11:13 AM | hyelland | 23/10/2024 11:13 AM | ✓ Legacy Proxy Support: Supports legacy proxy technologies for compatibility. | ❌ Relies on Third Party PoPs: Dependent on third-party Points of Presence (PoPs) for connectivity. |
| 2 | hyelland | 23/10/2024 11:13 AM | hyelland | 23/10/2024 11:13 AM | ✓ Integrated Experience Monitoring: Provides integrated experience monitoring for enhanced visibility. | ❌ Industry 4.0 and IoT Security: Advanced performance and security capabilities may be challenging for Industry 4.0 and IoT environments. |
| Pros | Cons |
Versa Networks
Similarly to FortiSASE, Versa SASE stands out for its integration of Artificial Intelligence (AI) and machine learning (ML) capabilities. These technologies have been implemented to provide real-time network insights and automated threat response.
Deployment of Versa SASE was much more long-winded in comparison to the other vendors on this list. Whilst this can be looked upon as a limiting factor, this complexity comes as a result of the abundance of features that Versa SASE has to offer.
The first security feature we tested was the Next Generation Firewall (NGFW) capabilities of Versa SASE. Configuring the Next Generation Firewall settings was a straightforward process, all contained inside Versa Director. Once setup, we began testing by attempting to access blocked websites from within the network. We noted that Versa prevented access to the websites, identifying them as being part of the configured blacklist. Through testing, this proved to us that the NGFW capabilities of Versa could adequately prevent access to potentially malicious sites and noted that Versa Director allowed us to view the nature and source of attacks, which could be crucial in a real-world scenario.
Following the testing of Versa’s NGFW, we began focusing on Versa’s Virtual Private Network (VPN) capabilities. Versa’s VPN creates a tunnel between remote sites and the network to allow data and resource sharing across geographically distant locations. Versa’s VPN created a quick and secure tunnel to networked resources, effectively encrypting traffic and ensuring secure connectivity for remote users under varying network conditions.
Why Consider Versa SD-WAN?
Due to the volume of features, complexity of deployment and management and the availability of in-depth real-time analytics, we would recommend Versa SASE for organisations requiring granular control over their security policies. We would, however, caveat this by suggesting that a dedicated network administration team may be required given the complexity of Versa’s solution.
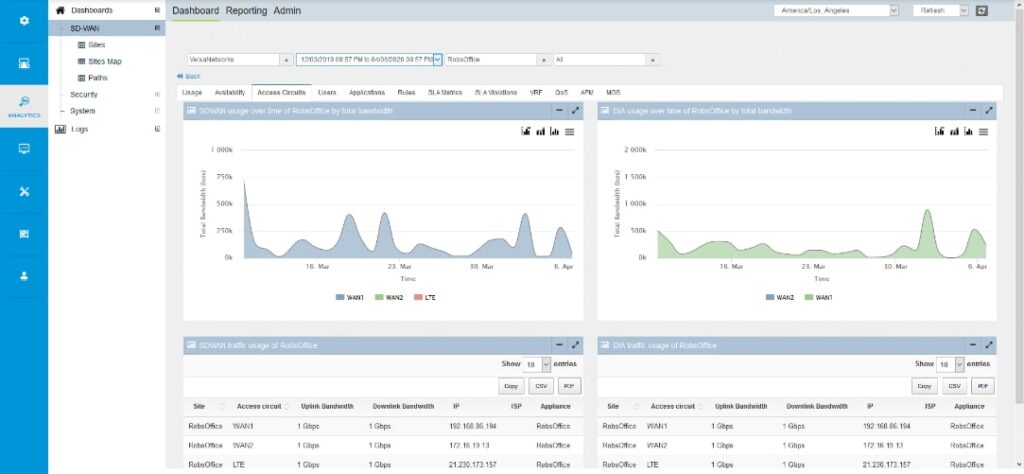
OVERALL SCORE: 89
SASE Features: 9.0
Overall SASE Capability: 8.0
Threat Detection and Response: 9.0
User and Entity Behaviour Analytics (UEBA): 9.0
Data Protection and Privacy: 8.0
Management and Orchestration: 8.0
Scalability and Cloud Integration: 8.0
Cost and Return on Investment (ROI): 8.0
Features: Managed Solution
Editors Note: Best for Service Provider Delivered SASE
Versa SASE Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 23/10/2024 11:15 AM | hyelland | 23/10/2024 11:15 AM | ✓ Simplified Management: Easy to manage with minimal complexity. | ❌ Slow Onboarding: Onboarding process can be slower than expected. |
| 2 | hyelland | 23/10/2024 11:15 AM | hyelland | 23/10/2024 11:15 AM | ✓ Advanced Security: Provides advanced security features. | ❌ Service Provider Delivered SASE: Relies on service provider for SASE delivery, which may limit customisation. |
| Pros | Cons |
VMware
VMware SASE combines a VeloCloud SD-WAN backbone with ZTNA secure access, SWG, CASB and an NSX-based NGFW in a service delivered from more than 100 VMware SASE PoPs worldwide. It’s secure access gateway supports passthrough, RADIUS, SecurID (one-time passcode), smartcards/2FA tokens, certificates and SAML federated authentication. Access gateways work with VMware’s Workspace ONE client, which provides endpoint security and management.
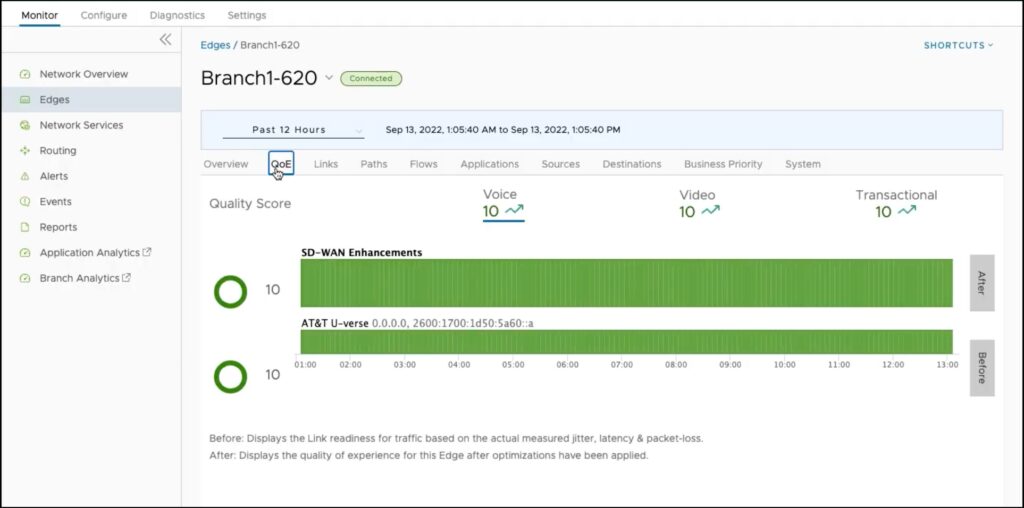
VMware SD-WAN Pros and Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 21/10/2024 04:00 PM | hyelland | 21/10/2024 04:00 PM | ✓ Scalable: Offers scalability to meet the needs of growing businesses. | ❌ Scaling Issues: Some users report issues when scaling the solution to larger environments. |
| 2 | hyelland | 21/10/2024 04:00 PM | hyelland | 21/10/2024 04:00 PM | ✓ Simple Deployment: Easy and quick to deploy. | ❌ Feature Limitations: Certain features have limitations, restricting advanced configurations. |
| 3 | hyelland | 21/10/2024 04:00 PM | hyelland | 21/10/2024 04:00 PM | ✓ Multi-cloud: Supports multicloud environments, allowing integration with multiple cloud providers. | ❌ Complexity: The solution can be complex to configure and manage. |
| 4 | hyelland | 21/10/2024 04:00 PM | hyelland | 21/10/2024 04:00 PM | ✓ Integrated Security: Provides integrated security features for enhanced protection. | |
| 5 | hyelland | 21/10/2024 04:00 PM | hyelland | 21/10/2024 04:00 PM | ✓ Public Gateways: Offers public gateways for improved connectivity options. | |
| 6 | hyelland | 21/10/2024 04:00 PM | hyelland | 21/10/2024 04:00 PM | ✓ Efficient QoS Configuration: Quality of Service (QoS) is efficiently managed. | |
| Pros | Cons |
Zscaler
Similar to Cato, Zscaler offers over 150 global Points of Presence, enabling secure connectivity from a range of sites and locations. However, unlike Cato, Zscaler SASE is well known for its Zero Trust architecture implementation. Zero Trust enforces that there is no implicit trust for users across the network and requires clients to continuously verify their identity. In addition to this, Zscaler implements micro-segmentation to prevent unauthorised access spreading between applications.
When compared to Cato, the deployment process of Zscaler was not quite as straightforward. For setting up the SASE solution, we configured the private access (ZPA) and internet access (ZIA) policies, as well as the security services. These services included Zscaler’s full network security stack, Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), Data Loss Prevention (DLP) and Next Generation Firewall (NGFW).
Our testing began with Zscaler’s sandboxing capabilities. We introduced a variety of malware samples across the network in order to see how effectively Zscaler could deal with threats in a contained environment. Zscaler’s quickly identified all threats, isolating malicious payloads from the rest of the network and ensuring they could not spread to other segments.
Similar to sandboxing, which enables malware to be investigated within an isolated segment, Zscaler also offers browser isolation. Browser isolation protects end-user’s devices web sessions by segmenting traffic from each webpage and applications traffic. This helps to prevent against session hijacking and other malicious exploits that risk web applications may attempt. The combination of these features highlights Zscaler’s ability to protect users from breaches and their effects, reducing the vulnerabilities of Zscaler by reducing the attack plane.
Why Consider Zscaler SASE?
Within the market, Zscaler has experienced some issues related to scalability and performance, particularly with its Zscaler Private Access (ZPA) feature. Although we did not notice any latency within our testing, some users have reported latency issues and this can impact user experience in large-scale deployments. Due to these limitations, we would recommend Zscaler for large multinational enterprises that can manage potential scalability concerns.
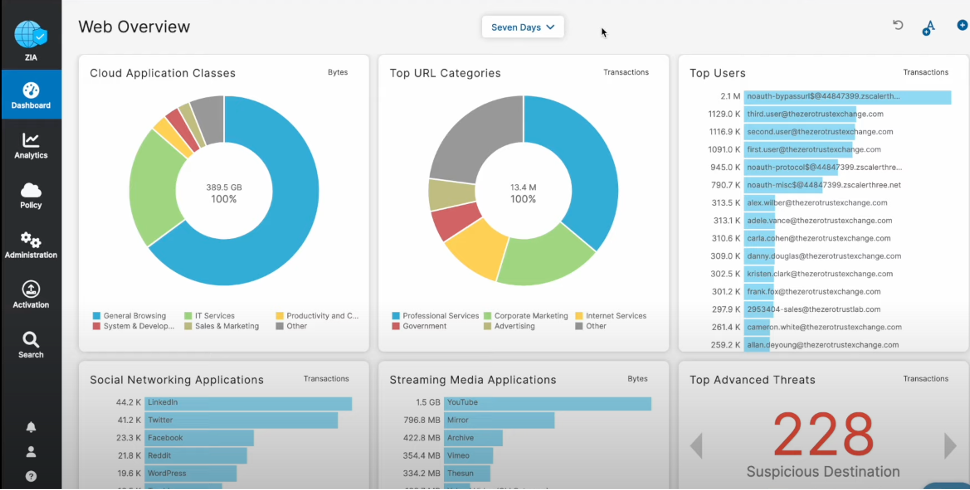
Zscaler was the first CASB vendor to integrate with Intel AMT and we continue to lead this industry by delivering constant protection against cyber threats, regardless of device or location. As part of our powerful integration with Intel AMT, Zscaler can detect compromised laptops as well as exfiltration attempts through covert channels like TeamViewer, VNC, RDP and Citrix through out-of-band management traffic. The Zscaler service is accessible from anywhere using a modern web browser; there’s no need for costly VPN provisioning or network changes.
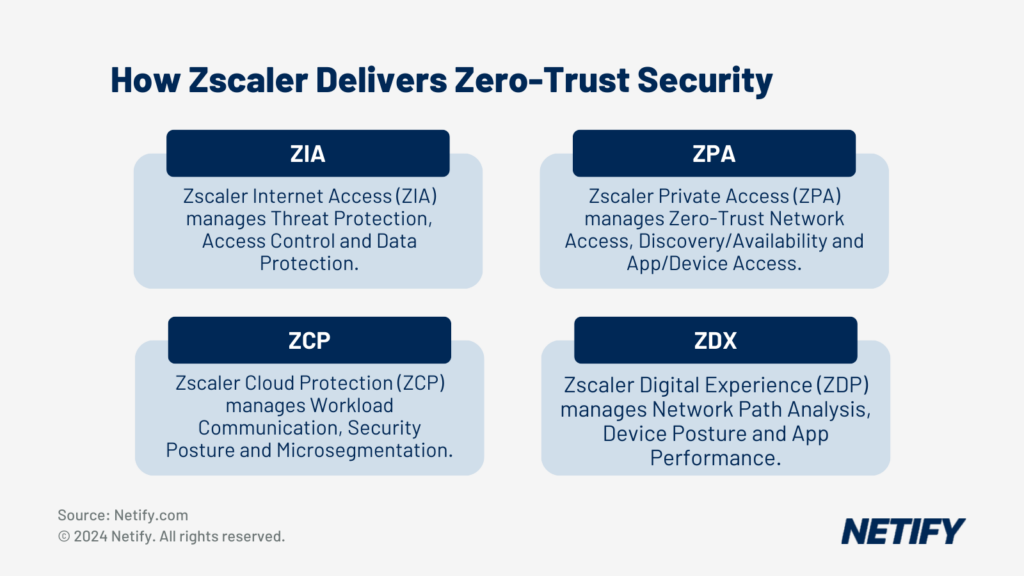
How Zscaler delivers Zero-Trust Security - How Zscaler delivers Zero-Trust Security
OVERALL SCORE: 92
SASE Features: 9.0
Overall SASE Capability: 9.0
Threat Detection and Response: 9.0
User and Entity Behaviour Analytics (UEBA): 9.0
Data Protection and Privacy: 9.0
Management and Orchestration: 8.0
Scalability and Cloud Integration: 9.0
Cost and Return on Investment (ROI): 7.0
Features: ZTNA, SSL/TLS Traffic Decryption
Editors Note: Best for Granular Security Requirements
Zscaler SASE Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 23/10/2024 11:16 AM | hyelland | 23/10/2024 11:16 AM | ✓ Optimised Routing: Provides optimised routing for better network performance. | ❌ Limited Legacy Application Support: Limited support for legacy applications. |
| 2 | hyelland | 23/10/2024 11:16 AM | hyelland | 23/10/2024 11:16 AM | ✓ Granular Security Control: Offers detailed security controls. | ❌ Granular Security Control for Large Corporations: Managing granular security controls can be challenging for large corporations. |
| Pros | Cons |
Aryaka
Aryaka joins the list of vendors on this comparison to other a global private backbone. With over 40 Points of Presence (PoPs) worldwide and a fully managed SASE solution, businesses with requirements for worldwide connectivity and 24/7 support should consider Aryaka as a contender.
The deployment process for Aryaka SASE was straightforward, with configuration of Aryaka OnePass, Next Generation Firewall (NGFW), Deep Packet Inspection (DPI) and anti-malware contained in the MyAryaka platform.
The first security feature we tested was Aryaka’s Zero Trust Network Access (ZTNA) functionality. Aryaka’s ZTNA capabilities are delivered through Aryaka OnePass, which enforces access policies consistently across the entire network.
ZTNA through Aryaka OnePass policy enforce. We then attempted to access networked resources with a user account that did not have sufficient privileges and noted that the connection was promptly rejected. Switching to an account that had the missing privileges, we noted that Aryaka allowed access and there were no performance drops whilst Aryaka verified authorisation.
We then tested Aryaka’s anti-malware capabilities, placing a controlled virus onto the network. Once placed we noted that Aryaka SASE quickly detected the malware and provided us with real-time alerts and reports. These insights enable real-world network administrators to make informed and proactive tweaks to security policies.
Why Consider Aryaka SASE?
We would recommend Aryaka SASE for businesses requiring a fully managed SASE solution and last-mile circuit management.
OVERALL SCORE: 88
SASE Features: 8.0
Overall SASE Capability: 8.0
Threat Detection and Response: 8.0
User and Entity Behaviour Analytics (UEBA): 8.0
Data Protection and Privacy: 8.0
Management and Orchestration: 8.0
Scalability and Cloud Integration: 8.0
Cost and Return on Investment (ROI): 8.0
Features: Global Private Backbone, ZTNA
Editors Note: Best for Fully Managed SASE and Last-Mile Circuit Management
Aryaka SASE Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 23/10/2024 11:10 AM | hyelland | 23/10/2024 11:10 AM | ✓ Simplified Management: Easy to manage with minimal complexity. | ❌ Limited Customisation: Limited options for customisation. |
| 2 | hyelland | 23/10/2024 11:10 AM | hyelland | 23/10/2024 11:10 AM | ❌ Fully Managed SASE and Last-Mile Circuit Management: Being fully managed may limit flexibility for last-mile circuit management. | |
| Pros | Cons |
What are use cases for SASE and the recommendations?
- Integration with existing network infrastructure and management software. For example, organisations with significant investments in Cisco or VMware products should start evaluations with them.
- Internal integration among SASE components. Some providers use NFV service chaining to link disparate security modules, using a single management UI to control them, however, connecting this way can reduce performance, complicate management and leave gaps in security.
- Reduce evaluation overhead by keeping detailed product bake-offs to two finalists.